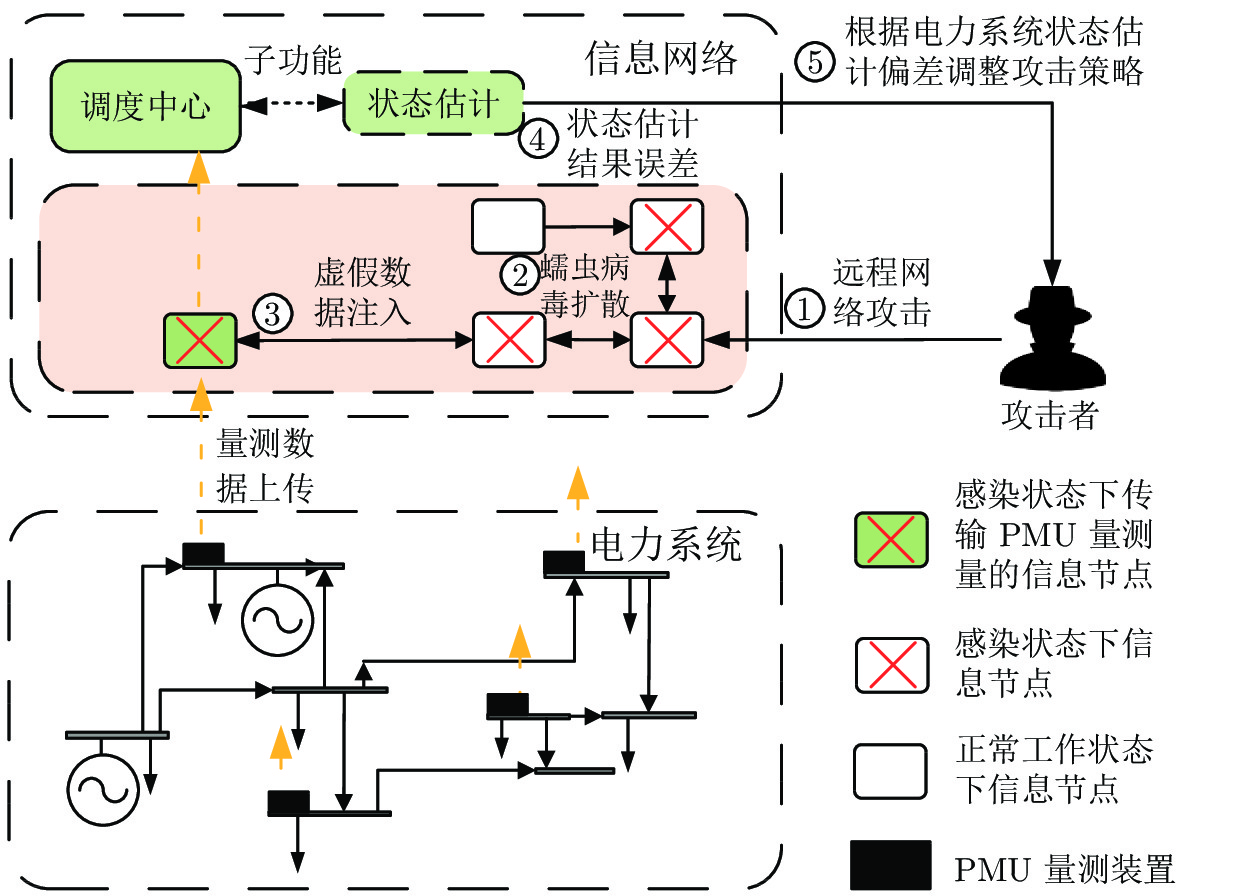
The Coordinated Cyber Physical Power Attack Strategy Based on Worm Propagation and False Data Injection
-
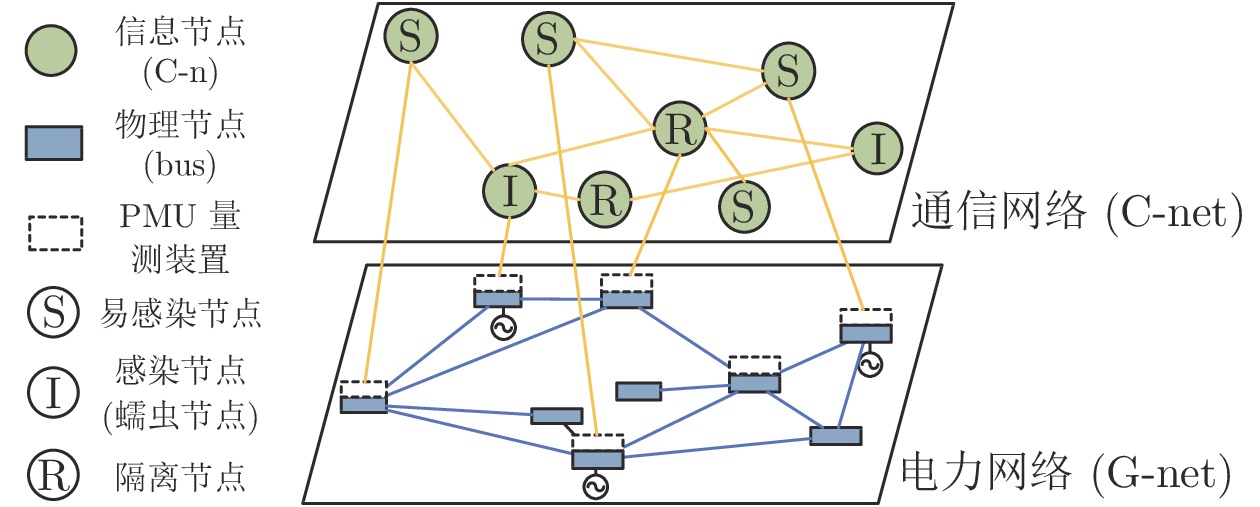
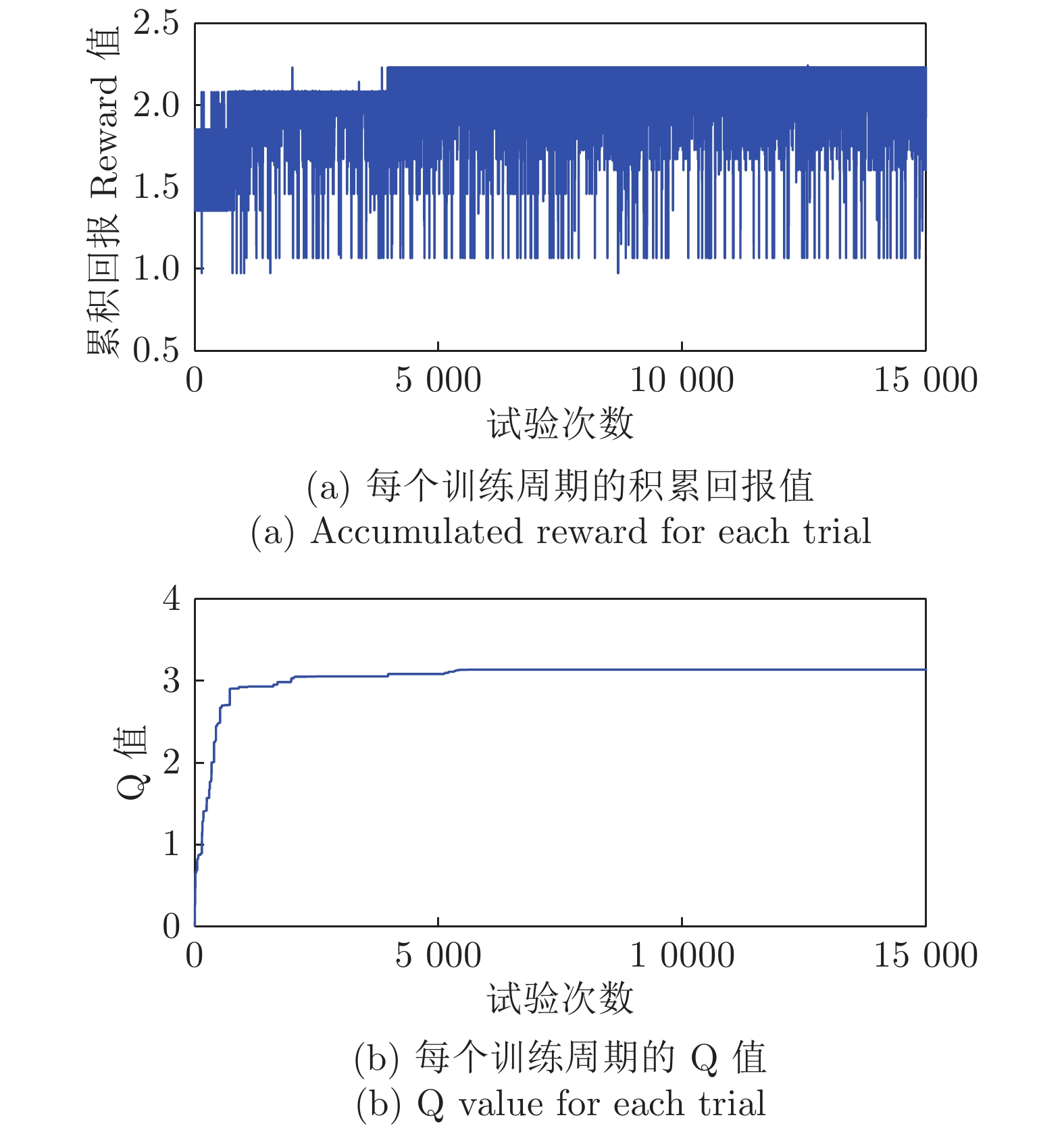
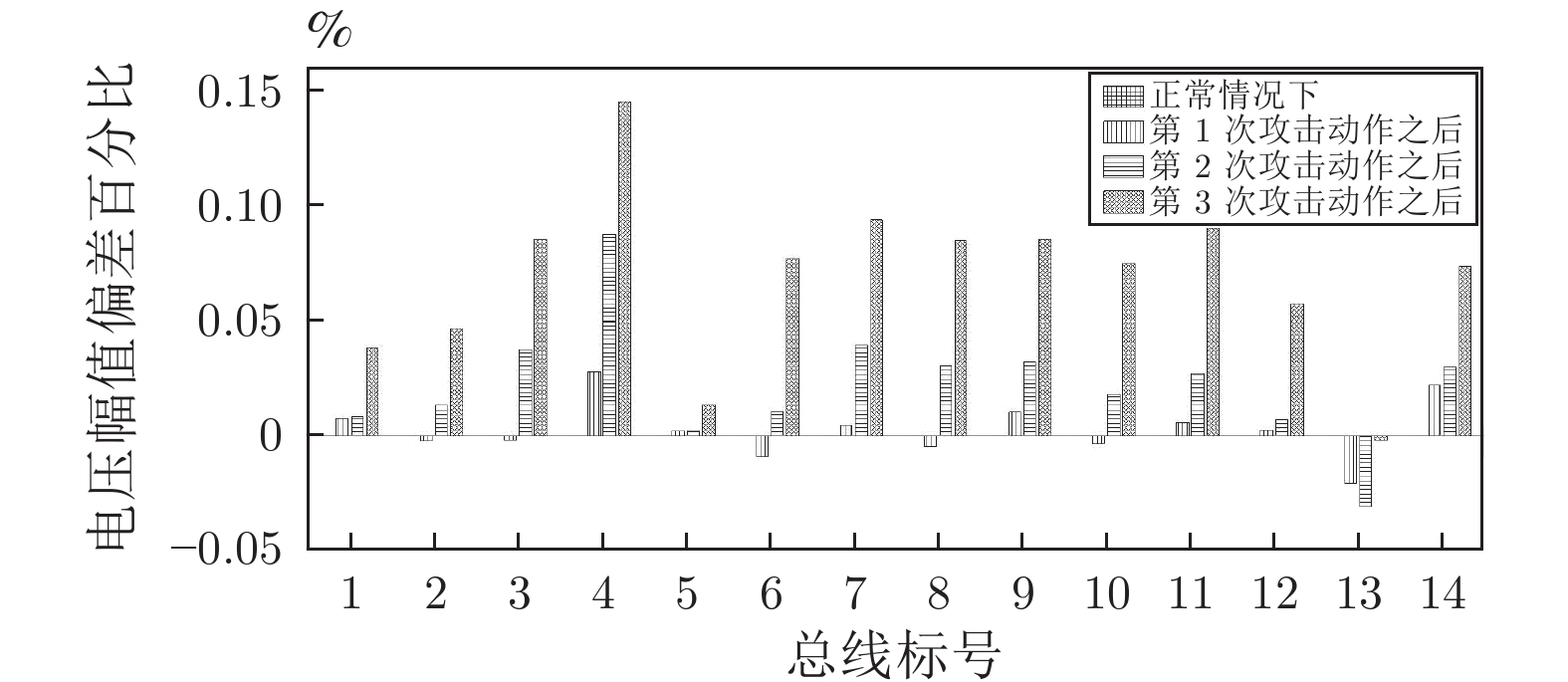
摘要: 随着信息技术与现代电力系统的结合日趋紧密, 通信系统异常和网络攻击均可能影响到电力系统的安全稳定运行. 为了研究工控蠕虫病毒对电网带来的安全隐患, 本文首次建立了基于马尔科夫决策过程(Markov decision process, MDP)的电力信息物理系统跨空间协同攻击模型, 该模型同时考虑通信设备漏洞被利用的难易程度为代价以及对电力网络的破坏程度为收益两方面因素, 能够更有效地识别系统潜在风险. 其次, 采用Q学习算法求解在该模型下的最优攻击策略, 并依据电力系统状态估计的误差值来评定该攻击行为对电力系统造成的破坏程度. 最后, 本文在通信8节点−电力14节点的耦合系统上进行联合仿真, 对比结果表明相较单一攻击方式, 协同攻击对电网的破坏程度更大. 与传统的不考虑通信网络的电力层攻击研究相比, 本模型辨识出的薄弱节点也考虑了信息层的关键节点的影响, 对防御资源的分配有指导作用.Abstract: With the deep integration of information technologies in modern power systems, cyber system anomalies and network attacks can threaten the safety and stability of power system operation. To study the security risks of the power system caused by the latest industrial control worm, a coordinated cyber-physical power attack model based on the Markov decision process (MDP) is proposed in this paper. Then, the Q-learning algorithm is adopted to search for the optimal attack strategy in the proposed model, and the error of state estimation result induced by the attacks is devised to quantify the potential physical influences-attack benefits. Eventually, numerical joint simulation experiments are conducted on the 8CYBER_NODE-14BUS coupling test system, and the results show that the coordinated attack model proposed in this paper is more destructive. Compared with the traditional isolated physical attack without considering the cyber network, the identified weak nodes can also consider the influence of the cyber devices and guide the allocation of defense resources.
-
表 1 考虑不同攻击方法下的影响
Table 1 Attack effect under different attack methods
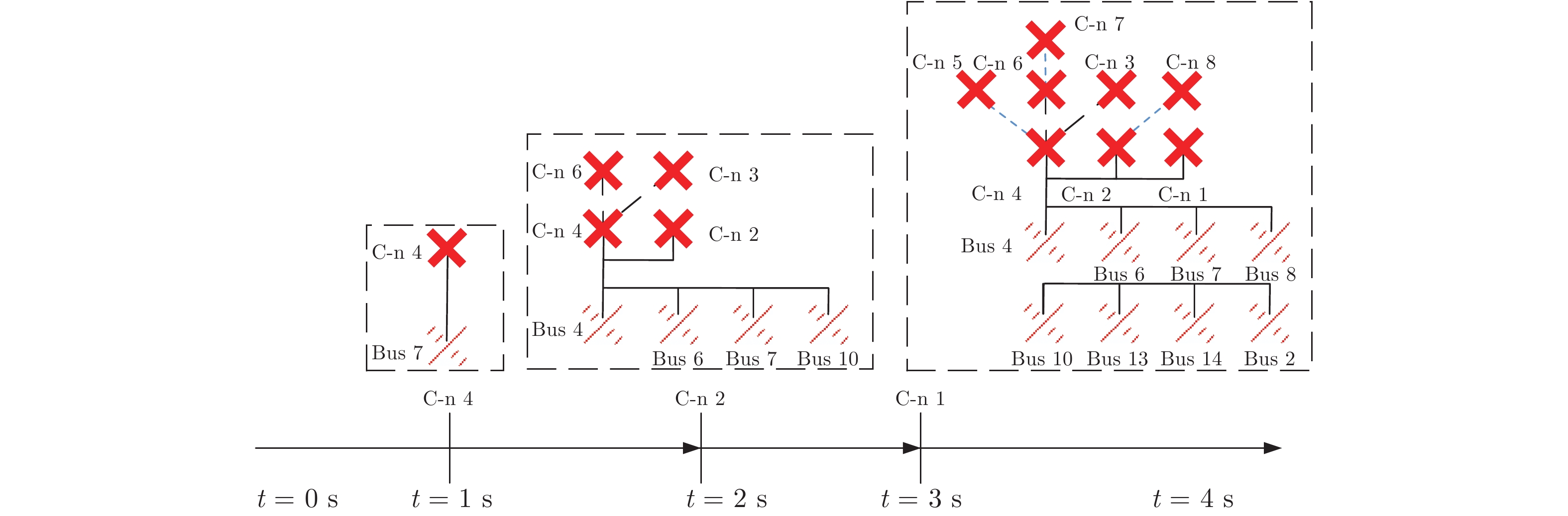
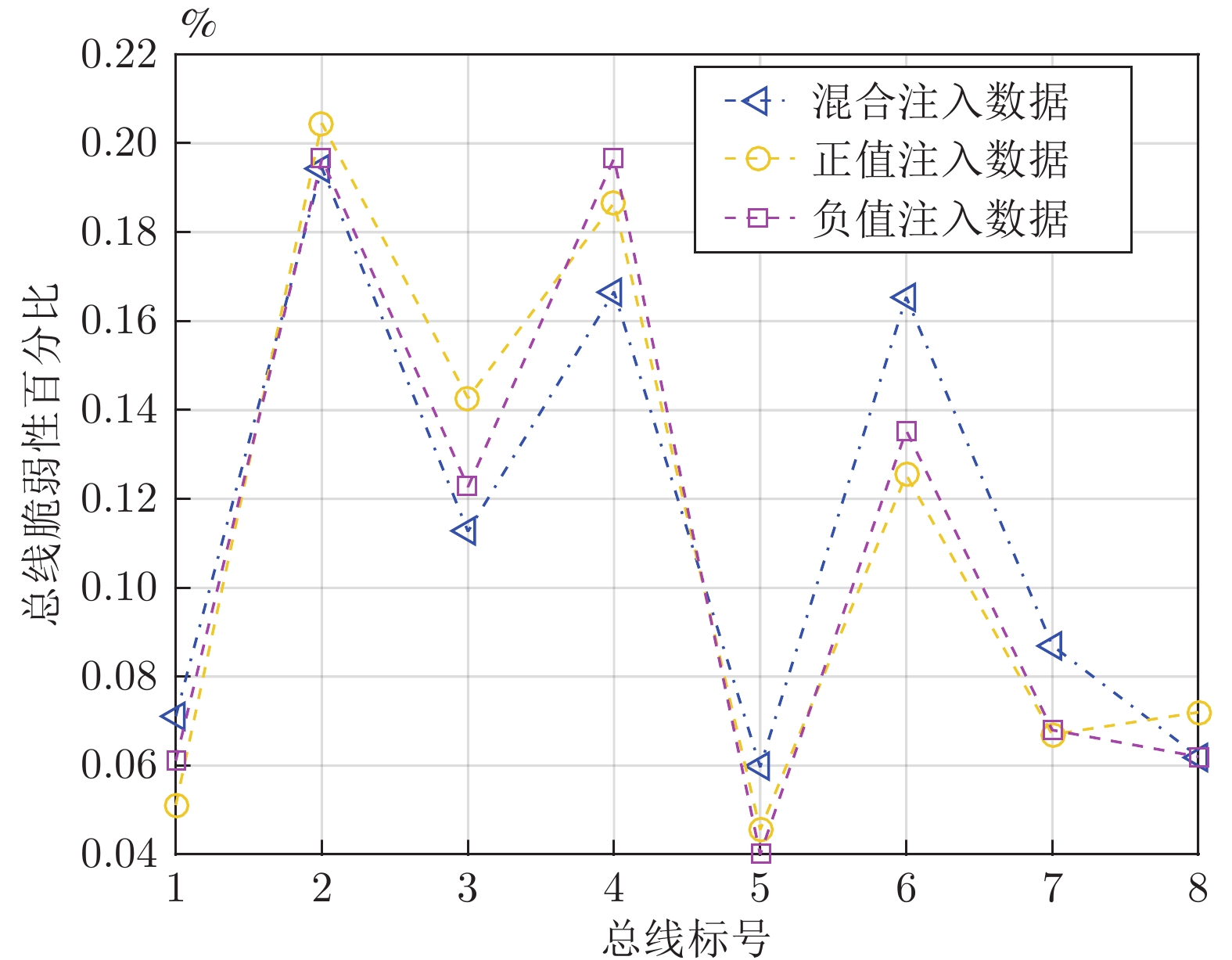
攻击类型 参数 n = 1 n = 2 n = 3 网络攻击 $\pi^*$ 1 $2\rightarrow 3$ $2\rightarrow 3\rightarrow 4$ $f(\Delta \theta )$ 0.022 0.103 0.2333 $f(\Delta V )$ 0.043 0.115 0.245 物理攻击 $\pi^*$ 4 $5 \rightarrow 6$ $5\rightarrow 4\rightarrow 7$ $f(\Delta \theta )$ 0.035 0.144 0.344 $f(\Delta V )$ 0.061 0.134 0.444 协同攻击 $\pi^*$ 3 $6 \rightarrow 7$ $2 \rightarrow 4 \rightarrow 8$ $f(\Delta \theta )$ 0.077 0.223 0.523 $f(\Delta V )$ 0.062 0.267 0.667 表 2 电力设备被攻击可能性分析(%)
Table 2 The vulnerability analysis of power equipment (%)
通信−电力 节点耦合 协同攻击 物理攻击 C-n 1 Bus 2 31.65 16.66 C-n 2 Bus 4 32.51 16.40 C-n 3 Bus 6 30.60 11.27 C-n 4 Bus 7 0.67 15.26 C-n 5 Bus 8 0.85 5.97 C-n 6 Bus 10 1.00 19.54 C-n 7 Bus 13 1.44 8.70 C-n 8 Bus 14 1.25 6.20 表 3 系统离散程度不同时电力设备被攻击的可能性分析
Table 3 The vulnerability analysis of power equipment under different discrete degrees of false data
离散状态数目 各个电力设备被攻击的可能性分析 (%) 母线标号 Bus 2 Bus 4 Bus 6 Bus 7 Bus 8 Bus 10 Bus 13 Bus 14 $N_V^g = N_\theta^g = 4$ 7.18 20.88 13.36 18.25 6.54 16.03 9.02 6.31 $N_V^g = N_\theta^g = 6$ 8.31 19.95 12.97 17.66 6.43 17.38 10.50 6.80 $N_V^g = N_\theta^g = 8$ 8.11 20.45 12.27 17.66 6.97 17.54 9.70 7.20 A1 NS2中通信网络的参数配置
A1 The parameters of cyber network in NS2
起点 终点 带宽 (Mbps) 时延 (ms) C-n 1 C-n 2 60 60 C-n 2 C-n 6 60 20 C-n 2 C-n 8 60 20 C-n 7 C-n 8 60 20 C-n 7 C-n 6 60 20 C-n 1 C-n 3 60 60 C-n 3 C-n 4 60 20 C-n 3 C-n 5 60 20 C-n 4 C-n 5 60 20 A2 每个通信设备上存在的漏洞的CVSS评分
A2 The CVSS standards of each cyber node
标号 漏洞 ID 标号 影响度量分数 漏洞利用分数 基础分数 C-n 1 CVE-2016-8366 3.4 3.9 7.3 C-n 2 CVE-2016-8366 3.4 3.9 7.3 C-n 3 CVE-2016-8366 3.4 3.9 7.3 C-n 4 CVE-2017-14470 2.7 2.8 5.5 C-n 5 CVE-2017-14470 2.7 2.8 5.5 C-n 6 CVE-2017-14470 2.7 2.8 5.5 C-n 7 CVE-2018-16210 5.9 3.9 9.8 C-n 8 CVE-2018-16210 5.9 3.9 9.8 -
[1] 王冰玉, 孙秋野, 马大中, 黄博南. 能源互联网多时间尺度的信息物理融合模型. 电力系统自动化, 2016, 40(17): 13-21Wang Bing-Yu, Sun Qiu-Ye, Ma Da-Zhong, Huang Bo-Nan. A cyber physical model of the energy internet based on multiple time scales. Automation of Electric Power Systems, 2016, 40(17): 13-21 [2] 刘烃, 田决, 王稼舟, 吴宏宇, 孙利民, 周亚东, 等. 信息物理融合系统综合安全威胁与防御研究. 自动化学报, 2019, 45(1): 5-24Liu Ting, Tian Jue, Wang Jia-Zhou, Wu Hong-Yu, Sun Li-Min, Zhou Ya-Dong, et al. Integrated security threats and defense of cyber-physical systems. Acta Automatica Sinica, 2019, 45(1): 5-24 [3] Mo Y C, Xing L D, Zhong F R, Zhang Z. Reliability evaluation of network systems with dependent propagated failures using decision diagrams. IEEE Transactions on Dependable and Secure Computing, 2016, 13(6): 672-683 doi: 10.1109/TDSC.2015.2433254 [4] Yao Y, Sheng C, Fu Q, Liu H X, Wang D J. A propagation model with defensive measures for PLC-PC worms in industrial networks. Applied Mathematical Modelling, 2019, 69: 696-713 doi: 10.1016/j.apm.2019.01.014 [5] 王先培, 田猛, 董政呈, 朱国威, 龙嘉川, 代荡荡, 等. 输电网虚假数据攻击研究综述. 电网技术, 2016, 40(11): 3406-3414Wang Xian-Pei, Tian Meng, Dong Zheng-Cheng, Zhu Guo-Wei, Long Jia-Chuan, Dai Dang-Dang, et al. Survey of false data injection attacks in power transmission systems. Power System Technology, 2016, 40(11): 3406-3414 [6] Hug G, Giampapa J A. Vulnerability assessment of AC state estimation with respect to false data injection cyber-attacks. IEEE Transactions on Smart Grid, 2012, 3(3): 1362-1370 doi: 10.1109/TSG.2012.2195338 [7] 王琦, 邰伟, 汤奕, 倪明. 面向电力信息物理系统的虚假数据注入攻击研究综述. 自动化学报, 2019, 45(1): 72-83Wang Qi, Tai Wei, Tang Yi, Ni Ming. A review on false data injection attack toward cyber-physical power system. Acta Automatica Sinica, 2019, 45(1): 72-83 [8] Xiang Y M, Wang L F, Liu N. Coordinated attacks on electric power systems in a cyber-physical environment. Electric Power Systems Research, 2017, 149: 156-168 doi: 10.1016/j.jpgr.2017.04.023 [9] 杨飞生, 汪璟, 潘泉, 康沛沛. 网络攻击下信息物理融合电力系统的弹性事件触发控制. 自动化学报, 2019, 45(1): 110-119Yang Fei-Sheng, Wang Jing, Pan Quan, Kang Pei-Pei. Resilient event-triggered control of grid cyber-physical systems against Cyber Attack. Acta Automatica Sinica, 2019, 45(1): 110-119 [10] Deng R L, Zhuang P, Liang H. CCPA: Coordinated cyber-physical attacks and countermeasures in smart grid. IEEE Transactions on Smart Grid, 2017, 8(5): 2420-2430 doi: 10.1109/TSG.2017.2702125 [11] 郭庆来, 辛蜀骏, 王剑辉, 孙宏斌. 由乌克兰停电事件看信息能源系统综合安全评估. 电力系统自动化, 2016, 40(5): 145-147Guo Qing-Lai, Xin Shu-Jun, Wang Jian-Hui, Sun Hong-Bin. Comprehensive security assessment for a cyber physical energy system: A lesson from Ukraine’s blackout. Automation of Electric Power Systems, 2016, 40(5): 145-147) [12] Liang G Q, Weller S R, Zhao J H, Luo F J, Dong Z Y. The 2015 Ukraine blackout: Implications for false data injection attacks. IEEE Transactions on Power Systems, 2017, 32(4): 3317-3318 doi: 10.1109/TPWRS.2016.2631891 [13] Korkali M, Veneman J G, Tivnan B F, Bagrow J P, Hines P D H. Reducing cascading failure risk by increasing infrastructure network interdependence. Scientific Reports, 2017, 7: Article No. 44499 doi: 10.1038/srep44499 [14] Buldyrev S V, Parshani R, Paul G, Stanley H E, Havlin S. Catastrophic cascade of failures in interdependent networks. Nature, 2010, 464(7291): 1025-1028 doi: 10.1038/nature08932 [15] 汤奕, 韩啸, 吴英俊, 鞠勇, 周霞, 倪明. 考虑通信系统影响的电力系统综合脆弱性评估. 中国电机工程学报, 2015, 35(23): 6066-6074Tang Yi, Han Xiao, Wu Ying-Jun, Ju Yong, Zhou Xia, Ni Ming. Electric power system vulnerability assessment considering the influence of communication system. Proceedings of the CSEE, 2015, 35(23): 6066-6074 [16] 田猛, 董政呈, 王先培, 赵乐, 简子倪. 目标冲突下电力信息物理协同攻击分析. 电网技术, 2019, 43(7): 2336-2344Tian Meng, Dong Zheng-Cheng, Wang Xian-Pei, Zhao Le, Jian Zi-Ni. Analysis of electrical coordinated cyber physical attacks under goal conflict. Power System Technology, 2019, 43(7): 2336-2344 [17] Liu X, Li Z Y, Liu X D, Li Z Y. Masking transmission line outages via false data injection attacks. IEEE Transactions on Information Forensics and Security, 2016, 11(7): 1592-1602 doi: 10.1109/TIFS.2016.2542061 [18] Zhang J Z, Sankar L. Physical system consequences of unobservable state-and-topology cyber-physical attacks. IEEE Transactions on Smart Grid, 2016, 7(4): 2016-2025 doi: 10.1109/TSG.2016.2552178 [19] Hao Y S, Wang M, Chow J H. Likelihood analysis of cyber data attacks to power systems with Markov decision processes. IEEE Transactions on Smart Grid, 2018, 9(4): 3191-3202 doi: 10.1109/TSG.2016.2628522 [20] Duan J, Chow M Y. A novel data integrity attack on consensus-based distributed energy management algorithm using local information. IEEE Transactions on Industrial Informatics, 2019, 15(3): 1544-1553 doi: 10.1109/TII.2018.2851248 [21] 孙秋野, 杨凌霄, 张化光. 智慧能源-人工智能技术在电力系统中的应用与展望. 控制与决策, 2018, 33(5): 938-949Sun Qiu-Ye, Yang Ling-Xiao, Zhang Hua-Guang. Smart energy -Applications and prospects of artificial intelligence technology in power system. Control and Decision, 2018, 33(5): 938-949 [22] Yan J, He H B, Zhong X N, Tang Y F. Q-learning-based vulnerability analysis of smart grid against sequential topology attacks. IEEE Transactions on Information Forensics and Security, 2017, 12(1): 200-210 doi: 10.1109/TIFS.2016.2607701 [23] 石立宝, 简洲. 基于动态攻防博弈的电力信息物理融合系统脆弱性评估. 电力系统自动化, 2016, 40(17): 99-105Shi Li-bao, Jian Zhou. Vulnerability assessment of cyber physical power system based on dynamic attack-defense game model. Automation of Electric Power Systems, 2016, 40(17): 99-105 [24] Wei L F, Sarwat A I, Saad W, Biswas S. Stochastic games for power grid protection against coordinated cyber-physical attacks. IEEE Transactions on Smart Grid, 2018, 9(2): 684-694 doi: 10.1109/TSG.2016.2561266 [25] 周彦衡, 吴俊勇, 张广韬, 苗青, 屈博, 胡艳梅. 考虑级联故障的电力系统脆弱性评估. 电网技术, 2013, 37(2): 444-449 doi: 10.13335/j.1000-3673.pst.2013.02.027Zhou Yan-Heng, Wu Jun-Yong, Zhang Guang-Tao, Miao Qing, Qu Bo, Hu Yan-Mei. Assessment on power system vulnerability considering cascading failure. Power System Technology, 2013, 37(2): 444-449 doi: 10.13335/j.1000-3673.pst.2013.02.027 [26] Langner R. Stuxnet: Dissecting a cyberwarfare weapon. IEEE Security & Privacy, 2011, 9(3): 49-51 [27] Warda H, Zhioua S, Almulhem A. PLC access control: A security analysis. In: Proceedings of the 2016 World Congress on Industrial Control Systems Security (WCICSS). London, UK: IEEE, 2016. [28] 叶夏明, 文福拴, 尚金成, 何洋. 电力系统中信息物理安全风险传播机制. 电网技术, 2015, 39(11): 3072-3079 doi: 10.13335/j.1000-3673.pst.2015.11.009Ye Xia-Ming, Wen Fu-Shuan, Shang Jin-Cheng, He Yang. Propagation mechanism of cyber physical security risks in power systems. Power System Technology, 2015, 39(11): 3072-3079 doi: 10.13335/j.1000-3673.pst.2015.11.009 [29] Tarali A, Abur A. Bad data detection in two-stage state estimation using phasor measurements. In: Proceedings of the 3rd IEEE PES Innovative Smart Grid Technologies Europe (ISGT). Berlin, Germany: IEEE, 2012. [30] Wang X A, Shi D, Wang J H, Yu Z, Wang Z W. Online identification and data recovery for PMU data manipulation attack. IEEE Transactions on Smart Grid, 2019, 10(6): 5889-5898 doi: 10.1109/TSG.2019.2892423 [31] Beasley C, Zhong X S, Deng J, Brooks R, Venayagamoorthy G K. A survey of electric power synchrophasor network cyber security. In: Proceedings of the 2014 IEEE PES Innovative Smart Grid Technologies, Europe (ISGT). Istanbul, Turkey: IEEE, 2014. 1−5 [32] 李强, 周京阳, 于尔铿, 刘树春, 王磊. 基于相量量测的电力系统线性状态估计. 电力系统自动化, 2005, 29(18): 24-28 doi: 10.3321/j.issn:1000-1026.2005.18.005Li Qiang, Zhou Jing-Yang, Yu Er-Keng, Liu Shu-Chun, Wang Lei. Power system linear state estimation based on phasor measurement. Automation of Electric Power Systems, 2005, 29(18): 24-28 doi: 10.3321/j.issn:1000-1026.2005.18.005 [33] Li P K, Liu Y, Xin H H, Jiang X C. A robust distributed economic dispatch strategy of virtual power plant under cyber-attacks. IEEE Transactions on Industrial Informatics, 2018, 14(10): 4343-4352 doi: 10.1109/TII.2017.2788868 [34] Liang J W, Sankar L, Kosut O. Vulnerability analysis and consequences of false data injection attack on power system state estimation. IEEE Transactions on Power Systems, 2016, 31(5): 3864-3872 doi: 10.1109/TPWRS.2015.2504950 -




 下载:
下载: