-
摘要: 为了提高指纹模板算法的安全性等性能,设计了一种基于细节点邻域信息的可撤销指纹模板生成算法.首先对指纹图像进行预处理,提取指纹的细节点特征,然后采用改进的细节点描述子采样结构提取细节点邻域的纹线特征,最后结合用户PIN码生成指纹模板,同时结合贪婪算法设计了相应的指纹匹配算法.在指纹数据库FVC2002-DB1和DB2上的实验表明,该算法具有良好的认证性能,能较好地满足可撤销性、多样性和不可逆性,而且改进的采样结构在没有降低系统识别性能的情况下,进一步拓展了细节点描述子的采样结构方式.Abstract: It has become critical to improve the security of the fingerprint templates. This paper, we propose a cancelable fingerprint template based on minutiae local information. First, we extract fingerprint minutiae feature after the preprocessing, then we use the improved Tico sampling structure to extract texture feature of minutiae adjacent area. Finally, the fingerprint template is generated by combining the user PIN. Our design of fingerprint matching algorithm draws on the experience of greedy algorithm. The experiments results on FVC2002-DB1 and DB2 show that the algorithm not only achieves good recognition performance but also fulfills revocability, diversity and non-invertibility, and that without reducing system recognition performance, the improved sampling structure extends the sampling structure of minutiae description.
-
Key words:
- Minutiae /
- local information /
- cancelable template /
- fingerprint
1) 本文责任编委 封举富 -
表 1 FVC2002-DB1和FVC2002-DB2数据库参数
Table 1 Summary of databases used in our experiments
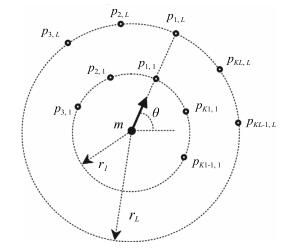
FVC2002-DB1 FVC2002-DB2 采集设备 Touch View Ⅱ FX2000 光学采集仪 光学采集仪 图像尺寸 388 × 374 296 × 560 手指数量 100 100 每枚手指采集次数 8 8 分辨率 500 dpi 596 dpi 图像质量 Good Medium 表 2 不同的采样圆环r与采样点个数K下的匹配结果
Table 2 EER of different sampling point structure around each minutiae for the same PIN (%)
采样点构造
(r1, K1), (r2, K2), …, (rL, KL)FVC2002-DB1
EERFVC2002-DB2
EER(42, 14), (60, 20), (78, 26) 8.12 7.33 (42, 14), (60, 20), (78, 26), (93, 32) 17.37 21.18 (27, 10), (45, 16), (63, 22), (81, 28) 12.14 11.54 (12, 14), (24, 18), (36, 24), (48, 28) 3.26 4.58 表 3 不同方法的性能对比 (EER)(%)
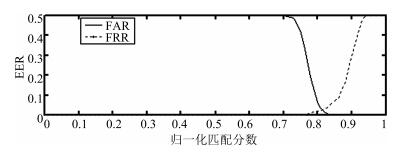
Table 3 EER comparison between proposed method and some existing methods (%)
表 4 采用均匀采样方法和本文提出方法的性能比较 (EER) (%)
Table 4 EER comparison between the method of uniform sampling structure and proposed method (%)
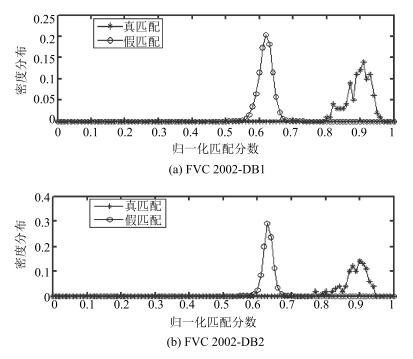
方法 用户PIN码安全 用户PIN码泄露 DB1 DB2 DB1 DB2 均匀采样 0 0 4.97 6.31 本文方法 0.02 0 3.26 4.58 表 5 真、假匹配分布的均值与方差
Table 5 The mean and standard deviations of the distributions
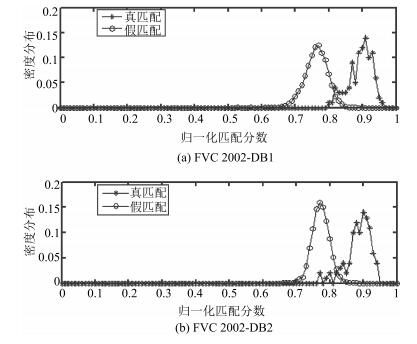
指纹数据库 相同PIN码的真匹配 相同PIN码的假匹配 不同PIN码的假匹配 伪假匹配 均值 方差 均值 方差 均值 方差 均值 方差 FVC2002-DB1 0.8940 1.24 × 10-3 0.7624 1.18 × 10-3 0.6186 4.31 × 10-4 0.6254 4.97 × 10-4 FVC2002-DB2 0.8860 1.30 × 10-3 0.7731 6.23 × 10-4 0.6312 1.98 × 10-4 0.6294 3.52 × 10-4 表 6 不同方法的假匹配分布的均值与方差 (FVC2002-DB2)
Table 6 The mean and standard deviations of the different methods imposter distributions for FVC2002-DB2
-
[1] 田捷, 杨鑫.生物特征识别理论与应用.北京:清华大学出版社, 2009. http://www.cnki.com.cn/Article/CJFDTOTAL-SYQY201603027.htmTian Jie, Yang Xin. Biometric Recognition Theory and Application. Beijing:Publishing House of Tsinghua University, 2009. http://www.cnki.com.cn/Article/CJFDTOTAL-SYQY201603027.htm [2] Cao K, Jain A K. Learning fingerprint reconstruction:from minutiae to image. IEEE Transactions on Information Forensics and Security, 2015, 10(1):104-117 doi: 10.1109/TIFS.2014.2363951 [3] 岳峰, 左旺孟, 张大鹏.掌纹识别算法综述.自动化学报, 2010, 36(3):353-365 http://www.aas.net.cn/CN/abstract/abstract13675.shtmlYue Feng, Zuo Wang-Meng, Zhang Da-Peng. Survey of palmprint recognition algorithms. Acta Automatica Sinica, 2010, 36(3):353-365 http://www.aas.net.cn/CN/abstract/abstract13675.shtml [4] Rane S, Wang Y, Draper S C, Ishwar P. Secure biometrics:concepts, authentication architectures, and challenges. IEEE Signal Processing Magazine, 2013, 30(5):51-64 doi: 10.1109/MSP.2013.2261691 [5] Ratha N K, Chikkerur S, Connell J H, Bolle R M. Generating cancelable fingerprint templates. IEEE Transactions on Pattern Analysis and Machine Intelligence, 2007, 29(4):561-572 doi: 10.1109/TPAMI.2007.1004 [6] Feng Q, Su F, Cai A N, Zhao F F. Cracking cancelable fingerprint template of Ratha. In:Proceedings of the 2008 International Symposium on Computer Science and Computational Technology. Shanghai, China:IEEE, 2008. 572-575 [7] Ang R, Safavi-Naini R, McAven L. Cancelable key-based fingerprint templates. In:Proceedings of the 10th Australasian Conference on Information Security and Privacy. Berlin Heidelberg, Germany:Springer, 2005. 242-252 [8] Teoh A B J, Ling D N C, Goh A. Biohashing:two factor authentication featuring fingerprint data and tokenised random number. Pattern Recognition, 2004, 37(11):2245-2255 doi: 10.1016/j.patcog.2004.04.011 [9] Kong A, Cheung K H, Zhang D, Kamel M, You J. An analysis of BioHashing and its variants. Pattern Recognition, 2006, 39(7):1359-1368 doi: 10.1016/j.patcog.2005.10.025 [10] Lee C, Choi J Y, Toh K A, Lee S, Kim J. Alignment-free cancelable fingerprint templates based on local minutiae information. IEEE Transactions on Systems, Man, and Cybernetics, Part B:Cybernetics, 2007, 37(4):980-992 doi: 10.1109/TSMCB.2007.896999 [11] Jin Z, Teoh A B J, Ong T S, Tee C. A revocable fingerprint template for security and privacy preserving. KSⅡ Transactions on Internet and Information Systems, 2010, 4(6):1327-1342 https://www.researchgate.net/publication/220595234_A_Revocable_Fingerprint_Template_for_Security_and_Privacy_Preserving [12] Lee C, Kim J. Cancelable fingerprint templates using minutiae-based bit-strings. Journal of Network and Computer Applications, 2010, 33(3):236-246 doi: 10.1016/j.jnca.2009.12.011 [13] Jin Z, Teoh A B J, Ong T S, Tee C. Fingerprint template protection with minutiae-based bit-string for security and privacy preserving. Expert Systems with Applications, 2012, 39(6):6157-6167 doi: 10.1016/j.eswa.2011.11.091 [14] Ahmad T, Hu J K, Wang S. String-based cancelable fingerprint templates. In:Proceedings of the 6th Conference on Industrial Electronics and Applications. Beijing, China:IEEE, 2011. 1028-1033 [15] Wong W J, Teoh A B J, Wong M L D, Kho Y H. Enhanced multi-line code for minutiae-based fingerprint template protection. Pattern Recognition Letters, 2013, 34(11):1221-1229 doi: 10.1016/j.patrec.2013.03.039 [16] Wang S, Hu J K. Alignment-free cancelable fingerprint template design:a densely infinite-to-one mapping (DITOM) approach. Pattern Recognition, 2012, 45(12):4129-4137 doi: 10.1016/j.patcog.2012.05.004 [17] Prasad M V N K, Santhosh K C. Fingerprint template protection using multiline neighboring relation. Expert Systems with Applications, 2014, 41(14):6114-6122 doi: 10.1016/j.eswa.2014.04.020 [18] 李梦醒, 冯全, 杨梅, 赵建, 贺康.基于二进制加密电路的无预对齐指纹匹配.北京邮电大学学报, 2014, 37(6):81-85 http://www.cnki.com.cn/Article/CJFDTOTAL-BJYD201406017.htmLi Meng-Xing, Feng Quan, Yang Mei, Zhao Jian, He Kang. Garbled circuits based alignment-free fingerprint matching. Journal of Beijing University of Posts and Telecommunications, 2014, 37(6):81-85 http://www.cnki.com.cn/Article/CJFDTOTAL-BJYD201406017.htm [19] Das P, Karthik K, Chandra G B. A robust alignment-free fingerprint hashing algorithm based on minimum distance graphs. Pattern Recognition, 2012, 45(9):3373-3388 doi: 10.1016/j.patcog.2012.02.022 [20] Tico M, Kuosmanen P. Fingerprint matching using an orientation-based minutia descriptor. IEEE Transactions on Pattern Analysis and Machine Intelligence, 2003, 25(8):1009-1014 doi: 10.1109/TPAMI.2003.1217604 [21] Ahmad T, Hu J K, Wang S. Pair-polar coordinate-based cancelable fingerprint templates. Pattern Recognition, 2011, 44(10-11):2555-2564 doi: 10.1016/j.patcog.2011.03.015 [22] Belguechi R, Cherrier E, Rosenberger C, Ait-Aoudia S. An integrated framework combining Bio-Hashed minutiae template and PKCS15 compliant card for a better secure management of fingerprint cancelable templates. Computers and Security, 2013, 39:325-339 doi: 10.1016/j.cose.2013.08.009 -




 下载:
下载: