-
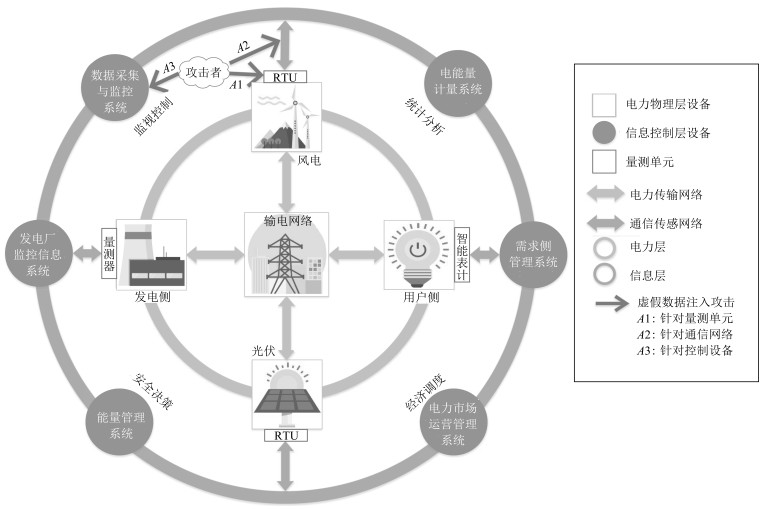
摘要: 随着电力信息通信技术的发展与应用,电力流与信息流深度融合,共同实现对系统的全景状态感知与控制决策,电力系统转变成典型的信息物理系统(Cyber physical system,CPS).开放的通信环境与复杂的信息物理耦合交互过程,使得信息安全风险成为影响电力系统安全稳定运行的重要因素.其中,虚假数据注入攻击(False data injection attack,FDIA)通过破坏网络数据完整性以干扰控制决策,是一种典型的网络攻击方式.本文针对面向电力CPS的虚假数据注入的攻击过程和防御手段进行了分析与总结.从攻击者视角分析了FDIA的攻击目标、策略及后果;从防御者视角总结了保护与检测环节中的各类方法;最后基于联合仿真技术,提出了针对虚假数据攻防过程建模和评估的电力CPS联合攻防平台.Abstract: With the development and application of information communication technology, the power flow and the information flow are becoming deeply integrated in order to achieve panoramic state awareness and control decision. Therefore the power system has been transformed into a typical cyber-physical system (CPS). Considering the open communication environment and complex cyber physical coupling mechanism, the information risk has become an important issue posing severe threats to the secure operation of power systems. False data injection attack (FDIA), as a typical attack mode destroying data integrity, can interfere with the control decision. In this paper, the attack process and defense method of false data injection are analyzed and summarized. Firstly, from the perspective of attackers, the goals, strategies and consequences of FDIA are comprehensively discussed. Then, from the perspective of defenders, the protection and detection countermeasures are discussed. Finally the co-simulation technology is utilized to construct associated attack-defense platform of cyber-physical power system (CPPS), which is aimed at modeling and assessment of the attack and defense processes of false data injection.1) 本文责任编委 孙秋野
-
表 1 电力CPS网络安全攻防平台研究现状
Table 1 Researches of CPPS associated attack-defense platforms
组成结构 攻击场景 防御方法 验证效果 MATLAB, OPNET[60] 信息传输故障 基于多维尺度和局部异常因子的检测方法 实现CPS各区域故障的统一识别与定位 Digsilent, OMNET++, MATLAB[61] 针对EMS的FDIA 检测和事后恢复方法 构建了脆弱性和攻击影响的综合评估框架 PSLF, NS2[62] 针对PMU状态估计器的FDIA 基于状态变量时效性的检测方法 验证了状态估计器对单链路和路由器故障、拥塞的鲁棒性 MATLAB, OPNET, C++[63] 针对广域阻尼控制系统的拒绝服务、中间人等攻击 无 分析归纳了延迟、无序、错误数据的端到端信息特征 Simulink, OPNET[64] 目的为延迟和污染通信数据的分布式拒绝服务攻击 无 观察了网络攻击对故障附近发电机响应的影响 RTDS, Python, AutoIt[65] 面向广域监控系统应用的电力CPS突发事件和网络攻击行为 基于数据挖掘的入侵异常检测方法 验证了电力系统应对攻击的脆弱性评估、异常检测与故障检测能力 -
[1] 赵俊华, 文福拴, 薛禹胜, 李雪, 董朝阳.电力CPS的架构及其实现技术与挑战.电力系统自动化, 2010, 34(16):1-7 http://d.old.wanfangdata.com.cn/Periodical/dlxtzdh201016001Zhao Jun-Hua, Wen Fu-Shuan, Xue Yu-Sheng, Li Xue, Dong Zhao-Yang.Cyber physical power systems:architecture, implementation techniques and challenges.Automation of Electric Power Systems, 2010, 34(16):1-7 http://d.old.wanfangdata.com.cn/Periodical/dlxtzdh201016001 [2] 马钊, 周孝信, 尚宇炜, 盛万兴.能源互联网概念、关键技术及发展模式探索.电网技术, 2015, 39(11):3014-3022 http://d.old.wanfangdata.com.cn/Periodical/dwjs201511003Ma Zhao, Zhou Xiao-Xin, Shang Yu-Wei, Sheng Wan-Xing.Exploring the concept, key technologies and development model of energy internet.Power System Technology, 2015, 39(11):3014-3022 http://d.old.wanfangdata.com.cn/Periodical/dwjs201511003 [3] Mo Y L, Kim T H J, Brancik K, Dickinson D, Lee H, Perrig A, et al.Cyber-physical security of a smart grid infrastructure.Proceedings of the IEEE, 2012, 100(1):195-209 doi: 10.1109/JPROC.2011.2161428 [4] He H B, Yan J.Cyber-physical attacks and defences in the smart grid:a survey.IET Cyber-Physical Systems:Theory and Applications, 2016, 1(1):13-27 doi: 10.1049/iet-cps.2016.0019 [5] 刘东, 盛万兴, 王云, 陆一鸣, 孙辰.电网信息物理系统的关键技术及其进展.中国电机工程学报, 2015, 35(14):3522-3531 http://d.old.wanfangdata.com.cn/Periodical/zgdjgcxb201514007Liu Dong, Sheng Wan-Xing, Wang Yun, Lu Yi-Ming, Sun Chen.Key technologies and trends of cyber physical system for power grid.Proceedings of the CSEE, 2015, 35(14):3522-3531 http://d.old.wanfangdata.com.cn/Periodical/zgdjgcxb201514007 [6] Vellaithurai C, Srivastava A, Zonouz S, Berthier R.CPIndex:cyber-physical vulnerability assessment for power-grid infrastructures.IEEE Transactions on Smart Grid, 2015, 6(2):566-575 doi: 10.1109/TSG.2014.2372315 [7] Wang W Y, Lu Z.Cyber security in the smart grid:survey and challenges.Computer Networks, 2013, 57(5):13441371 doi: 10.1016/j.comnet.2012.12.017 [8] 苗新, 张恺, 田世明, 李建歧, 殷树刚, 赵子岩.支撑智能电网的信息通信体系.电网技术, 2009, 33(17):8-13 http://d.old.wanfangdata.com.cn/Periodical/zgsjtx201516019Miao Xin, Zhang Kai, Tian Shi-Ming, Li Jian-Qi, Yin Shu-Gang, Zhao Zi-Yan.Information communication system supporting smart grid.Power System Technology, 2009, 33(17):8-13 http://d.old.wanfangdata.com.cn/Periodical/zgsjtx201516019 [9] Liu S, Mashayekh S, Kundur D, Zourntos T, Butler-Purry K.A framework for modeling cyber-physical switching attacks in smart grid.IEEE Transactions on Emerging Topics in Computing, 2013, 1(2):273-285 doi: 10.1109/TETC.2013.2296440 [10] 叶夏明, 文福拴, 尚金成, 何洋.电力系统中信息物理安全风险传播机制.电网技术, 2015, 39(11):3072-3079 http://d.old.wanfangdata.com.cn/Periodical/dwjs201511012Ye Xia-Ming, Wen Fu-Shuan, Shang Jin-Cheng, He Yang.Propagation mechanism of cyber physical security risks in power systems.Power System Technology, 2015, 39(11):3072-3079 http://d.old.wanfangdata.com.cn/Periodical/dwjs201511012 [11] Hahn A, Govindarasu M.Cyber attack exposure evaluation framework for the smart grid.IEEE Transactions on Smart Grid, 2011, 2(4):835-843 doi: 10.1109/TSG.2011.2163829 [12] 田继伟, 王布宏, 李夏.智能电网状态维持拓扑攻击及其对经济运行的影响.电力系统保护与控制, 2018, 46(1):50-56 http://d.old.wanfangdata.com.cn/Periodical/jdq201801008Tian Ji-Wei, Wang Bu-Hong, Li Xia.State-preserving topology attacks and its impact on economic operation of smart grid.Power System Protection and Control, 2018, 46(1):50-56 http://d.old.wanfangdata.com.cn/Periodical/jdq201801008 [13] 汤奕, 陈倩, 李梦雅, 王琦, 倪明, 梁云.电力信息物理融合系统环境中的网络攻击研究综述.电力系统自动化, 2016, 40(17):59-69 http://d.old.wanfangdata.com.cn/Periodical/dlxtzdh201617009Tang Yi, Chen Qian, Li Meng-Ya, Wang Qi, Ni Ming, Liang Yun.Overview on cyber-attacks against cyber physical power system.Automation of Electric Power Systems, 2016, 40(17):59-69 http://d.old.wanfangdata.com.cn/Periodical/dlxtzdh201617009 [14] Liang G Q, Weller S R, Zhao J H, Luo F J, Dong Z Y.The 2015 Ukraine blackout:implications for false data injection attacks.IEEE Transactions on Power Systems, 2017, 32(4):3317-3318 doi: 10.1109/TPWRS.2016.2631891 [15] 李中伟, 佟为明, 金显吉.智能电网信息安全防御体系与信息安全测试系统构建:乌克兰和以色列国家电网遭受网络攻击事件的思考与启示.电力系统自动化, 2016, 40(8):147-151 http://d.old.wanfangdata.com.cn/Periodical/dlxtzdh201608022Li Zhong-Wei, Tong Wei-Ming, Jin Xian-Ji.Construction of cyber security defense hierarchy and cyber security testing system of smart grid:thinking and enlightenment for network attack events to national power grid of Ukraine and Israel.Automation of Electric Power Systems, 2016, 40(8):147-151 http://d.old.wanfangdata.com.cn/Periodical/dlxtzdh201608022 [16] 赵俊华, 梁高琪, 文福拴, 董朝阳.乌克兰事件的启示:防范针对电网的虚假数据注入攻击.电力系统自动化, 2016, 40(7):149-151 http://d.old.wanfangdata.com.cn/Periodical/dlxtzdh201607022Zhao Jun-Hua, Liang Gao-Qi, Wen Fu-Shuan, Dong Zhao-Yang.Lessons learnt from Ukrainian blackout:protecting power grids against false data injection attacks.Automation of Electric Power Systems, 2016, 40(7):149-151 http://d.old.wanfangdata.com.cn/Periodical/dlxtzdh201607022 [17] 倪明, 颜诘, 柏瑞, 汤奕.电力系统防恶意信息攻击的思考.电力系统自动化, 2016, 40(5):148-151 http://d.old.wanfangdata.com.cn/Periodical/dlxtzdh201605023Ni Ming, Yan Jie, Bo Rui, Tang Yi.Power system cyber attack and its defense.Automation of Electric Power Systems, 2016, 40(5):148-151 http://d.old.wanfangdata.com.cn/Periodical/dlxtzdh201605023 [18] 卫志农, 陈和升, 倪明, 孙国强, 孙永辉, 厉超.电力信息物理系统中恶性数据定义、构建与防御挑战.电力系统自动化, 2016, 40(17):70-78 http://d.old.wanfangdata.com.cn/Periodical/dlxtzdh201617010Wei Zhi-Nong, Chen He-Sheng, Ni Ming, Sun Guo-Qiang, Sun Yong-Hui, Li Chao.Definition, construction and defense of false data in cyber physical system.Automation of Electric Power Systems, 2016, 40(17):70-78 http://d.old.wanfangdata.com.cn/Periodical/dlxtzdh201617010 [19] 汤奕, 王琦, 倪明, 梁云.电力信息物理融合系统中的网络攻击分析.电力系统自动化, 2016, 40(6):148-151 http://d.old.wanfangdata.com.cn/Periodical/dlxtzdh201606024Tang Yi, Wang Qi, Ni Ming, Liang Yun.Analysis of cyber attacks in cyber physical power system.Automation of Electric Power Systems, 2016, 40(6):148-151 http://d.old.wanfangdata.com.cn/Periodical/dlxtzdh201606024 [20] 朱杰, 张葛祥, 王涛, 赵俊博.电力系统状态估计欺诈性数据攻击及防御综述.电网技术, 2016, 40(8):2406-2415 http://www.cnki.com.cn/Article/CJFDTOTAL-DWJS201608026.htmZhu Jie, Zhang Ge-Xiang, Wang Tao, Zhao Jun-Bo.Overview of fraudulent data attack on power system state estimation and defense mechanism.Power System Technology, 2016, 40(8):2406-2415 http://www.cnki.com.cn/Article/CJFDTOTAL-DWJS201608026.htm [21] Fan Y W, Zhang Z H, Trinkle M, Dimitrovski A D, Song J B, Li H S.A cross-layer defense mechanism against GPS spoofing attacks on PMUs in smart Grids.IEEE Transactions on Smart Grid, 2015, 6(6):2659-2668 doi: 10.1109/TSG.2014.2346088 [22] Liu X X, Zhu P D, Zhang Y, Chen K.A collaborative intrusion detection mechanism against false data injection attack in advanced metering infrastructure.IEEE Transactions on Smart Grid, 2015, 6(5):2435-2443 doi: 10.1109/TSG.2015.2418280 [23] Bishop A N, Savkin A V.On false-data attacks in robust multi-sensor-based estimation.In:Proceedings of the 9th IEEE International Conference on Control and Automation.Santiago, Chile:IEEE, 2011.10-17 [24] Pal S, Sikdar B, Chow J H.An online mechanism for detection of gray-hole attacks on PMU data.IEEE Transactions on Smart Grid, 2018, 9(4):2498-2507 doi: 10.1109/TSG.2016.2614327 [25] 冀星沛, 王波, 董朝阳, 陈果, 刘涤尘, 魏大千, 等.电力信息-物理相互依存网络脆弱性评估及加边保护策略.电网技术, 2016, 40(6):1867-1873 http://www.cnki.com.cn/Article/CJFDTotal-DWJS201606042.htmJi Xing-Pei, Wang Bo, Dong Zhao-Yang, Chen Guo, Liu Di-Chen, Wei Da-Qian, et al.Vulnerability evaluation and link addition protection strategy research of electrical cyber-physical interdependent networks.Power System Technology, 2016, 40(6):1867-1873 http://www.cnki.com.cn/Article/CJFDTotal-DWJS201606042.htm [26] 李强, 周京阳, 于尔铿, 刘树春, 王磊.基于混合量测的电力系统状态估计混合算法.电力系统自动化, 2005, 29(19):31-35 doi: 10.3321/j.issn:1000-1026.2005.19.006Li Qiang, Zhou Jing-Yang, Yu Er-Keng, Liu Shu-Chun, Wang Lei.Hybrid algorithm for power system state estimation based on PMU measurement and SCADA measurement.Automation of Electric Power Systems, 2005, 29(19):31-35 doi: 10.3321/j.issn:1000-1026.2005.19.006 [27] Mo Y L, Sinopoli B.False data injection attacks in control systems.In:Proceedings of the 1st Workshop on Secure Control Systems.Stockholm, Sweden:Springer, 2010. [28] 王宇飞, 高昆仑, 赵婷, 邱健.基于改进攻击图的电力信息物理系统跨空间连锁故障危害评估.中国电机工程学报, 2016, 36(6):1490-1499 http://www.cnki.com.cn/Article/CJFDTOTAL-ZGDC201606005.htmWang Yu-Fei, Gao Kun-Lun, Zhao Ting, Qiu Jian.Assessing the harmfulness of cascading failures across space in electric cyber-physical system based on improved attack graph.Proceedings of the CSEE, 2016, 36(6):1490-1499 http://www.cnki.com.cn/Article/CJFDTOTAL-ZGDC201606005.htm [29] 田猛, 王先培, 董政呈, 朱国威, 代荡荡, 赵乐.基于拉格朗日乘子法的虚假数据攻击策略.电力系统自动化, 2017, 41(11):26-32 doi: 10.7500/AEPS20161225004Tian Meng, Wang Xian-Pei, Dong Zheng-Cheng, Zhu Guo-Wei, Dai Dang-Dang, Zhao Le.Injected attack strategy for false data based on Lagrange multipliers method.Automation of Electric Power Systems, 2017, 41(11):26-32 doi: 10.7500/AEPS20161225004 [30] 苏盛, 吴长江, 马钧, 曾祥君.基于攻击方视角的电力CPS网络攻击模式分析.电网技术, 2014, 38(11):3115-3120 http://d.old.wanfangdata.com.cn/Periodical/dwjs201411026Su Sheng, Wu Chang-Jiang, Ma Jun, Zeng Xiang-Jun.Attacker's perspective based analysis on cyber attack mode to cyber-physical system.Power System Technology, 2014, 38(11):3115-3120 http://d.old.wanfangdata.com.cn/Periodical/dwjs201411026 [31] 朱泽磊, 周京阳, 潘毅, 闫翠会, 崔晖, 李伟刚.考虑电力电量平衡的安全约束经济调度.中国电机工程学报, 2013, 33(10):168-176 http://d.old.wanfangdata.com.cn/Periodical/zgdjgcxb201310022Zhu Ze-Lei, Zhou Jing-Yang, Pan Yi, Yan Cui-Hui, Cui Hui, Li Wei-Gang.Security constrained economic dispatch considering balance of electric power and energy.Proceedings of the CSEE, 2013, 33(10):168-176 http://d.old.wanfangdata.com.cn/Periodical/zgdjgcxb201310022 [32] Xie L, Mo Y L, Sinopoli B.Integrity data attacks in power market operations.IEEE Transactions on Smart Grid, 2011, 2(4):659-666 doi: 10.1109/TSG.2011.2161892 [33] Jia L Y, Kim J, Thomas R J, Tong L.Impact of data quality on real-time locational marginal price.IEEE Transactions on Power Systems, 2014, 29(2):627-636 doi: 10.1109/TPWRS.59 [34] Mousavian S, Valenzuela J, Wang J H.A probabilistic risk mitigation model for cyber-attacks to PMU networks.IEEE Transactions on Power Systems, 2015, 30(1):156-165 doi: 10.1109/TPWRS.2014.2320230 [35] Zhao J B, Zhang G X, La Scala M, Wang Z Y.Enhanced robustness of state estimator to bad data processing through multi-innovation analysis.IEEE Transactions on Industrial Informatics, 2017, 13(4):1610-1619 doi: 10.1109/TII.2016.2626782 [36] 王先培, 朱国威, 贺瑞娟, 田猛, 董政呈, 代荡荡, 等.复杂网络理论在电力CPS连锁故障研究中的应用综述.电网技术, 2017, 41(9):2947-2956 http://www.wanfangdata.com.cn/details/detail.do?_type=perio&id=QKC20172017091300081478Wang Xian-Pei, Zhu Guo-Wei, He Rui-Juan, Tian Meng, Dong Zheng-Cheng, Dai Dang-Dang, et al.Survey of cascading failures in cyber physical power system based on complex network theory.Power System Technology, 2017, 41(9):2947-2956 http://www.wanfangdata.com.cn/details/detail.do?_type=perio&id=QKC20172017091300081478 [37] Liu R, Vellaithurai C, Biswas S S, Gamage T T, Srivastava A K.Analyzing the cyber-physical impact of cyber events on the power grid.IEEE Transactions on Smart Grid, 2015, 6(5):2444-2453 doi: 10.1109/TSG.2015.2432013 [38] Deng R L, Zhuang P, Liang H.CCPA:coordinated cyber-physical attacks and countermeasures in smart grid.IEEE Transactions on Smart Grid, 2017, 8(5):2420-2430 doi: 10.1109/TSG.2017.2702125 [39] Bo Z Q, Lin X N, Wang Q P, Yi Y H, Zhou F Q.Developments of power system protection and control.Protection and Control of Modern Power Systems, 2016, 1:Article No.7 doi: 10.1186/s41601-016-0012-2 [40] Smart Grid Interoperability Panel Cyber Security Working Group.Introduction to NISTIR 7628 Guidelines for Smart Grid Cyber Security.Technical Standard, NIST Special Publication, 2010, 154 [41] Hu Z S, Wang Y, Tian X X, Yang X L, Meng D J, Fan R S.False data injection attacks identification for smart grids.In:Proceedings of the 3rd International Conference on Technological Advances in Electrical, Electronics and Computer Engineering.Beirut, Lebanon:IEEE, 2015.139-143 [42] Bobba R B, Rogers K M, Wang Q Y, Khurana H, Nahrstedt K, Overbye T J.Detecting false data injection attacks on DC state estimation.In:Proceedings of the 1st Workshop on Secure Control Systems.Urbana-Champaign, USA, 2010.1-9 [43] Chakhchoukh Y, Ishii H.Enhancing robustness to cyber-attacks in power systems through multiple least trimmed squares state estimations.IEEE Transactions on Power Systems, 2016, 31(6):4395-4405 doi: 10.1109/TPWRS.2015.2503736 [44] Gu Y, Liu T, Wang D, Guan X H, Xu Z B.Bad data detection method for smart grids based on distributed state estimation.In:Proceedings of the 2013 IEEE International Conference on Communications.Budapest, Hungary:IEEE, 2013.4483-4487 [45] Wang D, Guan X H, Liu T, Gu Y, Shen C, Xu Z B.Extended distributed state estimation:a detection method against tolerable false data injection attacks in smart grids.Energies, 2014, 7(3):1517-1538 doi: 10.3390/en7031517 [46] Zhao J B, Zhang G X, La Scala M, Dong Z Y, Chen C, Wang J H.Short-term state forecasting-aided method for detection of smart grid general false data injection attacks.IEEE Transactions on Smart Grid, 2017, 8(4):1580-1590 doi: 10.1109/TSG.2015.2492827 [47] Li S, Yilmaz Y, Wang X D.Quickest detection of false data injection attack in wide-area smart grids.IEEE Transactions on Smart Grid, 2015, 6(6):2725-2735 doi: 10.1109/TSG.2014.2374577 [48] Khalid H M, Peng J C H.Immunity toward data-injection attacks using multisensor track fusion-based model prediction.IEEE Transactions on Smart Grid, 2017, 8(2):697707 http://www.wanfangdata.com.cn/details/detail.do?_type=perio&id=08222785e4546cb340e870dcf1295755 [49] He Y B, Mendis G J, Wei J.Real-time detection of false data injection attacks in smart grid:a deep learning-based intelligent mechanism.IEEE Transactions on Smart Grid, 2017, 8(5):2505-2516 doi: 10.1109/TSG.2017.2703842 [50] Ozay M, Esnaola I, Tunay F, Vural Y, Kulkarni S R, Poor H V.Machine learning methods for attack detection in the smart grid.IEEE Transactions on Neural Networks and Learning Systems, 2016, 27(8):1773-1786 doi: 10.1109/TNNLS.2015.2404803 [51] Liu X, Li Z, Member S, Li Z, Member S.Optimal protection strategy against false data injection attacks in power systems.IEEE Transactions on Smart Grid, 2017, 8(4):18021810 doi: 10.1109/TSG.2015.2508449 [52] Mishra S, Li X, Pan T Y, Kuhnle A, Thai M T, Seo J.Price modification attack and protection scheme in smart grid.IEEE Transactions on Smart Grid, 2017, 8(4):1864-1875 doi: 10.1109/TSG.2015.2509945 [53] Sanjab A, Saad W.Data injection attacks on smart grids with multiple adversaries:a game-theoretic perspective.IEEE Transactions on Smart Grid, 2016, 7(4):2038-2049 doi: 10.1109/TSG.2016.2550218 [54] Wei L F, Sarwat A I, Saad W, Biswas S.Stochastic games for power grid protection against coordinated cyber-physical attacks.IEEE Transactions on Smart Grid, 2018, 9(2):684694 doi: 10.1109/TSG.2016.2561266 [55] Ma C Y T, Yau D K Y, Lou X, Rao N S V.Markov game analysis for attack-defense of power networks under possible misinformation.IEEE Transactions on Power Systems, 2013, 28(2):1676-1686 doi: 10.1109/TPWRS.2012.2226480 [56] Wang C, Hou Y H, Ten C W.Determination of Nash Equilibrium based on plausible attack-defense dynamics.IEEE Transactions on Power Systems, 2017, 32(5):3670-3680 doi: 10.1109/TPWRS.2016.2635156 [57] 汤奕, 王琦, 邰伟, 陈彬, 倪明.基于OPAL-RT和OPNET的电力信息物理系统实时仿真.电力系统自动化, 2016, 40(23):1521, 92 doi: 10.7500/AEPS20160515020Tang Yi, Wang Qi, Tai Wei, Chen Bin, Ni Ming.Real-time simulation of cyber-physical power system based on OPAL-RT and OPNET.Automation of Electric Power Systems, 2016, 40(23):15-21, 92 doi: 10.7500/AEPS20160515020 [58] 王云, 刘东, 翁嘉明, 严光升, 雍军, 戴晖.电网信息物理系统建模与仿真验证平台研究.中国电机工程学报, 2018, 38(1):130-136 http://epub.cnki.net/grid2008/detail.aspx?filename=ZGDC201801012&dbname=DKFX2018Wang Yun, Liu Dong, Weng Jia-Ming, Yan Guang-Sheng, Yong Jun, Dai Hui.The research of power CPS modeling and simulation verification platform.Proceedings of the CSEE, 2018, 38(1):130-136 http://epub.cnki.net/grid2008/detail.aspx?filename=ZGDC201801012&dbname=DKFX2018 [59] 李霞, 李勇, 曹一家, 施星宇.基于信息物理系统融合的广域互联电网阻尼控制策略.电力系统保护与控制, 2017, 45(21):35-42 doi: 10.7667/PSPC161610Li Xia, Li Yong, Cao Yi-Jia, Shi Xing-Yu.Wide-area damping control strategy of interconnected power grid based on cyber physical system.Power System Protection and Control, 2017, 45(21):35-42 doi: 10.7667/PSPC161610 [60] 张志鹏, 李勇, 曹一家, 施星宇, 胡伟, 赵庆周.通信和电网联合仿真的配电网局部异常因子故障辨识算法.电力系统自动化, 2016, 40(17):44-50 http://d.old.wanfangdata.com.cn/Periodical/dlxtzdh201617007Zhang Zhi-Peng, Li Yong, Cao Yi-Jia, Shi Xing-Yu, Hu Wei, Zhao Qing-Zhou.A local outlier factor fault identification algorithm based on the co-simulation between cyber and power system for distribution network.Automation of Electric Power Systems, 2016, 40(17):44-50 http://d.old.wanfangdata.com.cn/Periodical/dlxtzdh201617007 [61] Pan K K, Teixeira A, López C D, Palensky P.Co-simulation for cyber security analysis:data attacks against energy management system.In:Proceedings of the 2007 IEEE International Conference on Smart Grid Communications.Dresden, Germany:IEEE, 2017.253-258 [62] Lin H, Deng Y, Shukla S, Thorp J, Mili L.Cyber security impacts on all-PMU state estimator-a case study on co-simulation platform GECO.In:Proceedings of the 3rd IEEE International Conference on Smart Grid Communications.Tainan, China:IEEE, 2012.587-592 [63] Cao Y J, Shi X Y, Li Y, Tan Y, Shahidehpour M, Shi S L.A simplified co-simulation model for investigating impacts of cyber-contingency on power system operations.IEEE Transactions on Smart Grid, 2018, 9(5):4893-4905 doi: 10.1109/TSG.2017.2675362 [64] Sadi M A H, Ali M H, Dasgupta D, Abercrombie R K, Kher S.Co-simulation platform for characterizing cyber attacks in cyber physical systems.In:Proceedings of the 2015 IEEE Symposium Series on Computational Intelligence.Cape Town, South Africa:IEEE, 2015.1244-1251 [65] Adhikari U, Morris T, Pan S Y.WAMS cyber-physical test bed for power system, cybersecurity study, and data mining.IEEE Transactions on Smart Grid, 2017, 8(6):2744-2753 doi: 10.1109/TSG.2016.2537210 [66] Tang Y, Tai W, Liu Z J, Li M Y, Wang Q, Liang Y, et al.A hardware-in-the-loop based co-simulation platform of cyber-physical power systems for wide area protection applications.Applied Sciences, 2017, 7(12):Article No.1279 doi: 10.3390/app7121279 [67] 贾驰千, 冯冬芹.基于多目标决策的工控系统设备安全评估方法研究.自动化学报, 2016, 42(5):706-714 http://www.aas.net.cn/CN/abstract/abstract18860.shtmlJia Chi-Qian, Feng Dong-Qin.Industrial control system devices security assessment with multi-objective decision.Acta Automatica Sinica, 2016, 42(5):706-714 http://www.aas.net.cn/CN/abstract/abstract18860.shtml -




 下载:
下载: