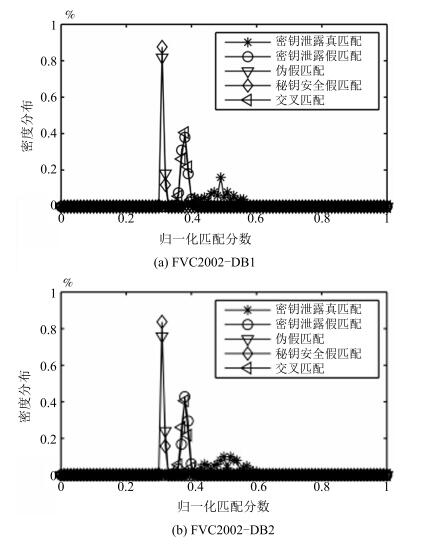
-
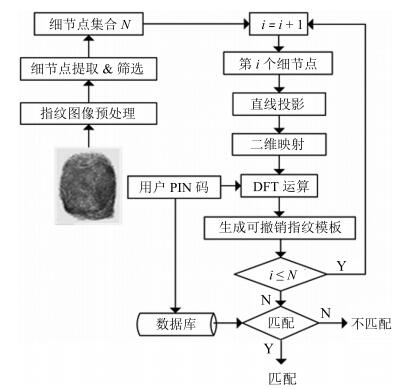
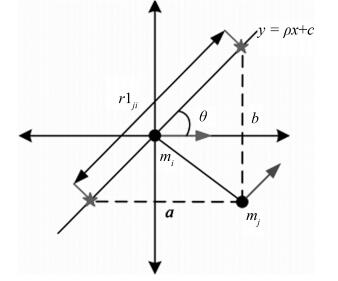
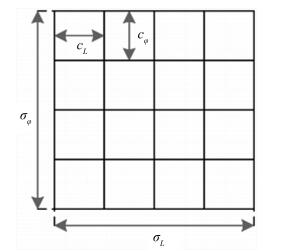
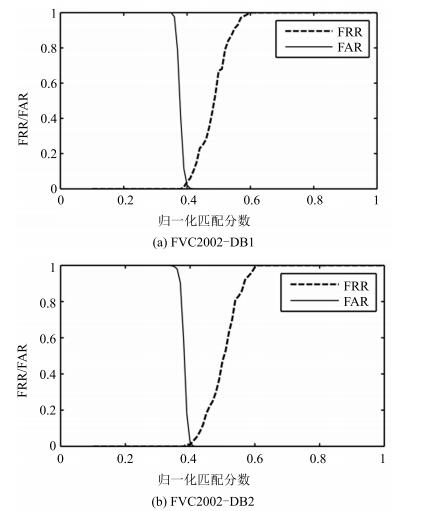
摘要: 为了改善指纹模板保护算法的可撤销性、不可逆性等性能, 设计了一种基于细节点投影的可撤销指纹模板生成算法.首先对指纹图像进行预处理, 提取指纹的细节点特征, 并筛选出采样半径范围内的有效细节点, 然后对细节点进行直线投影, 将投影后的向量映射到二维网格, 生成固定长度的一维比特串, 再结合用户PIN码生成可撤销指纹模板.在指纹数据库FVC2002-DB1和DB2上的实验结果表明, 该算法不仅提高了指纹模板认证的稳定性, 而且在可撤销性、不可逆性和安全性等方面均具有较好性能.Abstract: In order to enhance the revocation and irreversibility performance of the fingerprint template protection algorithm, a cancelable fingerprint template generating algorithm is proposed using minutiae projection. Firstly, we extract fingerprint minutiae feature after preprocessing the fingerprint image and select the effective minutiae within the range of the sampling radius. Next, we project the minutiae into a line and map the projected vectors onto a 2D grid to generate a fixed length 1D bit-string. Finally, the cancelable fingerprint template is generated by combining the user PIN code. Experiments performed on FVC2002-DB1 and DB2 show that the algorithm not only improves the stability of the template authentication but also satisfies revocation as well as non-invertibility, and ensures the security of the algorithm.
-
Key words:
- Minutiae /
- projection /
- sample radius /
- cancelable template
1) 本文责任编委 左旺孟 -
表 1 不同参数的取值范围
Table 1 Parameter settings in the experiments
参数 参数描述 参数范围 $ t\_\min $ 最小采样半径 $ \{ 6, 7, \cdots, 13 \} $ $ t\_\max $ 最大采样半径 $ \{ 100, 110, \cdots, 160 \} $ $ c_{x} $ 网格单元的长 $ \{ 10, 11, \cdots, 15 \} $ $ c_{y} $ 网格单元的宽 $ \{ 8, 9, \cdots, 12 \} $ 表 2 不同参数在FVC2002-DB1下的EER (%)
Table 2 EER of different parameters for FVC2002-DB1 (%)
$ (t\_\min, t\_\max) $ $ (c_{x}, c_{y}) $ PIN码安全 PIN码泄露 (7, 100) (10, 8) 0 3.38 (13, 9) 0 3.63 (9, 120) (12, 9) 0 3.12 (14, 10) 0 3.37 (11, 140) (13, 9) 0 2.56 (13, 10) 0 3.14 (13, 160) (11, 11) 0 3.08 (12, 11) 0 3.18 表 3 采用Pambudi方法和本文算法的性能比较(%)
Table 3 EER comparison between the Pambudi method and proposed method (%)
算法 PIN码安全 PIN码泄露 DB1 DB2 DB1 DB2 Pambudi等[18] $ - $ 1 $ - $ $ - $ 本文算法 0 0 2.5555 1.1565 -
[1] 张宁, 臧亚丽, 田捷.生物特征与密码技术的融合——一种新的安全身份认证方案.密码学报, 2015, 2(2): 159-176 http://d.wanfangdata.com.cn/Periodical/mmxb201502005Zhang Ning, Zang Ya-Li, Tian Jie. The integration of biometrics and cryptography-a new solution for secure identity authentication. Journal of Cryptologic Research, 2015, 2(2): 159-176 http://d.wanfangdata.com.cn/Periodical/mmxb201502005 [2] Rane S, Wang Y, Draper S C, Ishwar P. Secure biometrics: concepts, authentication architectures, and challenges. IEEE Signal Processing Magazine, 2013, 30(5): 51-64 doi: 10.1109/MSP.2013.2261691 [3] Adámek M, Matýsek M, Neumann P. Security of biometric systems. Procedia Engineering, 2015, 100: 169-176 doi: 10.1016/j.proeng.2015.01.355 [4] Juels A, Sudan M. A fuzzy vault scheme. Designs, Codes and Cryptography, 2006, 38(2): 237-257 doi: 10.1007-s10623-005-6343-z/ [5] Kaur G, Singh G, Kumar V. A review on biometric recognition. International Journal of Bio-Science and Bio-Technology, 2014, 6(4): 69-76 doi: 10.14257/ijbsbt.2014.6.4.07 [6] Jin A T B, Ling D N C, Goh A. Biohashing: two factor authentication featuring fingerprint data and tokenised random number. Pattern Recognition, 2004, 37(11): 2245- 2255 doi: 10.1016/j.patcog.2004.04.011 [7] Kong A, Cheung K H, Zhang D, Kamel M, You J. An analysis of BioHashing and its variants. Pattern Recognition, 2006, 39(7): 1359-1368 doi: 10.1016/j.patcog.2005.10.025 [8] Nanni L, Lumini A. Empirical tests on BioHashing. Neurocomputing, 2006, 69(16-18): 2390-2395 doi: 10.1016/j.neucom.2006.05.001 [9] Ratha N K, Chikkerur S, Connell J H, Bolle R M. Generating cancelable fingerprint templates. IEEE Transactions on Pattern Analysis and Machine Intelligence, 2007, 29(4): 561-572 doi: 10.1109/TPAMI.2007.1004 [10] Feng Q, Su F, Cai A N, Zhao F F. Cracking cancelable fingerprint template of Ratha. In: Proceedings of the 2008 International Symposium on Computer Science and Computational Technology. Shanghai, China: IEEE, 2008. 572-575 [11] Lee C, Choi J Y, Toh K A, Lee S, Kim J. Alignment-free cancelable fingerprint templates based on local minutiae information. IEEE Transactions on Systems, Man, and Cybernetics, Part B (Cybernetics), 2007, 37(4): 980-992 doi: 10.1109/TSMCB.2007.896999 [12] Lee C, Kim J. Cancelable fingerprint templates using minutiae-based bit-strings. Journal of Network and Computer Applications, 2010, 33(3): 236-246 http://d.old.wanfangdata.com.cn/NSTLQK/NSTL_QKJJ0218997814/ [13] Ahmad T, Hu J K, Wang S. String-based cancelable fingerprint templates. In: Proceedings of the 6th IEEE Conference on Industrial Electronics and Applications. Beijing, China: IEEE, 2011. 1028-1033 [14] Jin Z, Teoh A B J, Ong T S, Tee C. Fingerprint template protection with minutiae-based bit-string for security and privacy preserving. Expert Systems with Applications, 2012, 39(6): 6157-6167 doi: 10.1016/j.eswa.2011.11.091 [15] Wang S, Hu J K. Alignment-free cancelable fingerprint template design: a densely infinite-to-one mapping (DITOM) approach. Pattern Recognition, 2012, 45(12): 4129-4137 doi: 10.1016/j.patcog.2012.05.004 [16] Wang S, Hu J K. Design of alignment-free cancelable fingerprint templates via curtailed circular convolution. Pattern Recognition, 2014, 47(3): 1321-1329 http://www.wanfangdata.com.cn/details/detail.do?_type=perio&id=7c4c223ba1fa298bf19097d6a7534b11 [17] Sandhya M, Prasad M V N K. K-nearest neighborhood structure (K-NNS) based alignment-free method for fingerprint template protection. In: Proceedings of the 2015 International Conference on Biometrics. Phuket, Thailand: IEEE, 2015. 386-393 [18] Ahmad T, Pambudi D S, Usagawa T. Improving the performance of projection-based cancelable fingerprint template method. In: Proceedings of the 7th International Conference of Soft Computing and Pattern Recognition. Fukuoka, Japan: IEEE, 2016. 84-88 [19] 许秋旺, 张雪锋.基于细节点邻域信息的可撤销指纹模板生成算法.自动化学报, 2017, 43(4): 645-652 doi: 10.16383/j.aas.2017.c160069Xu Qiu-Wang, Zhang Xue-Feng. Generating cancelable fingerprint templates using minutiae local information. Acta Automatica Sinica, 2017, 43(4): 645-652 doi: 10.16383/j.aas.2017.c160069 [20] Ahmad T, Hu J K, Wang S. Pair-polar coordinate-based cancelable fingerprint templates. Pattern Recognition, 2011, 44(10-11): 2555-2564 doi: 10.1016/j.patcog.2011.03.015 [21] Jin Z, Lim M H, Teoh A B J, Goi B M. A non-invertible randomized graph-based hamming embedding for generating cancelable fingerprint template. Pattern Recognition Letters, 2014, 42: 137-147 doi: 10.1016/j.patrec.2014.02.011 -




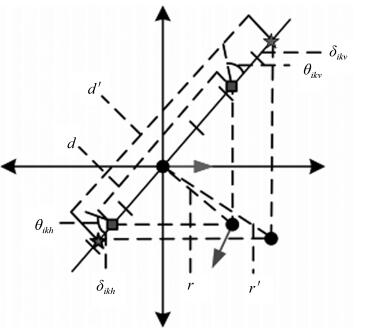
 下载:
下载: