Distributed Secure State Estimation and Control for CPSs Under Sensor Attacks -A Finite Time Approach
-
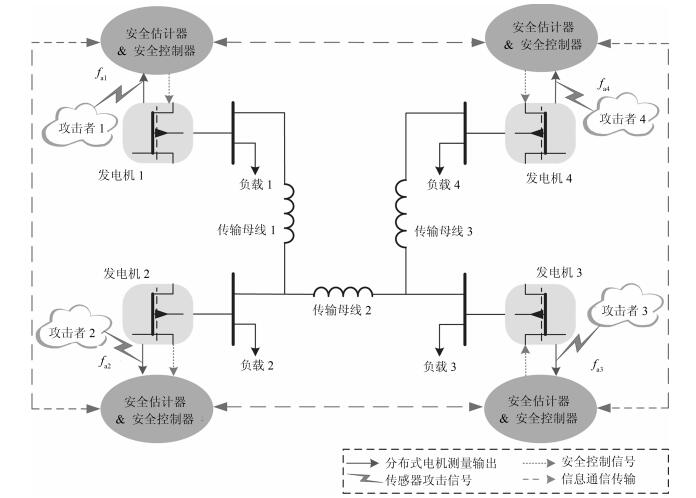
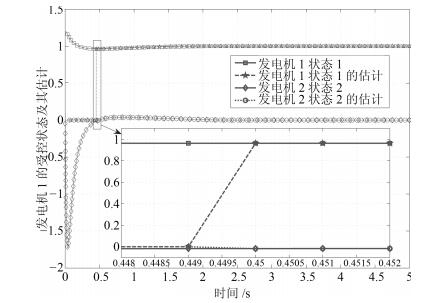
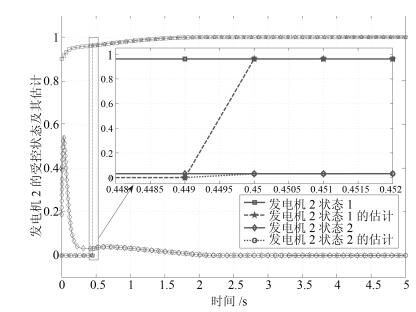
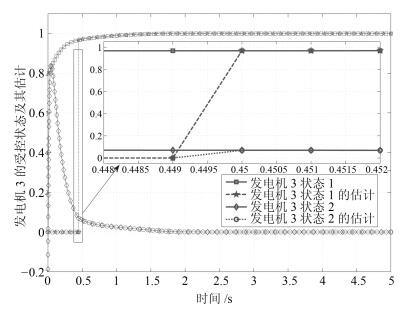
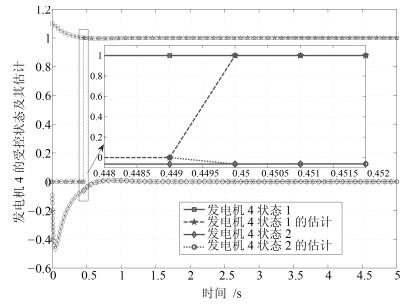
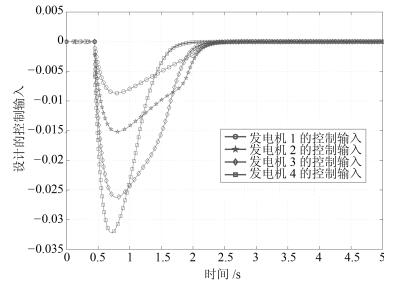
摘要: 研究具有非线性耦合特性信息物理系统(Cyber physical systems,CPS)在被攻击情况下的分布式有限时间状态安全估计和控制问题.首先,提出一种由分布式安全测量预选器和有限时间观测器组成的分布式有限时间状态安全估计策略,可确保系统的状态在预设的有限时间之内被准确估计出来.然后,利用获得的安全状态估计,借助反步设计方法,建立一套分布式有限时间安全控制算法.理论分析表明,该方法可以保证系统能在有限时间内实现对给定信号的跟踪.最后,通过微电网系统仿真验证了所提方法的有效性.Abstract: This paper investigates the problem of distributed secure state estimation and control for nonlinearly coupled interconnected cyber physical systems (CPS) under sensor attacks. Distributed schemes consisting of pre-selectors and observers are presented to solve the secure state estimation problem. Then, with the obtained state estimation and following the backstepping design procedure, distributed secure control algorithms are derived. Theoretical analysis shows that, with the proposed distributed secure observers and controllers, not only the state estimation of the CPS under attacks is obtained in a given finite time, but also the state tracking is ensured in a finite time. Finally, the developed algorithms are applied to an islanded micro-grid system as an illustration, verifying the effectiveness of the proposed method.1) 本文责任编委 刘向杰
-
表 1 微电网系统模型参数
Table 1 Parameters of isolated grids systems
发电机1 发电机2 发电机3 发电机4 模型 $\tau_{Pi}$ 0.016 0.016 0.016 0.016 $k_{Pi}$ 6E-5 3E-5 2E-5 1.5E-5 负载 $P_{1i}$ 0.01 0.01 0.01 0.01 $P_{2i}$ 1 2 3 4 $P_{3i}$ 1E-4 1E-4 1E-4 1E-4 母线 $B_{12}=10 \Omega^{-1}$, $B_{23}=10.67 \Omega^{-1}$, $B_{34}=9.82 \Omega^{-1}$ 参考电气角 $\delta_i ^{d}$=1 (rad) -
[1] Park K J, Zheng R, and Liu X. Cyber-physical systems: Milestones and research challenges. Computer Communications, 2012, 36(1): 1-7 http://d.old.wanfangdata.com.cn/Periodical/jsjyy2013z2001 [2] Conti J P. The day the samba stopped. Engineering & Technology, 2010, 25(4): 46-47 [3] Langner R. Stuxnet: Dissecting a cyberwarfare weapon. IEEE Security & Privacy, 2011, 9(3): 49-51 http://d.old.wanfangdata.com.cn/Periodical/sysyjyts201408030 [4] Pasqualetti F, Dörfler F, and Bullo F. Attack detection and identiflcation in cyber-physical systems. IEEE Transactions on Automatic Control, 2013, 58(11): 2715-2729 doi: 10.1109/TAC.2013.2266831 [5] Ao W, Song Y and Wen C. Adaptive cyber-physical system attack detection and reconstruction with application to power systems. IET Control Theory & Applications, 2016, 10(12): 1458-1468 http://www.wanfangdata.com.cn/details/detail.do?_type=perio&id=52c0111162369eb5d70e0c7dfc1c148e [6] Chen Y, Kar S, and Moura J M. Dynamic attack detection in cyber-physical systems with side initial state information. IEEE Transactions on Automatic Control, 2017, 62(9): 4618-4624 doi: 10.1109/TAC.2016.2626267 [7] Fawzi H, Tabuada P, and Diggavi S. Secure state-estimation for dynamical systems under active adversaries. In: Proceeding of Forty-Ninth Annual Allerton Conference. Monticello, USA: IEEE, 2011. 337-344 [8] Fawzi H, Tabuada P, and Diggavi S. Secure estimation and control for cyber-physical systems under adversarial attacks. IEEE Transactions on Automatic Control, 2014, 59(6): 1454-1467 doi: 10.1109/TAC.2014.2303233 [9] Shoukry Y and Tabuada P. Event-triggered state observers for sparse sensor noise/attacks. IEEE Transactions on Automatic Control, 2016, 61(8): 2079-2091 doi: 10.1109/TAC.2015.2492159 [10] Shoukry Y, Chong M, Wakaiki M, Nuzzo P, Sangiovanni-Vincentelli A L, Seshia S A, Hespanha J P and Tabuada P. Smt-based observer design for cyber-physical systems under sensor attacks, In: Proceeding of 7th ACM/IEEE International Conference on Cyber-Physical Systems (ICCPS). IEEE Computer Society, 2016. 1-10 [11] Ao W, Song Y, Wen C, and Lai J. Finite time attack detection and supervised secure state estimation for CPSs with malicious adversaries. Information Sciences, 2018, 451-452: 67-82 doi: 10.1016/j.ins.2018.03.056 [12] Ao W, Song Y and Wen C. Distributed secure state estimation and control for CPSs under sensor attacks. IEEE Transactions on Cybernatics, 2018, DOI: 10.1109/TCYB.2018.2868781 [13] Wang Y, Song Y, Gao H and Lewis F L. Distributed fault-tolerant control of virtually and physically interconnected systems with application to high-speed trains under traction/braking failures. IEEE Transactions on Intelligent Transportation Systems, 2016, 17(2): 535-545 doi: 10.1109/TITS.2015.2479922 [14] Mo Y, Hespanha J P, and Sinopoli B. Resilient detection in the presence of integrity attacks. IEEE Transactions on Signal Processing, 2014, 62(1): 31-43 doi: 10.1109/TSP.2013.2284145 [15] Mo Y and Sinopoli B. Secure estimation in the presence of integrity attacks. IEEE Transactions on Automatic Control, 2015, 60(4): 1145-1151 doi: 10.1109/TAC.2014.2350231 [16] Engel R and Kreisselmeier G. A continuous-time observer which converges in flnite time. IEEE Transactions on Automatic Control, 2002, 47(7): 1202-1204 doi: 10.1109/TAC.2002.800673 [17] Li S, Sun H, Yang J, and Yu X. Continuous flnite-time output regulation for disturbed systems under mismatching condition. IEEE Transactions on Automatic Control, 2015, 60(1): 277-282 doi: 10.1109/TAC.2014.2324212 [18] Guo F, Wen C, Mao J and Song Y. Distributed secondary voltage and frequency restoration control of droopcontrolled inverter-based microgrids. IEEE Transactions on Industrial Electronics, 2015, 62(7): 4355-4364 doi: 10.1109/TIE.2014.2379211 -





 下载:
下载: