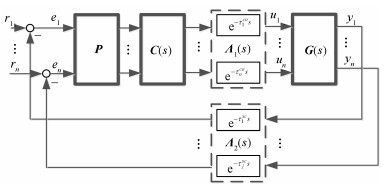
Feasibility Analysis of Encrypted Transmission on Security of Industrial Control Systems
-
摘要: 针对需要对现场数据加密的工业控制系统(Industrial control system,ICS),基于稳定性判据设计一种加密传输机制的可行性评估模型,结合超越方程D-subdivision求解法,提出一种数据加密长度可行域求解算法.改进IAE(Integral absolute error)并提出Truncated IAE(TIAE)-based指标,用于评估可行域内不同数据长度对系统实时性能的影响.利用嵌入式平台测定的加密算法执行时间与数据长度的关系,评估了两种对称加密算法应用在他励直流电机控制系统中的可行性,验证了可行域求解算法的准确性,并获得了实时性能随数据长度的变化规律.Abstract: For those industrial control systems (ICS) whose field data need to be encrypted, a model, based on stability criterion is designed to assess the feasibility of the encrypted transmition mechanism. Combined with D-subdivision solution to transcentdental equation, a method to solve the feasible region of the length of encrypted data quantitatively is proposed. Integral absolute error (IAE) is improved to introduce the truncated IAE (TIAE)-based index, which is designed for evaluating the real-time performance influenced by the length in the feasible region. In terms of the relationship between execute time of encryption algorithm and length measured on embedded platform, two symmetric encryption algorithms for the control system of separately excited DC motor are evaluated, the accuracy of solution to the feasible region is verified, and the change law between real-time performance and length is obtained.1) 本文责任编委 陈积明
-
表 1 加密算法执行时间与数据加密长度测试数据
Table 1 Test data between the execute time of encryption algorithms and the length of plaintext
长度(B) 16 144 272 400 528 656 784 912 1040 时间(ms) AES加密 7.48 67.21 127.18 187.24 246.88 306.46 366.37 426.42 485.94 AES解密 9.32 83.99 158.81 233.46 308.88 383.58 458.43 533.18 608.33 DES加密 8.83 79.72 150.59 228.22 300.12 372.94 445.34 517.98 595.94 DES解密 6.97 62.46 117.91 178.22 234.84 291.86 348.74 405.94 462.94 表 2 集合$\Theta$判定表格
Table 2 Judging form of $\Theta$
$\tau$ $\omega $ $T$ ${\rm{RT}}$ ${\rm{NU(}}\tau {\rm{)}}$ (0, 0.321) 0 0.321 4.775 0.201867 1 (0.321, 1.637) 2 1.637 4.775 0.201867 1 (1.637, 2.953) 4 2.953 4.775 0.201867 1 $\cdots$ $\cdots$ $\cdots$ $\cdots$ 6 表 3 实时性指标与数据加密长度测试数据
Table 3 Test data between the real-time performance index and the length of encrypted data
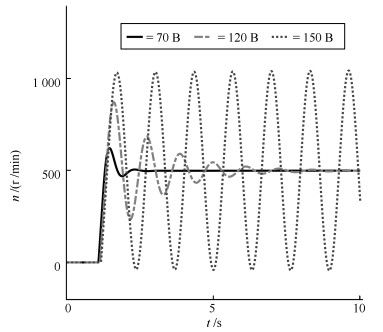
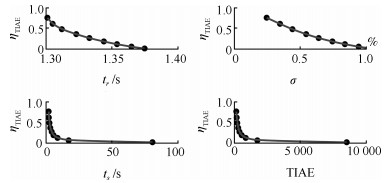
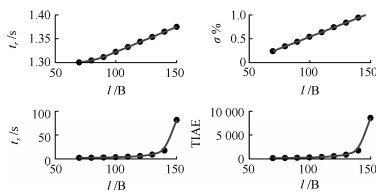
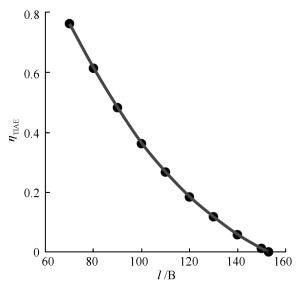
$l$(B) ${t_r}$(s) $\sigma\%$ ${t_s}$ (s) TIAE ${\eta _{{{\rm TIAE}}}}$ 0 20 0 1.618 99.2545 1 70 1.301 0.2438 1.972 130.2633 0.7620 80 1.305 0.3453 2.118 161.8826 0.6131 90 1.312 0.4396 2.596 206.0987 0.4816 100 1.323 0.544 3.209 274.6412 0.3614 110 1.333 0.639 4.311 372.4369 0.2665 120 1.344 0.7434 5.676 541.5546 0.1833 130 1.354 0.8383 8.749 846.1615 0.1173 140 1.365 0.9427 17.231 1.73E+03 0.0573 150 1.375 1.0376 80.985 8.52E+03 0.0117 -
[1] Knowles W, Prince D, Hutchison D, Disso J F P, Jones K. A survey of cyber security management in industrial control systems. International Journal of Critical Infrastructure Protection, 2015, 9:52-80 doi: 10.1016/j.ijcip.2015.02.002 [2] ICS-CERT. ICS-CERT Monitor[Online], available: https://ics-cert.us-cert.gov/monitors/ICS-MM201512, May 3, 2016. [3] Pang Z H, Liu G P, Zhou D H, Hou F Y, Sun D H. Two-channel false data injection attacks against output tracking control of networked systems. IEEE Transactions on Industrial Electronics, 2016, 63(5):3242-3251 doi: 10.1109/TIE.2016.2535119 [4] Tang B X, Alvergue L D, Gu G X. Secure networked control systems against replay attacks without injecting authentication noise. In: Proceedings of the 2015 American Control Conference (ACC). Chicago, USA: IEEE, 2015. 6028-6033 [5] Zijlstra P. Cryptography for a Networked Control System using Asynchronous Event-Triggered Control[Master dissertation], Delft University of Technology, Netherlands, 2016. [6] Zhang L Y, Xie L, Li W Z, Wang Z L. Security solutions for networked control systems based on des algorithm and improved grey prediction model. International Journal of Computer Network and Information Security (IJCNIS), 2013, 6(1):78-85 doi: 10.5815/ijcnis [7] Wei M K, Wang W Y. Safety can be dangerous: secure communications impair smart grid stability under emergencies. In: Proceedings of the 2015 IEEE Global Communications Conference (GLOBECOM). San Diego, USA: IEEE, 2015. 1-6 [8] Sipahi R, Niculescu S I, Abdallah C T, Michiels W, Gu K Q. Stability and stabilization of systems with time delay. IEEE Control Systems, 2011, 31(1):38-65 doi: 10.1109/MCS.2010.939135 [9] Sipahi R, Olgac N. A unique methodology for the stability robustness of multiple time delay systems. Systems & Control Letters, 2006, 55(10):819-825 http://www.sciencedirect.com/science/article/pii/S0167691106000612 [10] Olgac N, Sipahi R. An exact method for the stability analysis of time-delayed linear time-invariant (LTI) systems. IEEE Transactions on Automatic Control, 2002, 47(5):793-797 doi: 10.1109/TAC.2002.1000275 [11] Harris T J. Assessment of control loop performance. The Canadian Journal of Chemical Engineering, 1989, 67(5):856-861 doi: 10.1002/cjce.v67:5 [12] Eriksson P G, Isaksson A J. Some aspects of control loop performance monitoring. In: Proceedings of the 3rd IEEE Conference on Control Applications. Scotland, UK: IEEE, 1994. 1029-1034 [13] Gupta R A, Chow M Y. Performance assessment and compensation for secure networked control systems. In: Proceedings of the 34th Annual Conference of IEEE Industrial Electronics. Orlando, USA: IEEE, 2008. 2929-2934 [14] Zeng W T, Chow M Y. Optimal tradeoff between performance and security in networked control systems based on coevolutionary algorithms. IEEE Transactions on Industrial Electronics, 2012, 59(7):3016-3025 doi: 10.1109/TIE.2011.2178216 [15] Yu Z P, Wang J D, Huang B, Bi Z F. Performance assessment of PID control loops subject to setpoint changes. Journal of Process Control, 2011, 21(8):1164-1171 doi: 10.1016/j.jprocont.2011.06.012 [16] Smith R S. Covert misappropriation of networked control systems:presenting a feedback structure. IEEE Control Systems, 2015, 35(1):82-92 doi: 10.1109/MCS.2014.2364723 -




 下载:
下载: