-
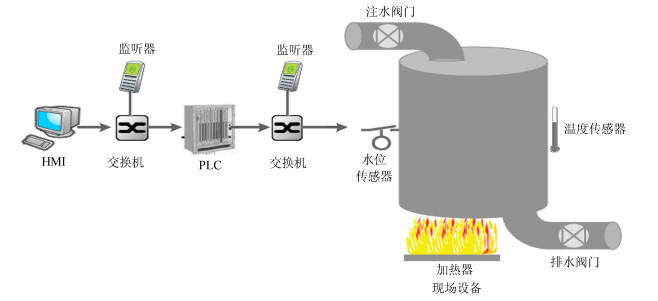
摘要: 针对工业控制系统中现有异常检测算法在语义攻击检测方面存在的不足, 提出一种基于混合马尔科夫树模型的异常检测算法, 充分利用工业控制系统的阶段性和周期性特征, 构建系统正常运行时的行为模型—混合马尔科夫树.该模型包含合法的状态事件、合法的状态转移、正常的概率分布以及正常的转移时间间隔等4种信息, 基于动态自适应的方法增强状态事件的关联度并引入时间间隔信息以实现对复杂语义攻击的检测, 语义建模时设计一种剪枝策略以去除模型中的低频事件、低转移事件以及冗余节点, 当被检测行为使得模型的以上4种信息产生的偏差超过阈值时, 判定该行为异常.最后, 基于OMNeT++网络仿真环境构建一个简化的污水处理系统对本文算法进行功能性验证, 并利用真实物理测试床的数据集对算法的检测准确度进行性能验证.验证结果表明, 本文算法能有效消除人机交互和常规诊断等操作带来的噪声影响, 对复杂语义攻击具有较高的检出率, 且能识别传统的非语义攻击.Abstract: Aiming at the problem that the existing anomaly detection algorithms in industrial control systems are insufficient in semantic attacks, an anomaly detection algorithm based on hybrid Markov tree model is proposed. The periodic characteristics of industrial control system is utilized to construct the system normal behavioral model at runtime— mixed-order Markov tree. The model includes four kinds of information: legal state events, legal state transition, normal probability distribution and normal transition time interval. Based on the dynamic adaptive method, the relation between state events are enhanced and the time interval information is added to realize the detection for more complex semantic attacks. When modeling, a pruning strategy is designed to remove low frequency events, low transition events and redundant nodes in the model. When the detected behavior makes the deviation of the above four kinds of information of the model exceed the threshold, the system detects the anomaly. Finally, a simplified sewage treatment system based on OMNeT++ network simulation environment is constructed to verify the function of the proposed algorithm, and a data set of a real physical testbed is used to verify the detection accuracy of the algorithm. Experimental results show that the proposed algorithm can effectively eliminate the noise of human interaction and normal diagnosis, and has high detection rate for complex semantic attacks and can also identify traditional non-semantic attacks.
-
Key words:
- Industrial control system (ICS) /
- semantic attacks /
- anomaly detection /
- mix-order Markov tree model
1) 本文责任编委 袁勇 -
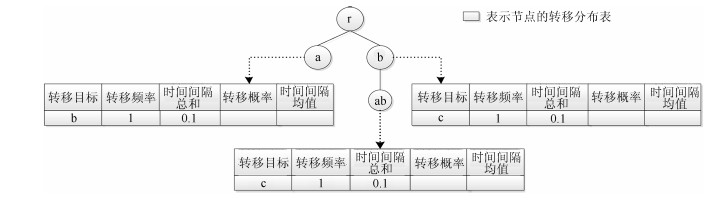
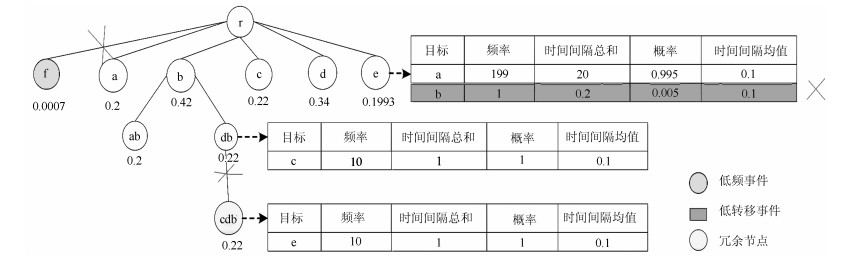
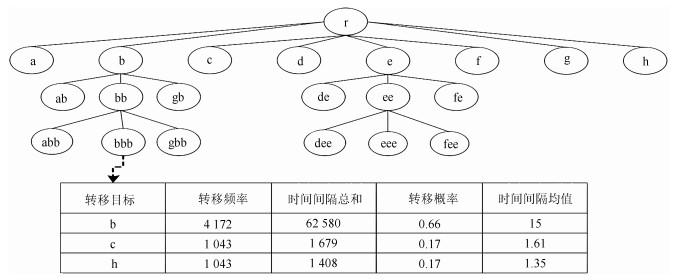
表 1 节点b转移分布表
Table 1 The transfer table of node "b"
转移目标 转移频率 转移概率 时间间隔总和 时间间隔均值 c 3 0.5 0.3 ms 0.1 ms e 3 0.5 0.3 ms 0.1 ms 表 2 各模型攻击检测结果对比
Table 2 Comparison of detection results of each method
检测模型 功能码异常攻击 缓冲区溢出攻击 Order-based语义攻击 Time-based语义攻击 分支节点语义攻击 周期性语义攻击 DFA 检测成功 检测成功 检测成功 检测失败 检测失败 检测失败 DTMC 检测成功 检测成功 检测成功 检测成功 检测失败 检测失败 PST 检测成功 检测成功 检测成功 检测失败 检测成功 检测失败 MMTM 检测成功 检测成功 检测成功 检测成功 检测成功 检测成功 表 3 误报率评估
Table 3 False positive rate evaluation
交互控制层 MMTM DFA DTMC PST HMI-PLCs 1.21 % 1.28 % 1.197 % 1.208 % PLC1-现场设备 0.85 % 1.151 % 0.83 % 0.828 % PLC2-现场设备 0.93 % 1.226 % 0.921 % 0.93 % PLC3-现场设备 1.124 % 1.205 % 1.12 % 1.108 % PLC4-现场设备 1.09 % 1.199 % 0.97 % 1.05 % PLC5-现场设备 1.075 % 1.27 % 1.066 % 1.073 % PLC6-现场设备 0.974 % 1.13 % 0.97 % 0.97 % 表 4 漏报率评估
Table 4 False negative rate evaluation
交互控制层} 剪枝前
MMTM剪枝后
MMTMDFA DTMC PST HMI-PLCs 0.694 % 0.58 % 1.328 % 1.10 % 1.093 % PLC1-现场设备 0.498 % 0.432 % 1.124 % 0.995 % 1.01 % PLC2-现场设备 0.607 % 0.55 % 1.301 % 1.027 % 1.02 % PLC3-现场设备 0.778 % 0.501 % 1.48 % 1.139 % 1.115 % PLC4-现场设备 0.41 % 0.329 % 1.119 % 0.971 % 1.13 % PLC5-现场设备 0.492 % 0.47 % 1.138 % 0.89 % 1.011 % PLC6-现场设备 0.197 % 0.203 % 0.897 % 0.704 % 0.703 % -
[1] Barbosa R R R, Sadre R, Pras A. Towards periodicity based anomaly detection in SCADA networks. In: Proceedings of IEEE 17th Conference on Emerging Technologies & Factory Automation. Krakow, Poland: IEEE, 2012. 1-4 [2] Hadžiosmanović D, Sommer R, Zambon E, Hartel P H. Through the eye of the PLC: semantic security monitoring for industrial processes. In: Proceedings of the 30th Annual Computer Security Applications Conference. New Orleans, Louisiana, USA: ACM, 2014. 126-135 [3] Falliere N, Murchu L O, Chien E. W32. Stuxnet Dossier. White Paper, 2011 [4] Caselli M, Zambon E, Kargl F. Sequence-aware intrusion detection in industrial control systems. In: Proceedings of the 1st ACM Workshop on Cyber-Physical System Security. Singapore, Republic of Singapore: ACM, 2015. 13-24 [5] Fovino I N, Carcano A, De Lacheze Murel T, Trombetta A, Masera M. Modbus/DNP3 state-based intrusion detection system. In: Proceedings of the 24th IEEE International Conference on Advanced Information Networking and Applications. Perth, WA: IEEE, 2010. 729-736 [6] Ellis J, Fisher D, Longstaff T A, Pesante L, Pethia R D. Report to the President's Commission on Critical Infrastructure Protection, Special Report CMU/SEI-97-SR-003, Carnegie Mellon University, Pittsburgh, PA, 1997. [7] Almaö G. Comparison of robust regression methods in linear regression. International Journal of Contemporary Mathematical Sciences, 2011, 6(9): 409-421 [8] 叶石罡.数据挖掘技术在AVC系统分析中的应用研究[硕士学位论文], 华南理工大学, 中国, 2014Ye Shi-Gang. Application of Data Mining Techniques in the AVC System Analysis[Master thesis], South China University of Technology, China, 2014 [9] Jiang J M, Yasakethu L. Anomaly detection via one class SVM for protection of SCADA systems. In: Proceedings of the 2013 International Conference on Cyber-Enabled Distributed Computing and Knowledge Discovery. Beijing, China: IEEE, 2013. 82-88 [10] Zhao J, Liu K, Wang W, Liu Y. Adaptive fuzzy clustering based anomaly data detection in energy system of steel industry. Information Sciences, 2014, 259: 335-345 doi: 10.1016/j.ins.2013.05.018 [11] 黄勇.面向ICS的异常检测系统研究[硕士学位论文], 重庆理工大学, 中国, 2014Huang Yong. Research of Anomaly detection system for Industrial Control System[Master thesis], Chongqing University of Technology, China, 2014 [12] 刘强, 秦泗钊.过程工业大数据建模研究展望.自动化学报, 2016, 42(2): 161-171 doi: 10.16383/j.aas.2016.c150510Liu Qiang, Qin S Joe. Perspectives on big data modeling of process industries. Acta Automatica Sinica, 2016, 42(2): 161-171 doi: 10.16383/j.aas.2016.c150510 [13] Nivethan J, Papa M. A SCADA intrusion detection framework that incorporates process semantics. In: Proceedings of the 11th Annual Cyber and Information Security Research Conference. Oak Ridge, TN, USA: ACM, 2016. Article No.6 [14] Goldenberg N, Wool A. Accurate modeling of Modbus/TCP for intrusion detection in SCADA systems. International Journal of Critical Infrastructure Protection, 2013, 6(2): 63-75 doi: 10.1016/j.ijcip.2013.05.001 [15] Kleinmann A, Wool A. A statechart-based anomaly detection model for multi-threaded SCADA systems. In: Proceedings of International Conference on Critical Information Infrastructures Security. Berlin, Germany: Springer International Publishing, 2015. 132-144 [16] 潘洪跃.基于MODBUS协议通信的设计与实现.计量技术, 2002, (4): 37-38 doi: 10.3969/j.issn.1000-0771.2002.04.014Pan Hong-Yue. Design and implementation of communication based on MODBUS protocol. Measurement Technique, 2002, (4): 37-38 doi: 10.3969/j.issn.1000-0771.2002.04.014 [17] Adepu S, Mathur A. From design to invariants: detecting attacks on cyber physical systems. In: Proceedings of the 2017 IEEE International Conference on Software Quality, Reliability and Security Companion. Prague, Czech Republic: IEEE, 2017. 533-540 [18] 李晓航, 朱芳来.延迟不确定马尔科夫跳变系统的执行器和传感器故障同时估计方法.自动化学报, 2017, 43(1): 72-82 doi: 10.16383/j.aas.2017.c150389Li Xiao-Hang, Zhu Fang-Lai. Simultaneous estimation of actuator and sensor faults for uncertain time-delayed Markovian jump systems. Acta Automatica Sinica, 2017, 43(1): 72-82 doi: 10.16383/j.aas.2017.c150389 [19] 杨新旭, 王长山, 王东琦, 郑丽娜.基于隐马尔可夫模型的入侵检测系统.计算机工程与应用, 2005, 41(12): 149-151 doi: 10.3321/j.issn:1002-8331.2005.12.046Yang Xin-Xu, Wang Chang-Shan, Wang Dong-Qi, Zheng Li-Na. An intrusion detection system based on hidden Markov model. Computer Engineering and Applications, 2005, 41(12): 149-151 doi: 10.3321/j.issn:1002-8331.2005.12.046 [20] Kleinmann A, Wool A. Automatic construction of statechart-based anomaly detection models for multi-threaded industrial control systems. ACM Transactions on Intelligent Systems and Technology, 2017, 8(4): Article No.55 [21] Begleiter R, El-Yaniv R, Yona G. On prediction using variable order Markov models. Journal of Artificial Intelligence Research, 2004, 22(1): 385-421 http://d.old.wanfangdata.com.cn/OAPaper/oai_arXiv.org_1107.0051 [22] 郑琪, 蒋盛益, 汤庸.概率后缀树在入侵检测中的应用研究.计算机工程与应用, 2010, 46(23): 79-81 doi: 10.3778/j.issn.1002-8331.2010.23.022Zheng Qi, Jiang Sheng-Yi, Tang Yong. Applying probabilistic suffix tree to intrusion detection. Computer Engineering and Applications, 2010, 46(23): 79-81 doi: 10.3778/j.issn.1002-8331.2010.23.022 [23] Yoon M K, Ciocarlie G F. Communication pattern monitoring: improving the utility of anomaly detection for industrial control systems. In: The Workshop on Security of Emerging Networking Technologies. San Diego, CA, USA, 2014. [24] Varga A. The OMNET++ discrete event simulation system. 2001. [25] Goh J, Adepu S, Junejo K N, Mathur A. A dataset to support research in the design of secure water treatment systems. In: Proceedings of the 11th International Conference on Critical Information Infrastructures Security. Paris, France, 2016. [26] Secure Water Treatment[Online], available: http://itrust.sutd.edu.sg/research/testbeds/secure-water-treatment-swat/, September 2017. -





 下载:
下载: