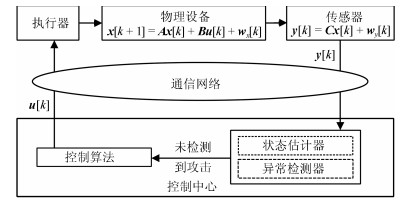
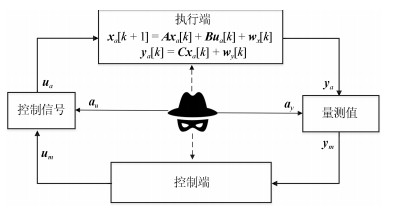
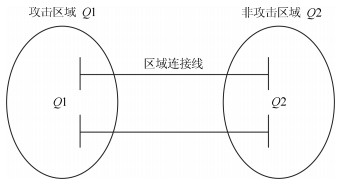
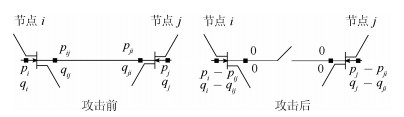
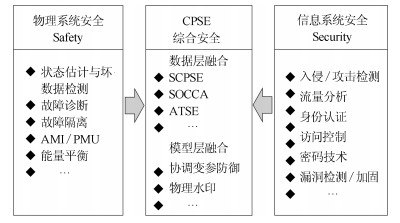
-
摘要: 信息物理融合系统(Cyber-physical system,CPS)是计算单元与物理对象在网络空间中高度集成交互形成的智能系统.信息系统与物理系统的融合在提升系统性能的同时,信息系统的信息安全威胁(Security)与物理系统的工程安全问题(Safety)相互影响,产生了新的综合安全问题,引入严重的安全隐患.本文介绍了CPS的概念与安全现状,给出了CPS综合安全的定义;在对现有安全事件进行分析的基础上,提出了CPS的综合安全威胁模型;从时间关联性和空间关联性的角度,对现有CPS攻击和防御方法进行了分类和总结,并探讨CPS综合安全的研究方向.Abstract: Cyber-physical system (CPS) is an intelligent system consisting of computing units and physical objects that highly interact with each other through the network. The combination of cyber system and physical system is promoting the performance of the CPS. At the same time, it also introduces a new integrated security threat into CPS, which combines engineering safety threat of physical system and information security threat of cyber system. In this paper, concepts and security status of CPS are introduced, and the concept of CPS integrated security is defined. After analyzing several existing security accidents in CPS, a new threat model of CPS integrated security is proposed. Existing CPS attacks and defense methods are classified and summarized from a perspective of temporal and spatial correlation. The future research of CPS integrated security is discussed.
-
Key words:
- Cyber-physical system (CPS) /
- integrated security /
- threat model /
- integrated defense
1) 本文责任编委 吕宜生 -
表 1 时间隐蔽型攻击对比
Table 1 Time concealment attack contrast
攻击类别 攻击者先验知识 读写权限 隐蔽性 零动态攻击 矩阵$A$、$B$与$C$ 大部分控制指令读权限与写权限 隐蔽 局部零动态攻击 $A_{11}$、$A_{21}$、$B_1$以及$C_1$ 大部分控制指令读权限与写权限 隐蔽 零状态诱导攻击 矩阵$A$、$B$与$C$ 大部分控制指令读权限与写权限 隐蔽 表 2 空间—时间隐蔽型攻击对比
Table 2 Space—time stealth attack contrast
攻击类别 攻击者先验知识 读写权限 隐蔽性 Stuxnet重放攻击 不需要 部分控制指令写权限, 全部量测信号的读写权限 隐蔽 量测量无关攻击 矩阵$A$、$B$与$C$ 部分或全部控制指令读写权限, 全部量测信号的读写权限 隐蔽 系统模拟攻击 矩阵$A$、$B$、$C$、$Q$与$R$系统初始状态$\pmb{x}[0]$ 部分或没有控制指令的读写权限, 全部量测值的读写权限 隐蔽 -
[1] National Institute of Standards and Technology, Framework for Cyber-Physical Systems. Cyber Physical Systems PWG, 2015. [2] 中华人民共和国国务院.中国制造2025.北京:中华人民共和国国务院, 2015State Council of the People's Republic of China. Made in China 2025 Strategy. Beijing:State Council of the PRC, 2015. [3] 管晓宏, 赵千川, 贾庆山, 吴江, 刘烃.信息物理融合能源系统.北京:科学出版社, 2016.Guan Xiao-Hong, Zhao Qian-Chuan, Jia Qing-Shan, Wu Jiang, Liu Ting. Cyber-Physical Energy System. Beijing:Science Press, 2016. [4] Marburger J H, Kvamme E F, Scalise G, Feed D A. Leadership under Challenge: Information Technology R & D in A Competitive World. An Assessment of the Federal Networking and Information Technology R & D Program. Washington, DC, USA: PCAST, 2007. [5] Khaitan S K, McCalley J D. Design techniques and applications of cyberphysical systems:A survey. IEEE Systems Journal, 2015, 9(2):350-365 doi: 10.1109/JSYST.2014.2322503 [6] Kagermann H, Wahlster W, Helbig J. Recommendations for implementing the strategic initiative INDUSTRIE 4.0: securing the future of German manufacturing industry; final report of the Industrie 4.0 Working Group. Germany: Forschungsunion, 2013. [7] 王中杰, 谢璐璐.信息物理融合系统研究综述.自动化学报, 2011, 37(10):1157-1166 http://www.aas.net.cn/CN/abstract/abstract17604.shtmlWang Zhong-Jie, Xie Lu-Lu. Cyber-physical systems:a survey. Acta Automatization Sinica, 2011, 37(10):1157-1166 http://www.aas.net.cn/CN/abstract/abstract17604.shtml [8] 中国信息物理系统发展论坛.信息物理系统白皮书[Online].获取自: https://www.innovation4.cn/library/r14012, 2018年5月25日China Cyber-Physical System Development Forum. Cyber-Physical System White Paper[Online], available: https://www.innovation4.cn/library/r14012, May 25, 2018 [9] Shakarian P. Stuxnet: cyberwar revolution in military affairs. 2011, DTIC Document. [10] Chen T M. Stuxnet, the real start of cyber warfare?[Editor's Note]. IEEE Network, 2010, 24(6): 2-3 [11] Falliere N, Murchu L O, Chien E. W32.Stuxnet Dossier (Version 1.4). Symantec Security Response, 2011. [12] Cherdantseva Y, Burnap P, Blyth A, Eden P, Jones K, Soulsby H, et al. A review of cyber security risk assessment methods for SCADA systems. Computers & Security, 2016, 56:1-27 http://www.wanfangdata.com.cn/details/detail.do?_type=perio&id=c3a9a92c96aacb8237b75416723d1386 [13] 汤奕, 陈倩, 李梦雅, 王琦, 倪明, 梁云.电力信息物理融合系统环境中的网络攻击研究综述.电力系统自动化, 2016, 40(17):59-69 http://d.old.wanfangdata.com.cn/Periodical/dlxtzdh201617009Tang Yi, Chen Qian, Li Meng-Ya, Wang Qi, Ni Ming, Liang Yun. Overview on cyber-attacks against cyber physical power system. Automation of Electric Power Systems, 2016, 40(17):59-69 http://d.old.wanfangdata.com.cn/Periodical/dlxtzdh201617009 [14] Staggs J, Ferlemann D, Shenoi S. Wind farm security:attack surface, targets, scenarios and mitigation. International Journal of Critical Infrastructure Protection, 2017, 17:3-14 doi: 10.1016/j.ijcip.2017.03.001 [15] Mo Y L, Sinopoli B. Secure control against replay attacks. In: Proceedings of the 47th Annual Allerton Conference on Communication, Control, and Computing. Monticello, USA: IEEE, 2009. 911-918 https://www.mendeley.com/catalogue/secure-control-against-replay-attacks/ [16] Lakshminarayana S, Teng T Z, Yau D K Y, Tan R. Optimal attack against cyber-physical control systems with reactive attack mitigation. In: Proceedings of the 8th ACM International Conference on Future Energy Systems. Hong Kong, China: ACM, 2017. 179-190 http://dl.acm.org/citation.cfm?id=3077852 [17] Weerakkody S, Mo Y L, Sinopoli B. Detecting integrity attacks on control systems using robust physical watermarking. In: Proceedings of the 53rd Annual Conference on Decision and Control (CDC). Los Angeles, USA: IEEE, 2014. 3757-3764 https://ieeexplore.ieee.org/document/7039974/ [18] Simon D. Kalman filtering with state constraints:a survey of linear and nonlinear algorithms. IET Control Theory & Applications, 2010, 4(8):1303-1318 https://ieeexplore.ieee.org/document/5540516 [19] Liang G Q, Weller S R, Zhao J H, Luo F J, Dong Z Y. The 2015 Ukraine blackout:implications for false data injection attacks. IEEE Transactions on Power Systems, 2017, 32(4):3317-3318 https://ieeexplore.ieee.org/document/7752958 [20] Liu Y, Ning P, Reiter M K. False data injection attacks against state estimation in electric power grids. In: Proceedings of the 16th ACM Conference on Computer and Communications Security. Chicago, USA: ACM, 2009. 21-32 https://www.mendeley.com/catalogue/false-data-injection-attacks-against-state-estimation-electric-power-grids/ [21] Liu Y, Ning P, Reiter M K. False data injection attacks against state estimation in electric power grids. ACM Transactions on Information and System Security, 2011, 14(1):Article No. 13 https://www.mendeley.com/catalogue/false-data-injection-attacks-against-state-estimation-electric-power-grids/ [22] Hug G, Giampapa J A. Vulnerability assessment of ac state estimation with respect to false data injection cyber-attacks. IEEE Transactions on Smart Grid, 2012, 3(3):1362-1370 doi: 10.1109/TSG.2012.2195338 [23] Yuan Y L, Li Z Y, Ren K. Modeling load redistribution attacks in power systems. IEEE Transactions on Smart Grid, 2011, 2(2):382-390 https://www.mendeley.com/catalogue/modeling-load-redistribution-attacks-power-systems/ [24] Kim J, Tong L. On topology attack of a smart grid:undetectable attacks and countermeasures. IEEE Journal on Selected Areas in Communications, 2013, 31(7):1294-1305 doi: 10.1109/JSAC.2013.130712 [25] Sandberg H, Teixeira A, Johansson K H. On security indices for state estimators in power networks. In: Proceedings of the 1st Workshop on Secure Control Systems. Stockholm, Sweden: CPSWEEK, 2010. [26] Hendrickx J M, Johansson K H, Jungers R M, Sandberg H, Sou K C. Efficient computations of a security index for false data attacks in power networks. IEEE Transactions on Automatic Control, 2014, 59(12):3194-3208 doi: 10.1109/TAC.2014.2351625 [27] Teixeira A, Amin S, Sandberg H, Johansson K H, Sastry S S. Cyber security analysis of state estimators in electric power systems. In: Proceedings of the 49th IEEE Conference on Decision and Control (CDC). Atlanta, GA, USA: IEEE, 2010. 5991-5998 https://www.mendeley.com/catalogue/cyber-security-analysis-state-estimators-electric-power-systems/ [28] Teixeira A, Dán G, Sandberg H, Johansson K H. A cyber security study of a SCADA energy management system:stealthy deception attacks on the state estimator. IFAC Proceedings Volumes, 2011, 44(1):11271-11277 doi: 10.3182/20110828-6-IT-1002.02210 [29] Rahman M A, Mohsenian-Rad H. False data injection attacks with incomplete information against smart power grids. In: Proceedings of the 2012 IEEE Global Communications Conference (GLOBECOM). Anaheim, USA: IEEE, 2012. 3153-3158 https://ieeexplore.ieee.org/document/6503599 [30] Liu X, Li Z Y. Local load redistribution attacks in power systems with incomplete network information. IEEE Transactions on Smart Grid, 2014, 5(4):1665-1676 doi: 10.1109/TSG.2013.2291661 [31] Liu X, Li Z Y. False data attacks against ac state estimation with incomplete network information. IEEE Transactions on Smart Grid, 2017, 8(5):2239-2248 doi: 10.1109/TSG.2016.2521178 [32] Liu X, Li Z Y. Local topology attacks in smart grids. IEEE Transactions on Smart Grid, 2017, 8(6):2617-2626 doi: 10.1109/TSG.2016.2532347 [33] Yu Z H, Chin W L. Blind false data injection attack using PCA approximation method in smart grid. IEEE Transactions on Smart Grid, 2015, 6(3):1219-1226 doi: 10.1109/TSG.2014.2382714 [34] Markwood I, Liu Y, Kwiat K, Kamhoua C. Electric grid power flow model camouflage against topology leaking attacks. In: Proceedings of the 2017 Conference on Computer Communications (INFOCOM). Atlanta, USA: IEEE, 2017. 1-9 https://ieeexplore.ieee.org/document/8057060 [35] Chen Y, Kar S, Moura J M F. Dynamic attack detection in cyber-physical systems with side initial state information. IEEE Transactions on Automatic Control, 2017, 62(9):4618-4624 doi: 10.1109/TAC.2016.2626267 [36] Teixeira A, Shames I, Sandberg H, Johansson K H. A secure control framework for resource-limited adversaries. Automatica, 2012, 51:135-148 http://d.old.wanfangdata.com.cn/OAPaper/oai_arXiv.org_1212.0226 [37] Vu Q D, Tan R, Yau D K Y. On applying fault detectors against false data injection attacks in cyber-physical control systems. In: Proceedings of the 35th IEEE International Conference on Computer Communications (INFOCOM). San Francisco, USA: IEEE, 2016. 1-9. https://www.mendeley.com/catalogue/applying-fault-detectors-against-false-data-injection-attacks-cyberphysical-control-systems/ [38] Weerakkody S, Sinopoli B. Detecting integrity attacks on control systems using a moving target approach. In: Proceedings of the 54th IEEE Conference on Decision and Control (CDC). Osaka, Japan: IEEE, 2015. 5820-5826 https://ieeexplore.ieee.org/document/7403134 [39] Satchidanandan B, Kumar P R. Dynamic watermarking:active defense of networked cyber-physical systems. Proceedings of the IEEE, 2017, 105(2):219-240 https://www.onacademic.com/detail/journal_1000039681235410_7f05.html [40] Sridhar S, Govindarasu M. Model-based attack detection and mitigation for automatic generation control. IEEE Transactions on Smart Grid, 2014, 5(2):580-591 http://d.old.wanfangdata.com.cn/NSTLQK/NSTL_QKJJ0231897321/ [41] Wang Q, Khurana H, Huang Y, Nahrstedt K. Time valid one-time signature for time-critical multicast data authentication. In: Proceedings of the 2009 IEEE Conference on Computer Communications (INFOCOM). Rio de Janeiro, Brazil: IEEE, 2009. 1233-1241 https://www.mendeley.com/catalogue/time-valid-onetime-signature-timecritical-multicast-data-authentication/ [42] Cao H Y, Zhu P D, Lu X C, Gurtov A. A layered encryption mechanism for networked critical infrastructures. IEEE Network, 2013, 27(1):12-18 http://www.wanfangdata.com.cn/details/detail.do?_type=perio&id=5cd41a41c9e212728c97abe483ee9f50 [43] Saxena N, Grijalva S. Efficient signature scheme for delivering authentic control commands in the smart grid. IEEE Transactions on Smart Grid, 2018, 9(5):4323-4334 doi: 10.1109/TSG.2017.2655014 [44] Kumar P, Braeken A, Gurtov A, Iinatti J, Ha P H. Anonymous secure framework in connected smart home environments. IEEE Transactions on Information Forensics and Security, 2017, 12(4):968-979 doi: 10.1109/TIFS.2016.2647225 [45] Zhang Y C, Wang L F, Sun W Q, Green Ⅱ R C, Alam M. Distributed intrusion detection system in a multi-layer network architecture of smart grids. IEEE Transactions on Smart Grid, 2011, 2(4):796-808 doi: 10.1109/TSG.2011.2159818 [46] Baig Z A. On the use of pattern matching for rapid anomaly detection in smart grid infrastructures. In: Proceedings of the 2011 IEEE International Conference on Smart Grid Communications (SmartGridComm). Brussels, Belgium: IEEE, 2011. 214-219 https://ieeexplore.ieee.org/document/6102321 [47] Palácios J M B, Garay J R B, Oliveira A M, Kofuji S T. Intrusion detection system:A hybrid approach for cyber-physical environments. Ciencia & Saude Coletiva, 2013, 269(2):2019-2021 [48] Bobba R B, Rogers K M, Wang Q Y, Khurana H, Overbye T J. Detecting false data injection attacks on DC state estimation. In: Proceedings of the 1st Workshop on Secure Control Systems. Stockholm, Sweden: University of Illinois Urbana-Champaign, 2010. https://www.mendeley.com/catalogue/detecting-false-data-injection-attacks-ac-state-estimation/ [49] Giani A, Bitar E, Garcia M, McQueen M, Khargonekar P, Poolla K. Smart grid data integrity attacks: characterizations and countermeasuresΠ. In: Proceedings of the 2011 IEEE International Conference on Smart Grid Communications (SmartGridComm). Brussels, Belgium: IEEE, 2011. 232-237 https://ieeexplore.ieee.org/document/6102324/ [50] Nuqui R F, Phadke A G. Phasor measurement unit placement techniques for complete and incomplete observability. IEEE Transactions on Power Delivery, 2005, 20(4):2381-2388 doi: 10.1109/TPWRD.2005.855457 [51] Qi J J, Sun K, Kang W. Optimal PMU placement for power system dynamic state estimation by using empirical observability Gramian. IEEE Transactions on Power Systems, 2015, 30(4):2041-2054 https://www.mendeley.com/catalogue/optimal-pmu-placement-power-system-dynamic-state-estimation-using-empirical-observability-gramian/ [52] Yang Q Y, An D, Yu W. On time desynchronization attack against IEEE 1588 protocol in power grid systems. In: Proceedings of the 2013 IEEE Energytech. Cleveland, USA: IEEE, 2013. 1-5 https://ieeexplore.ieee.org/document/6645332 [53] Zhang Z H, Gong S P, Dimitrovski A D, Li H S. Time synchronization attack in smart grid:impact and analysis. IEEE Transactions on Smart Grid, 2013, 4(1):87-98 doi: 10.1109/TSG.2012.2227342 [54] Jiang X C, Zhang J M, Harding B J, Makela J J, Domínguez-García A D. Spoofing GPS receiver clock offset of phasor measurement units. IEEE Transactions on Power Systems, 2013, 28(3):3253-3262 http://www.wanfangdata.com.cn/details/detail.do?_type=perio&id=69f28223f4edd176b9795e83a2d92f1a [55] Jafarnia-Jahromi A, Broumandan A, Nielsen J, Lachapelle G. GPS vulnerability to spoofing threats and a review of antispoofing techniques. International Journal of Navigation and Observation, 2012, 2012:Article No. 127072 http://d.old.wanfangdata.com.cn/OAPaper/oai_doaj-articles_03b5fa4fc35f0417b168ed476928e8b6 [56] Fan Y W, Zhang Z H, Trinkle M, Dimitrovski A D, Song J B, Li H S. A cross-layer defense mechanism against GPS spoofing attacks on PMUs in smart grids. IEEE Transactions on Smart Grid, 2015, 6(6):2659-2668 doi: 10.1109/TSG.2014.2346088 [57] Dán G, Sandberg H. Stealth attacks and protection schemes for state estimators in power systems. In: Proceedings of the 1st IEEE International Conference on Smart Grid Communications. Gaithersburg, USA: IEEE, 2010. 214-219 https://www.mendeley.com/catalogue/stealth-attacks-protection-schemes-state-estimators-power-systems/ [58] Huang Y, Li H S, Campbell K A, Han Z. Defending false data injection attack on smart grid network using adaptive CUSUM test. In: Proceedings of the 45th Annual Conference on Information Sciences and Systems (CISS). Baltimore, USA: IEEE, 2011. 1-6 https://www.mendeley.com/catalogue/defending-false-data-injection-attack-smart-grid-network-using-adaptive-cusum-test/ [59] Murguia C, Ruths J. CUSUM and chi-squared attack detection of compromised sensors. In: Proceedings of the 2016 IEEE Conference on Control Applications (CCA). Buenos Aires, Argentina: IEEE, 2016. 474-480 https://ieeexplore.ieee.org/document/7587875 [60] Liu L C, Esmalifalak M, Ding Q F, Emesih V A, Han Z. Detecting false data injection attacks on power grid by sparse optimization. IEEE Transactions on Smart Grid, 2014, 5(2):612-621 http://www.wanfangdata.com.cn/details/detail.do?_type=perio&id=6332463959730df1350bbc57ac5e4272 [61] Liu X X, Zhu P D, Zhang Y, Chen K. A collaborative intrusion detection mechanism against false data injection attack in advanced metering infrastructure. IEEE Transactions on Smart Grid, 2015, 6(5):2435-2443 doi: 10.1109/TSG.2015.2418280 [62] Gu C J, Jirutitijaroen P, Motani M. Detecting false data injection attacks in ac state estimation. IEEE Transactions on Smart Grid, 2015, 6(5):2476-2483 doi: 10.1109/TSG.2015.2388545 [63] Ashok A, Govindarasu M, Ajjarapu V. Online detection of stealthy false data injection attacks in power system state estimation. IEEE Transactions on Smart Grid, 2018, 9(3):1636-1646 https://ieeexplore.ieee.org/document/7526441 [64] Zonouz S, Rogers K M, Berthier R, Bobba R B, Sanders W H, Overbye T J. SCPSE:Security-oriented cyber-physical state estimation for power grid critical infrastructures. IEEE Transactions on Smart Grid, 2012, 3(4):1790-1799 doi: 10.1109/TSG.2012.2217762 [65] Zonouz S, Davis C M, Davis K R, Berthier R, Bobba R B, Sanders W H. SOCCA:a security-oriented cyber-physical contingency analysis in power infrastructures. IEEE Transactions on Smart Grid, 2014, 5(1):3-13 http://d.old.wanfangdata.com.cn/NSTLQK/NSTL_QKJJ0231677142/ [66] Wang Y, Xu Z Y, Zhang J L, Xu L, Wang H P, Gu G F. SRID: State relation based intrusion detection for false data injection attacks in SCADA. In: Proceedings of the 19th European Symposium on Research in Computer Security. Wroclaw, Poland: Springer, 2014. 401-418 doi: 10.1007/978-3-319-11212-1_23 [67] Liu T, Sun Y N, Liu Y, Gui Y H, Zhao Y C, Wang D, et al. Abnormal traffic-indexed state estimation:a cyber-physical fusion approach for Smart Grid attack detection. Future Generation Computer Systems, 2015, 49:94-103 doi: 10.1016/j.future.2014.10.002 [68] Liu T, Tian J, Gui Y H, Liu Y, Liu P F. SEDEA:state estimation-based dynamic encryption and authentication in smart grid. IEEE Access, 2017, 5:15682-15693 doi: 10.1109/ACCESS.2017.2713440 [69] Chong F, Lee R B, Vishik C, Acquisti A, Horne W, Palmer C, et al. National Cyber Leap Year Summit 2009: Co-chairs' Report. Arlington, Virginia, USA: Networking and Information Technology Research and Development Program (U.S.), 2009. [70] Jajodia S, Ghosh A K, Swarup V, Wang C, Wang X S. Moving Target Defense:Creating Asymmetric Uncertainty for Cyber Threats:Volume 54. New York, USA:Springer Science & Business Media, 2011. https://dl.acm.org/citation.cfm?coll=DL&dl=GUIDE&id=2038041 [71] Okhravi H, Hobson T, Bigelow D, Streilein W. Finding focus in the blur of moving-target techniques. IEEE Security & Privacy, 2014, 12(2):16-26 http://www.wanfangdata.com.cn/details/detail.do?_type=perio&id=6a5339ec75794f6832763a4ec1fdef1e [72] Carroll T E, Crouse M, Fulp E W, Berenhaut S. Analysis of network address shuffling as a moving target defense. In: Proceedings of the 2014 IEEE International Conference on Communications (ICC). Sydney, Australia: IEEE, 2014. 701-706 https://www.mendeley.com/catalogue/analysis-network-address-shuffling-moving-target-defense/ [73] 邬江兴.网络空间拟态防御研究.信息安全学报, 2016, 1(4):1-10 http://d.old.wanfangdata.com.cn/Periodical/xxaqxb201604001Wu Jiang-Xing. Research on cyber mimic defense. Journal of Cyber Security, 2016, 1(4):1-10 http://d.old.wanfangdata.com.cn/Periodical/xxaqxb201604001 [74] Morrow K L, Heine E, Rogers K M, Bobba R B, Overbye T J. Topology perturbation for detecting malicious data injection. In: Proceedings of the 45th Hawaii International Conference on System Sciences. Maui, USA: IEEE, 2012. 2104-113 https://ieeexplore.ieee.org/document/6149267/ [75] Davis K R, Morrow K L, Bobba R, Heine E. Power flow cyber attacks and perturbation-based defense. In: Proceedings of the 2012 IEEE Third International Conference on Smart Grid Communications (SmartGridComm). Tainan, China: IEEE, 2012. 342-347 https://ieeexplore.ieee.org/document/6486007 [76] Rahman M A, Al-Shaer E, Bobba R B. Moving target defense for hardening the security of the power system state estimation. In: Proceedings of the 1st ACM Workshop on Moving Target Defense. Scottsdale, USA: ACM, 2014. 59-68 https://www.deepdyve.com/lp/association-for-computing-machinery/moving-target-defense-for-hardening-the-security-of-the-power-system-XvR7JBirCd [77] Gyugyi L, Schauder C D, Sen K K. Static synchronous series compensator:a solid-state approach to the series compensation of transmission lines. IEEE Transactions on Power Delivery, 1997, 12(1):406-417 doi: 10.1109/61.568265 [78] Hoehn A, Zhang P. Detection of covert attacks and zero dynamics attacks in cyber-physical systems. In: Proceedings of the 2016 IEEE American Control Conference (ACC). Boston, USA: IEEE, 2016. 302-307 http://www.mendeley.com/catalog/detection-covert-attacks-zero-dynamics-attacks-cyberphysical-systems/ [79] Edris A, Adapa R, Baker M, Bohmann L, Clark K, Habashi K, et al. Proposed terms and definitions for flexible AC transmission system (FACTS). IEEE Transactions on Power Delivery, 1997, 12(4):1848-1853 doi: 10.1109/61.634216 [80] Divan D M, Brumsickle W E, Schneider R S, Kranz B, Gascoigne R W, Bradshaw D T, et al. A distributed static series compensator system for realizing active power flow control on existing power lines. IEEE Transactions on Power Delivery, 2006, 22(1):642-649 http://www.wanfangdata.com.cn/details/detail.do?_type=perio&id=6b74a9dab6f8dce35561bc99bea26669 [81] Teixeira A, Shames I, Sandberg H, Johansson K H. Revealing stealthy attacks in control systems. In: Proceedings of the 50th Annual Allerton Conference on Communication, Control, and Computing (Allerton). Monticello, USA: IEEE, 2012. 1806-1813 http://ieeexplore.ieee.org/xpls/icp.jsp?arnumber=6483441 [82] Kwon C, Hwang I. Hybrid robust controller design: cyber attack attenuation for cyber-physical systems. In: Proceedings of the 52nd IEEE Conference on Decision and Control (CDC). Florence, Italy: IEEE, 2013. 188-193 https://ieeexplore.ieee.org/document/6759880 [83] Weerakkody S, Ozel O, Griffioen P, Sinopoli B. Active detection for exposing intelligent attacks in control systems. In: Proceedings of the 2017 IEEE Conference on Control Technology and Applications (CCTA), Mauna Lani, HI, USA: IEEE, 2017. 1306-1312 https://www.onacademic.com/detail/journal_1000040218583510_ba0d.html [84] Weerakkody S, Sinopoli B. A moving target approach for identifying malicious sensors in control systems. In: Proceedings of the 54th Annual Allerton Conference on Communication, Control, and Computing (Allerton). Monticello, USA: IEEE, 2016. 1149-1156 https://ieeexplore.ieee.org/document/7852365 [85] Tian J, Tan R, Guan X H, Liu T. Hidden moving target defense in smart grids. In: Proceedings of the 2nd Workshop on Cyber-Physical Security and Resilience in Smart Grids. Pittsburgh, USA: IEEE, 2017. 21-26 [86] Tian J, Tan R, Guan X H, Liu T. Enhanced hidden moving target defense in smart grids. IEEE Transactions on Smart Grid, 2018, DOI: 10.1109/TSG.2018.2791512 [87] 尹浩, 林闯, 邱锋, 丁嵘.数字水印技术综述.计算机研究与发展, 2005, 42(7):1093-1099 http://d.old.wanfangdata.com.cn/Periodical/jsjyjyfz200507001Yin Hao, Lin Chuang, Qiu Feng, Ding Rong. A survey of digital watermarking. Journal of Computer Research and Development, 2005, 42(7):1093-1099 http://d.old.wanfangdata.com.cn/Periodical/jsjyjyfz200507001 [88] Hespanhol P, Porter M, Vasudevan R, Aswani A. Dynamic watermarking for general LTI systems. In: Proceedings of the 56th Annual Conference on Decision and Control (CDC). Melbourne, Australia: IEEE, 2017. 1834-1839 https://arxiv.org/abs/1703.07760 [89] Mo Y L, Garone E, Casavola A, Sinopoli B. False data injection attacks against state estimation in wireless sensor networks. In: Proceedings of the 49th IEEE Conference on Decision and Control (CDC). Atlanta, USA: IEEE, 2010. 5967-5972 https://www.mendeley.com/catalogue/false-data-injection-attacks-against-state-estimation-wireless-sensor-networks/ [90] Mo Y L, Chabukswar R, Sinopoli B. Detecting integrity attacks on SCADA systems. IEEE Transactions on Control Systems Technology, 2014, 22(4):1396-1407 https://www.sciencedirhttps://www.sciencedirect.com/science/article/pii/S1474667016454200ect.com/science/article/pii/S1474667016454200 [91] Weerakkody S, Ozel O, Sinopoli B. Bernoulli-Gaussian physical watermark for detecting integrity attacks in control systems. In: Proceedings of the 55th Annual Allerton Conference on Communication, Control, and Computing (Allerton), Monticello, IL, USA: IEEE, 2017. 966-973 https://arxiv.org/abs/1710.01105 [92] Mo Y L, Weerakkody S, Sinopoli B. Physical authentication of control systems:designing watermarked control inputs to detect counterfeit sensor outputs. IEEE Control Systems Magazine, 2015, 35(1):93-109 doi: 10.1109/MCS.2014.2364724 -





 下载:
下载: