|
[1]
|
Johansson K H, Pappas G J, Tabuada P, Tomlin C J. Guest editorial special issue on control of cyber-physical systems. IEEE Transactions on Automatic Control, 2014, 59(12): 3120-3121 doi: 10.1109/TAC.2014.2363896
|
|
[2]
|
Fink J, Ribeiro A, Kumar V. Robust control for mobility and wireless communication in cyber-physical systems with application to robot teams. Proceedings on the IEEE, 2012, 100(1): 164-178 doi: 10.1109/JPROC.2011.2161427
|
|
[3]
|
Li H, Lai L, Poor H V. Multicast routing for decentralized control of cyber physical systems with an application in smart grid. IEEE Journal on Selected Areas in Communications, 2012, 30(6): 1097-1107 doi: 10.1109/JSAC.2012.120708
|
|
[4]
|
Langner R. Stuxnet: dissecting a Cyberwarfare Weapon. IEEE Security & Privacy, 2011, 9(3): 49-51
|
|
[5]
|
Hu L, Wang Z, Han Q, Liu X. State estimation under false data injection attacks: Security analysis and system protection. Automatica, 2018, 87: 176-183 doi: 10.1016/j.automatica.2017.09.028
|
|
[6]
|
艾纳安德尔. 信息物理系统和工业4.0. 智能制造, 2015, 9: 10-12 doi: 10.3969/j.issn.1671-8186.2015.07.002Einar Andel. Cyber-physical systems and industry 4.0. Intelligent Manufacturing, 2015, 9: 10-12 doi: 10.3969/j.issn.1671-8186.2015.07.002
|
|
[7]
|
Pasqualetti F, Dorfler F, Bullo F. Attack detection and identification in cyber-physical systems. IEEE Transactions on Automatic Control, 2013, 58(11): 2715-2729 doi: 10.1109/TAC.2013.2266831
|
|
[8]
|
Pang Z, Liu G, Zhou D, Hou F, Sun D. Two-channel false data injection attacks against output tracking control of networked systems. IEEE Transactions on Industrial Electronics, 2016, 63(5): 3242-3251 doi: 10.1109/TIE.2016.2535119
|
|
[9]
|
Chen B, Ho D W C, Zhang W, Yu L. Distributed dimensionality reduction fusion estimation for cyber-physical systems under DoS attacks. IEEE Transactions on Systems, Man, and Cybernetics: Systems, 2019, 49(2): 455-468 doi: 10.1109/TSMC.2017.2697450
|
|
[10]
|
Lai S Y, Chen B, Li T X, Yu L. Packet-based state feedback control under DoS attacks in cyber-physical systems. IEEE Transactions on Circuits and Systems II: Express Briefs, 2019. 66(8): 1421−1425
|
|
[11]
|
Chen B, Ho D W C, Hu G, Yu L. Secure fusion estimation for bandwidth constrained cyber-physical systems under replay attacks. IEEE Transactions on Cybernetics, 2018, 48(6): 1862-1876 doi: 10.1109/TCYB.2017.2716115
|
|
[12]
|
Ding D, Han Q, Xiang Y, Ge X, Zhang X. A survey on security control and attack detection for industrial cyber-physical systems. Neurocomputing, 2018, 275: 1674-1683 doi: 10.1016/j.neucom.2017.10.009
|
|
[13]
|
Liu Y, Ning P, Reiter M K. False data injection attacks against state estimation in electric power grids. ACM Transactions on Information and System Security, 2011, 14(1): 1-33
|
|
[14]
|
Ye N, Zhang Y, Borror C M. Robustness of the Markov-chain model for cyber-attack detection. IEEE Transactions on Reliability, 2004, 53(1): 116-123 doi: 10.1109/TR.2004.823851
|
|
[15]
|
Chorppath A K, Alpcan T, Boche H. Bayesian mechanisms and detection methods for wireless network with malicious users. IEEE Transactions on Mobile Computing, 2016, 15(10): 2452-2465 doi: 10.1109/TMC.2015.2505724
|
|
[16]
|
Kailkhura B, Han Y S, Brahma S, Varshney P K. Distributed Bayesian detection in the presence of byzantine data. IEEE Transactions on Signal Processing, 2015, 63(9): 5250-5263
|
|
[17]
|
Kailkhura B, Han Y S, Brahma S, Varshney P K. Asymptotic analysis of distributed Bayesian detection with byzantine data. IEEE Signal Processing Letters, 2015, 22(5): 608-612 doi: 10.1109/LSP.2014.2365196
|
|
[18]
|
Rawat A S, Anand P, Chen H, Varshney P K. Collaborative spectrum sensing in the presence of byzantine attacks in cognitive radio networks. IEEE Transactions on Signal Processing, 2011, 59(2): 774-786 doi: 10.1109/TSP.2010.2091277
|
|
[19]
|
Manandhar K, Cao X, Hu F, Liu Y. Detection of faults and attacks including false data injection attack in smart grid using kalman filter. IEEE Transactions on Control of Network Systems, 2014, 1(4): 370-379 doi: 10.1109/TCNS.2014.2357531
|
|
[20]
|
Mo Y, Chabukswar R, Sinopoli B. Detecting integrity attacks on SCADA systems. IEEE Transactions on Control Systems Technology, 2014, 22(4): 1396-1407 doi: 10.1109/TCST.2013.2280899
|
|
[21]
|
Rawat D B, Bajracharya C. Detection of false data injection attacks in smart grid communication systems. IEEE Signal Processing Letters, 2015, 22(10): 1652-1656 doi: 10.1109/LSP.2015.2421935
|
|
[22]
|
Liu L, Esmalifalak M, Ding Q, Emesih V A, Han Z. Detecting false data injection attacks on power grid by sparse optimization. IEEE Transactions on Smart Grid, 2014, 5(2): 612-621 doi: 10.1109/TSG.2013.2284438
|
|
[23]
|
Deng R, Xiao G, Lu R. Defending against false data injection attacks on power system state estimation. IEEE Transactions on Industrial Informatics, 2017, 13(1): 198-207 doi: 10.1109/TII.2015.2470218
|
|
[24]
|
Huang Y, Tang J, Cheng Y, Li H, Campbell K A, Han Z. Real-time detection of false data injection in smart grid networks: An adaptive CUSUM method and analysis. IEEE Systems Journal, 2016, 10(2): 532-543 doi: 10.1109/JSYST.2014.2323266
|
|
[25]
|
Zhang Q, Basseville M. Statistical detection and isolation of additive faults in linear time-varying systems. Automatica, 2014, 50(10): 2527-2538 doi: 10.1016/j.automatica.2014.09.004
|
|
[26]
|
Zhang Q. Adaptive Kalman filter for actuator fault diagnosis. Automatica, 2018, 93: 333-342 doi: 10.1016/j.automatica.2018.03.075
|
|
[27]
|
Sun S, Deng Z. Multi-sensor optimal information fusion kalman filter. Automatica, 2004, 40(6): 1017-1023 doi: 10.1016/j.automatica.2004.01.014
|
|
[28]
|
Chen B, Ho D W C, Zhang W, Yu L. Networked Fusion Estimation With Bounded Noises. IEEE Transactions on Automatic Control, 2017, 62(10): 5415-5421 doi: 10.1109/TAC.2017.2696746
|




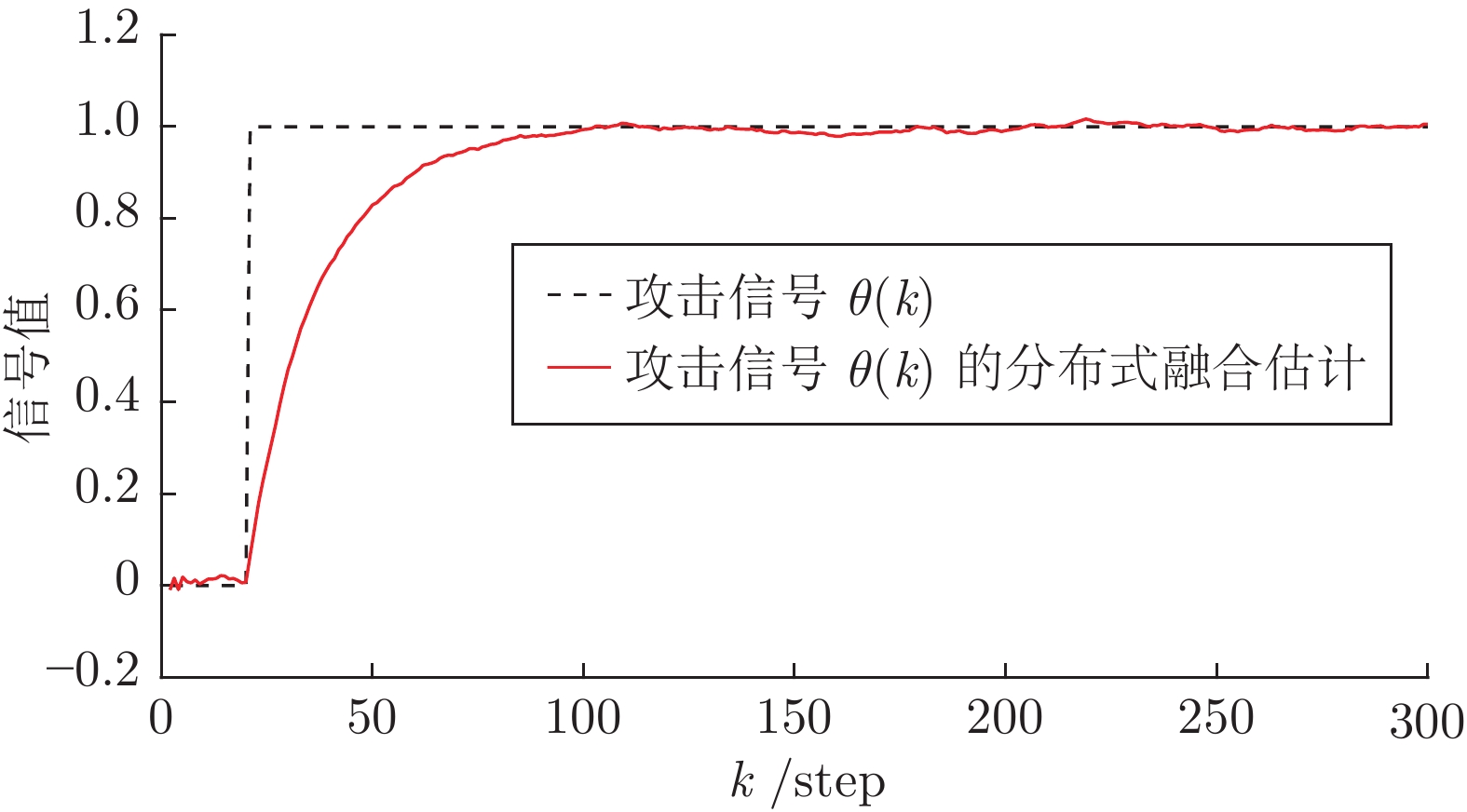
 下载:
下载: