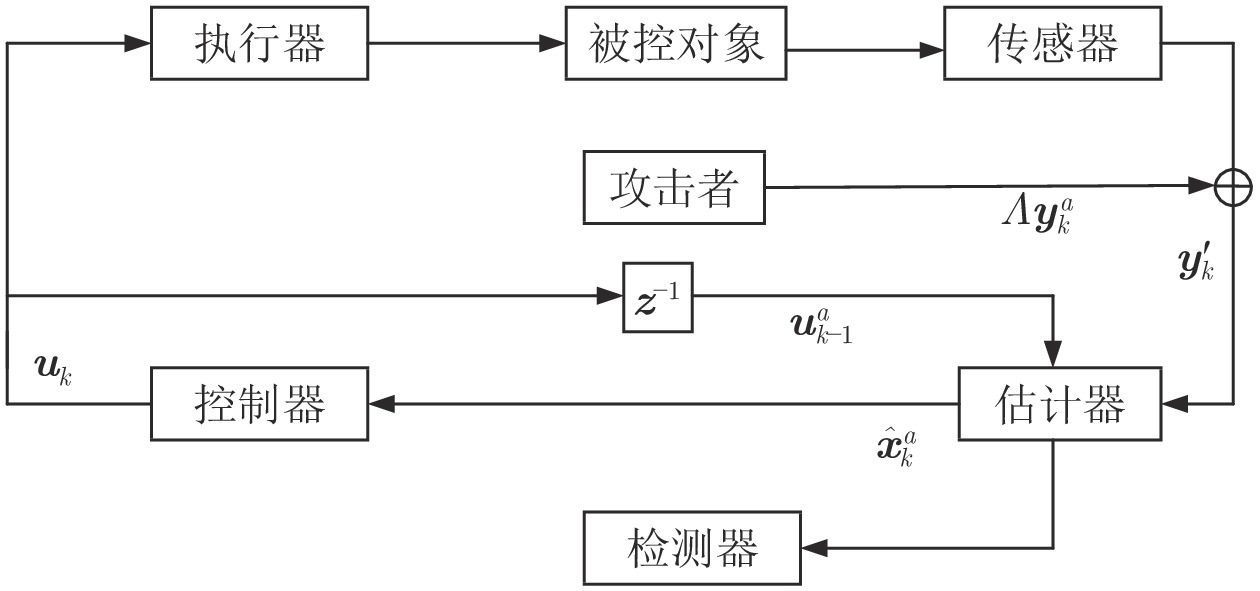
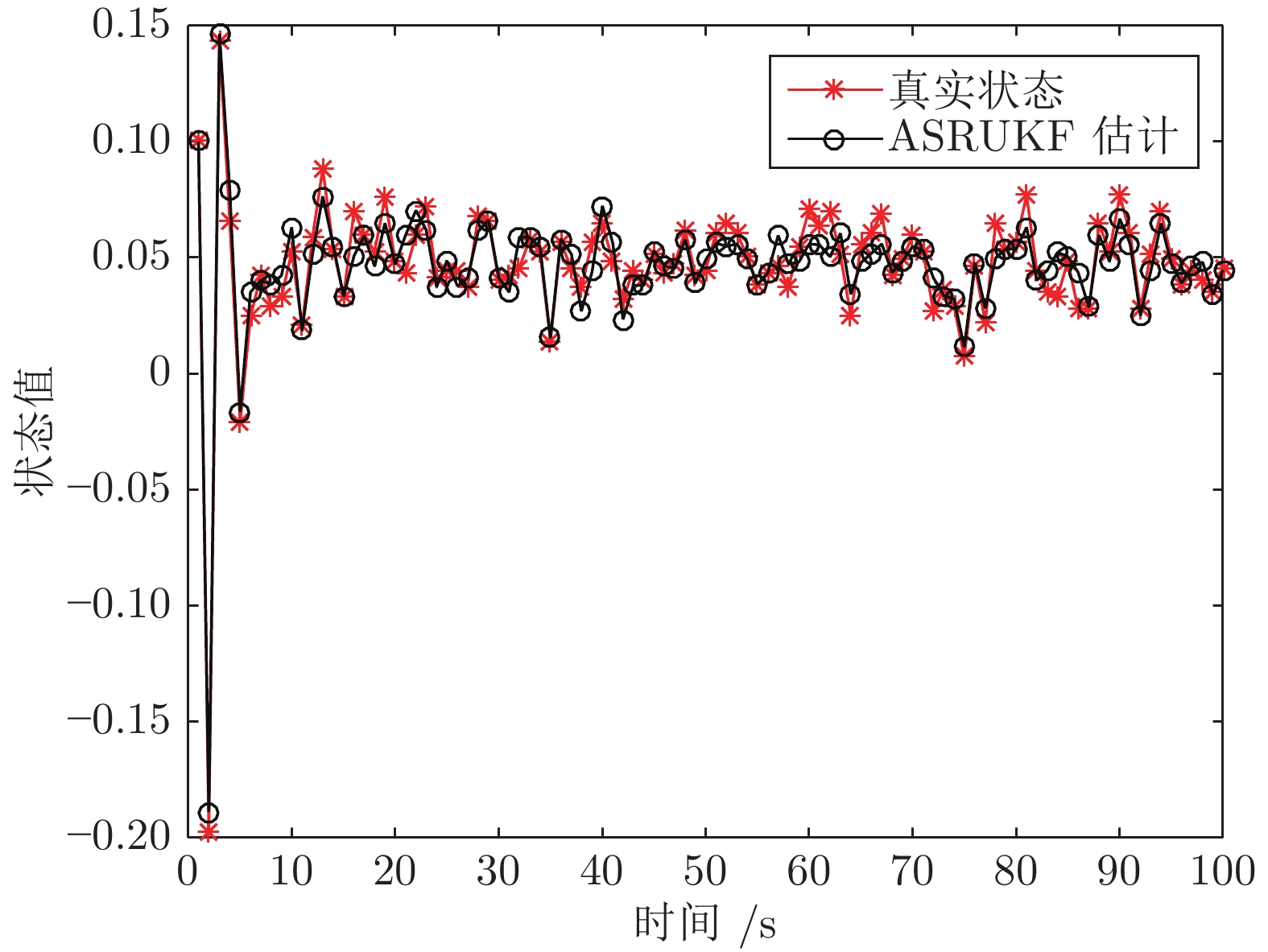
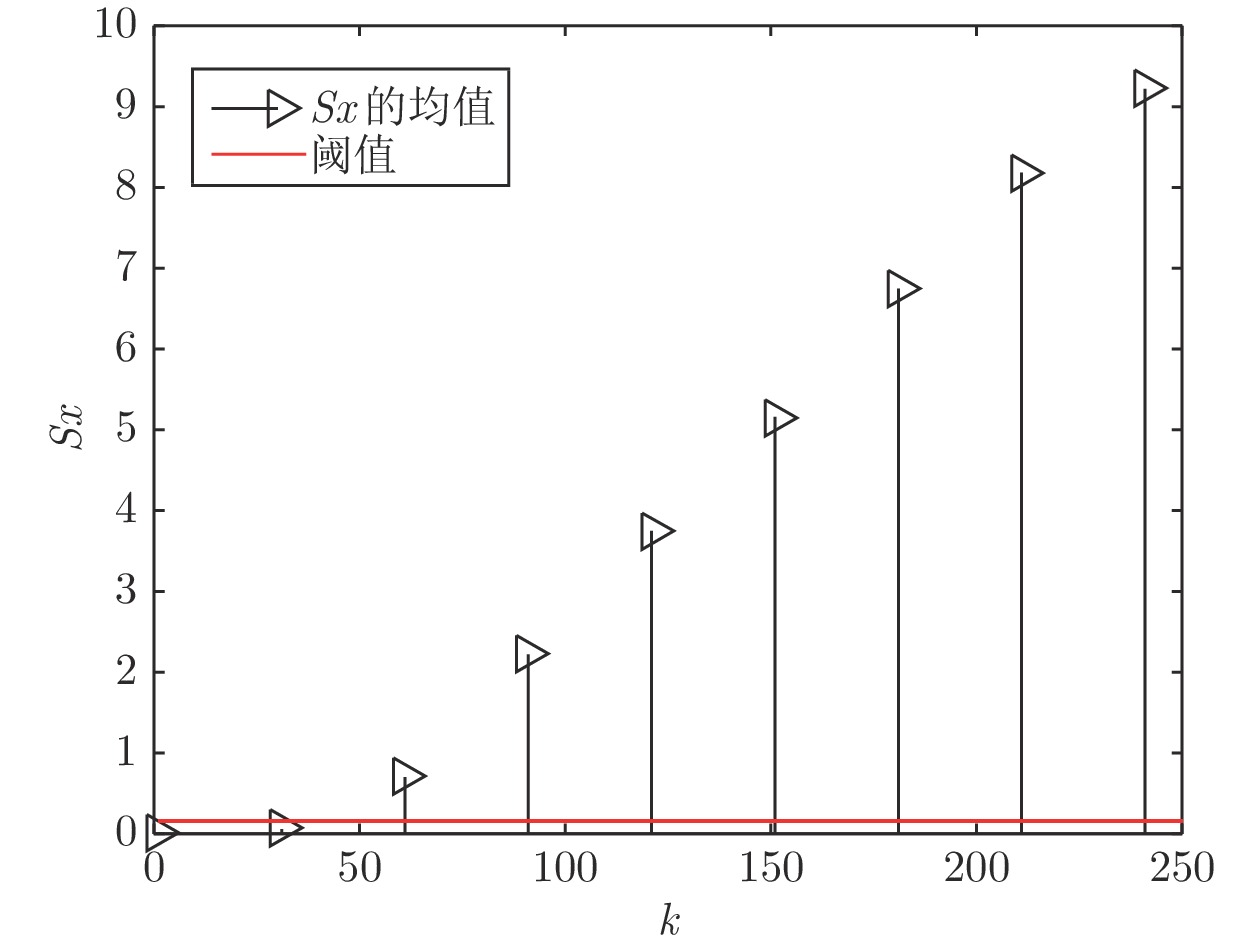
|
[1]
|
彭大天, 董建敏, 蔡忠闽, 张长青, 彭勤科. 假数据注入攻击下信息物理融合系统的稳定性研究. 自动化学报, 2019, 45(1): 196-205.PENG Da-Tian, DONG Jian-Min, CAI Zhong-Min, ZHANG Chang-Qing, PENG Qin-Ke. On the Stability of Cyber-physical Systems Under False Data Injection Attacks. ACTA AUTOMATICA SINICA, 2019, 45(1): 196-205.
|
|
[2]
|
王琦, 邰伟, 汤奕, 倪明. 面向电力信息物理系统的虚假数据注入攻击研究综述. 自动化学报, 2019, 45(1): 72-83.WANG Qi, TAI Wei, TANG Yi, NI Ming. A Review on False Data Injection Attack Toward Cyber-physical Power System. ACTA AUTOMATICA SINICA, 2019, 45(1): 72-83.
|
|
[3]
|
童晓阳, 王晓茹. 乌克兰停电事件引起的网络攻击与电网信息安全防范思考. 电力系统自动化, 2016, 40(7): 144-148.Tong Xiao-Yang, Wang Xiao-Ru. Inferrence and Countermeasure Presuppostion of Network Attack in Incdient on Ukrainian Power Grid. Automation of Electric Power Systems, 2016, 40(7): 144-148.
|
|
[4]
|
Liu Y, Ning P, Reiter M K. False Data Injection Attacks against State Estimation in Electric Power Grids. ACM Transactions on Information and System Security, 2011, 14(1): 1-34.
|
|
[5]
|
Yang C, Yang W, Shi H. DoS attack in centralised sensor network against state estimation. IET Control Theory & Applications, 2018, 12(9): 1244–1253.
|
|
[6]
|
Kurt M N, Yılmaz Y, Wang X D. Secure Distributed Dynamic State Estimation in Wide-Area Smart Grids. IEEE Transactions on Information Forensics and Security, 2020, 15: 800-815. doi: 10.1109/TIFS.2019.2928207
|
|
[7]
|
Weimer J, Kar S, Johansson K H. Distributed detection and isolation of topology attacks in power networks. In: Proceedings of the 1st ACM International Conference on High Confidence Networked Systems, Beijing, China. 2012. 65−71
|
|
[8]
|
Qi J J, Sun K, Wang J H, Liu H. Dynamic State Estimation for Multi-Machine Power System by Unscented Kalman Filter With Enhanced Numerical Stability. IEEE Transactions on smart grid, 2018, 9(2): 1184-1196. doi: 10.1109/TSG.2016.2580584
|
|
[9]
|
Mo Y L, Garone E, Casavola A, Sinopoli B. False data injection attacks against state estimation in wireless sensor networks. In: Proceedings of the 49th IEEE Conference on Decision and Control, Atlanta, USA: IEEE, 2010. 5967−5972
|
|
[10]
|
Mohammadi A, Plataniotis K N. Noncircular. Attacks on Phasor Measurement Units for State Estimation in Smart Grid. IEEE Journal of Selected Topics in Signal Processing, 2018, 12(4): 777-789. doi: 10.1109/JSTSP.2018.2840517
|
|
[11]
|
Manandhar K, Cao X J, Hu F. Detection of Faults and Attacks Including False Data Injection Attack in Smart Grid Using Kalman Filter. IEEE Transactions on Control of Network Systems, 2014, 1(4): 370-379. doi: 10.1109/TCNS.2014.2357531
|
|
[12]
|
Yang Q, Yang J, Yu W, An D, Zhang N, Zhao W. On false data-injection attacks against power system state estimation: modeling and countermeasures. IEEE Transactions on Parallel and Distributed Systems, 2014, 25(3): 717–729. doi: 10.1109/TPDS.2013.92
|
|
[13]
|
梁天添, 王茂. 一类广义连续-离散系统量测丢失情况下鲁棒滤波算法. 中国惯性技术学报, 2018, 26(2): 81-86.LIANG Tian-Tian, WANG Mao. Robust algorithm for a class of sampled-data descriptor systems with missing measurements. Journal of Chinese Inertial Technology, 2018, 26(2): 81-86.
|
|
[14]
|
赵琳, 王小旭, 孙明, 丁继成, 闫超. 基于极大后验估计和指数加权的自适应UKF滤波算法. 自动化学报, 2010, 36(7): 1008-1019.Zhao Lin, WANG Xiao-Xu, SUN Ming, DING Ji-Cheng, YAN Chao. Adaptive UKF Filtering Algorithm Based on Maximum a Posterior Estimation and Exponential Weighting. ACTA AUTOMATICA SINICA, 2010, 36(7): 1008-1019.
|
|
[15]
|
石勇, 韩崇昭. 自适应UKF算法在目标跟踪中的应用. 自动化学报, 2011, 37(6): 755-759.SHI Yong, HAN Chong-Zhao. Adaptive UKF Method with Applications to Target Tracking. ACTA AUTOMATICA SINICA, 2011, 37(6): 755-759.
|
|
[16]
|
Van der Merwe R, Wan E A. The square-root unscented Kalman filter for state and parameter estimation. In: Proceedings of the 2001 International Conference on Acoustics, Speech, and Signal Processing. New York, USA: IEEE, 2001. 3461−3464
|
|
[17]
|
Xiong K, Zhang H Y, Chan C W. Performance Evaluation of UKF-based Nonlinear Filtering. Automatica, 2006, 42(2): 261-270. doi: 10.1016/j.automatica.2005.10.004
|
|
[18]
|
Yu W, Griffith D, Ge L Q, Bhattarai S, Golmie N. An Integrated Detection System against False Data Injection Attacks in the Smart Grid. Security and Communication Networks, 2015, 8(2): 91-109. doi: 10.1002/sec.957
|
|
[19]
|
Hu J, Wang Z D, Gao H J. Recursive Filtering with Random Parameter Matrices, Multiple Fading Measurements and Correlated Noises. Automatica, 2013, 49(11): 3440-3448. doi: 10.1016/j.automatica.2013.08.021
|




 下载:
下载: