-
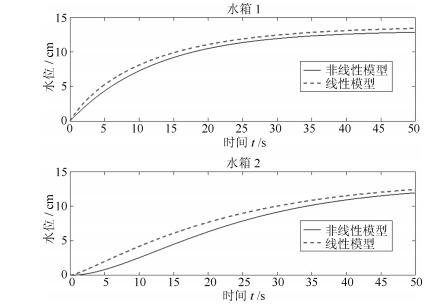
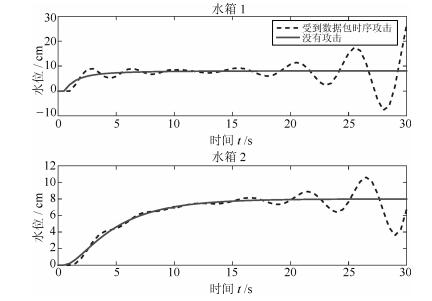
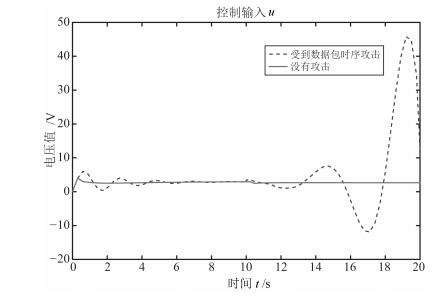
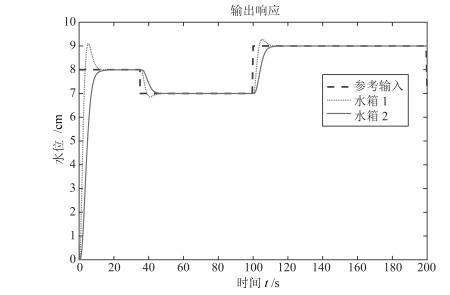
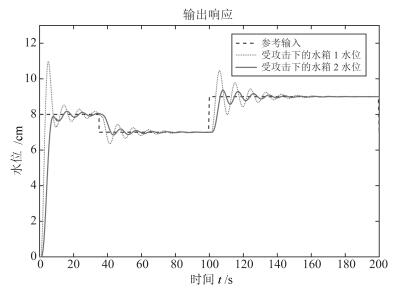
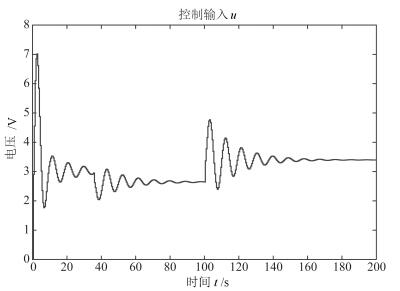
摘要: 对于远程复杂的操控系统,信息物理融合系统(Cyber-physical system,CPS)主要依靠无线网络实现从传感器到控制器,从控制器到执行器间的信息传输,由于其依靠网络传输数据的特性使其控制系统极易遭到安全威胁.本文从物理系统入手,意图保护CPS系统中物理实体的正常运行不受由于恶意攻击造成网络空间入侵带来的干扰.以受到数据包时序攻击的信息物理融合系统为研究对象,将其安全性研究抽象为一个博弈过程,基于非合作博弈的两人零和博弈模型,设计了可变延迟情况下鲁棒输出反馈的极大极小控制器.并且采用参数化的软约束二次型目标函数,在控制器设计时引入干扰衰减因子γ,通过对γ的取值使得二次型目标函数取极小值,从而保证了最差情况下的稳定控制,在满足γ的约束条件下,本文通过粒子群搜索算法得出γ的值.另外,本文还对所设计的极大极小控制器,与线性二次型高斯(Linear quadratic Gaussian,LQG)控制对比分析,用双水箱系统进行了仿真验证,发现在受攻击情况下本文所设计的控制器最终能够实现稳定控制,而LQG却不能.Abstract: As a remote control system, the cyber-physical system (CPS) relies mainly on wireless networks to realize the transmission of information from sensors to controllers and from controllers to actuators. Because of this characteristic, the control system of CPS is vulnerable to security threats. Starting with physical devices, the aim of this paper is to protect normal operation of physical entities in CPS system from the interference of network intrusion caused by malicious attacks. Taking the cyber-physical systems suffered packets scheduling attacks into consideration, its secure control was abstracted as a process of two person zero sum game. Based on two person zero sum model of non-cooperative game, the paper designed a min-max controller with a robust output-feedback under time-varying delays. In this paper, a parameterized soft constraint quadratic objective function was adopted. Also, interference attenuation factor γ was introduced in the controller design and the minimum value of the quadratic objective function was determined by the value of γ which guaranteed the stability control under the worst case. Within the constraint of γ, we get the value of γ through particle swarm search algorithm. In addition, the min-max controller is analyzed and compared with the linear quadratic Gaussian (LQG) control, and the simulation was conducted on a two tanks system. The result showed that the min-max controller can stabilize the attacked system, but LQG cannot.1) 本文责任编委 许斌
-
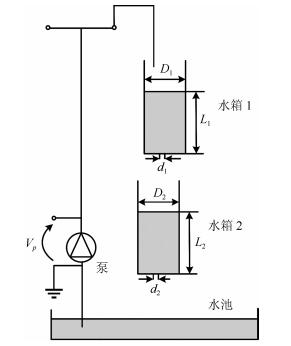
表 1 水箱参数
Table 1 Water tank equipment parameters
名称 参数大小 设备质量 6.6 kg 模型尺寸$(H\times W\times L)$ 30.5 cm$\times$ 30.5 cm$\times$ 91.5 cm 泵流量常数 3.3 cm$^3$/(V$\cdot$s) 压力传感器灵敏度 6.1 cm/V 水箱高度 30 cm 水箱内部直径 4.45 cm 流出孔直径 0.48 cm -
[1] Guan X P, Yang B, Chen C, Dai W, Wang Y. A comprehensive overview of cyber-physical systems:from perspective of feedback system. IEEE/CAA Journal of Automatica Sinica, 2016, 3(1):1-14 [2] 王中杰, 谢璐璐.信息物理融合系统研究综述.自动化学报, 2011, 37(10):1157-1166 http://www.aas.net.cn/CN/abstract/abstract17604.shtmlWang Zhong-Jie, Xie Lu-Lu. Cyber-physical systems:a survey. Acta Automatica Sinica, 2011, 37(10):1157-1166 http://www.aas.net.cn/CN/abstract/abstract17604.shtml [3] Hespanha J P, Naghshtabrizi P, Xu Y. A survey of recent results in networked control systems. Proceedings of the IEEE, 2007, 95(1):138-162 http://www.wanfangdata.com.cn/details/detail.do?_type=perio&id=e47d717e96da82596eb9456b53ba7d81 [4] Cetinkaya A, Ishii H, Hayakawa T. Networked control under random and malicious packet losses. IEEE Transactions on Automatic Control, 2017, 62(5):2434-2449 doi: 10.1109/TAC.2016.2612818 [5] Fawzi H, Tabuada P, Diggavi S. Secure estimation and control for cyber-physical systems under adversarial attacks. IEEE Transactions on Automatic Control, 2014, 59(6):1454-1467 doi: 10.1109/TAC.2014.2303233 [6] Jiang Y, Yin S. Recursive total principle component regression based fault detection and its application to vehicular cyber-physical systems. IEEE Transactions on Industrial Infoslatics, 2018, 14(4):1415-1423 doi: 10.1109/TII.2017.2752709 [7] Wang E K, Ye Y M, Xu X F, Chow K P. Security issues and challenges for cyber physical system. In: Green Computing and Communications (GreenCom), 2010 IEEE/ACM Int'l Conference on and Int'l Conference on Cyber, Physical and Social Computing (CPSCom). New York, USA: IEEE, 2010. 733-738 [8] 彭超宇.基于模型检验的信息物理融合系统安全性研究[硕士学位论文], 南京邮电大学, 2015 http://cdmd.cnki.com.cn/Article/CDMD-10293-1015730982.htmPeng Chao-Yu. Research on Security of Model Checking-based Cyber-Physical Systems[Master thesis], Nanjing University of Posts And Telecommunications, 2015 http://cdmd.cnki.com.cn/Article/CDMD-10293-1015730982.htm [9] 丁超, 杨立君, 吴蒙. IoT/CPS的安全体系结构及关键技术.中兴通讯技术, 2011, 17(1):11-16 doi: 10.3969/j.issn.1009-6868.2011.01.004Ding Chao, Yang Li-Jun, Wu Meng. Security architecture and key technologies for IoT/CPS. ZTE Technology Journal, 2011, 17(1):11-16 doi: 10.3969/j.issn.1009-6868.2011.01.004 [10] Amin S, Cárdenas A A, Sastry S S. Safe and secure networked control systems under denial-of-service attacks. In: Proceedings of International Conference on Hybrid Systems: Computation and Control. Heidelberg, Berlin, Germany: Springer, 2009. 31-45 [11] Gupta A, Langbort C, Basar T. Optimal control in the presence of an intelligent jammer with limited actions. In: Proceedings of the Decision and Control (CDC) 49th IEEE Conference. New York, USA: IEEE, 2010. 1096-1101 [12] Pang Z H, Liu G P, Dong Z. Secure networked control systems under denial of service attacks. In: Proceedings of the 18th IFAC World Congress, Milano, Italy: 2011. 8908-8913 [13] Sinopoli B, Schenato L, Franceschetti M, Poolla K, Jordan M I, Sastry S S. Kalman filtering with inteslittent observations. IEEE Transactions on Automatic Control, 2004, 49(9):1453-1464 doi: 10.1109/TAC.2004.834121 [14] Li X, Sun S. Robust H∞, Control for networked systems with random packet dropouts and time delays. Procedia Engineering, 2012, 29:4192-4197 doi: 10.1016/j.proeng.2012.01.642 [15] Moon J, Basar T. Control over TCP-like lossy networks: A dynamic game approach. In: Proceedings of the American Control Conference. New York, USA: IEEE, 2013. 1578-1583 [16] 史明光, 陈无畏.基于博弈论的H2/H∞混合控制及其在汽车主动悬架中的应用.控制理论与应用, 2005, 22(6):882-888 doi: 10.3969/j.issn.1000-8152.2005.06.007Shi Ming-Guang, Chen Wu-Wei. Mixed H2/H∞ control based on game theory and its application to the vehicle active suspension system. Control Theory and Applications, 2005, 22(6):882-888 doi: 10.3969/j.issn.1000-8152.2005.06.007 [17] 祝超群, 郭戈.事件驱动的网络化系统最优控制.控制与决策, 2014, 29(5):802-808 http://d.old.wanfangdata.com.cn/Periodical/kzyjc201405005Zhu Chao-Qun, Guo Ge. Optimal control for eventtriggered networked control systems. Control and Decision, 2014, 29(5):802-808 http://d.old.wanfangdata.com.cn/Periodical/kzyjc201405005 [18] 李海涛, 唐功友, 马慧.一类具有数据包丢失的网络控制系统的最优控制.控制与决策, 2009, 24(5):773-776 doi: 10.3321/j.issn:1001-0920.2009.05.026Li Hai-Tao, Tang Gong-You, Ma Hui. Optimal control for a class of networked control systems with data packet dropout. Control and Decision, 2009, 24(5):773-776 doi: 10.3321/j.issn:1001-0920.2009.05.026 [19] Shoukry Y, Araujo J, Tabuada P, Srivastava Me, Johansson K H. Minimax control for cyber-physical systems under network packet scheduling attacks. In: Proceedings of the 2nd ACM International Conference on High Confidence Networked Systems. New York, USA: ACM, 2013. 93-100 [20] Basar T, Bernhard P. H∞-optimal Control and Related Minimax Design Problems: a Dynamic Game Approach. Springer Science and Business Media, Birkhäuser Boston, 2008. [21] 张芬.基于最优控制的微分博弈问题研究[硕士学位论文], 云南师范大学, 2015. http://cdmd.cnki.com.cn/Article/CDMD-10681-1015809014.htmZhang Fen. Research The Problem of Differential Games Based on The Optimal Control[Master thesis], Yunnan Normal University, 2015. http://cdmd.cnki.com.cn/Article/CDMD-10681-1015809014.htm [22] Araújo J. Design, Implementation and Validation of Resource-Aware and Resilient Wireless Networked Control Systems[Ph.D. dissertation], KTH Royal Institute of Technology, 2014. [23] Garone E, Sinopoli B, Goldsmith A, Casavola A. LQG control for MIMO systems over multiple erasure channels with perfect acknowledgment. IEEE Transactions on Automatic Control, 2012, 57(2):450-456 doi: 10.1109/TAC.2011.2167789 [24] Changela M, Kumar A. Designing a controller for two tank interacting system. International Journal of Science and Research (IJSR), 2015, 5(4):589-593 [25] 温景容, 武穆清, 宿景芳.信息物理融合系统.自动化学报, 2012, 38(4):507-517 http://www.aas.net.cn/CN/abstract/abstract17704.shtmlWen Jing-Rong, Wu Mu-Qing, Su Jing-Fang. Cyber-physical System. Acta Automatica Sinica, 2012, 38(4):507-517 http://www.aas.net.cn/CN/abstract/abstract17704.shtml -




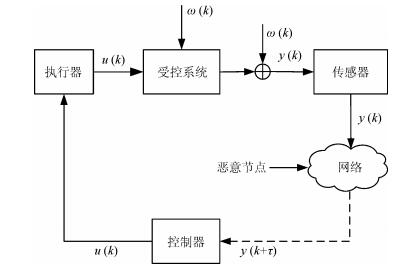
 下载:
下载: