Industrial Control System Devices Security Assessment with Multi-objective Decision
-
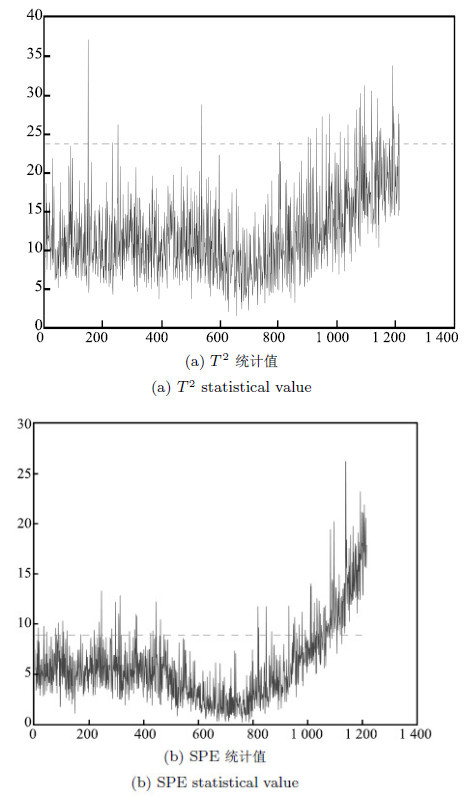
摘要: 目前的工业控制系统(Industrial control systems, ICS) 安全评估方法中,往往利用专家经验对系统设备受攻击的可能性进行赋值, 主观性较强.针对这个问题,本文提出了一种系统设备受攻击可能性的量化计算方法. 工控系统设备受攻击的可能性与两个因素有关,该设备受攻击后, 造成系统损害的严重程度与异常检测算法发现异常的时间长短.因此, 通过对工控系统中的各个设备发动相同攻击,记录各个设备受攻击后系统敏感指标的变化情况与异常检测算法发现异常的时间, 将敏感指标变化情况与发现异常时间作为量化指标,提出基于多目标决策的量化计算方法, 计算出各个设备受攻击的可能性.本文以田纳西--伊斯曼过程(Tennessee-Eastman process, TEP)为例,验证了计算方法的可行性,得到了设备受攻击可能性的量化计算结果.Abstract: In security assessment of industrial control systems, it is considered too subjective to evaluate the possibility of attack on industrial control systems (ICS) devices using expert experience. So a quantitative assessment is proposed for the possibility of attack on ICS devices. The weight of ICS devices depends on two factors, the severity of damage to the system and the time of anomaly detection after the devices being attacked. Thus, a record is made to keep both the variation of critical system parameters and the time when the anomaly is detected after the same attack against each device is launched in the industrial control system. This record is regarded as the quantitative parameter. Moreover, a quantitative method with multi-objective decision is proposed, meanwhile the possibility of each device's being attacked is then obtained. At last, the Tennessee-Eastman process (TEP) is set as an example to verify the feasibility of the method, and get the quantitative result of the possibility of attack on ICS devices.
-
Key words:
- Industrial control system /
- multi-objective /
- security assessment /
- quantitative method
-
表 1 量化评判表
Table 1 Quantitative evaluation table
设备 工艺指标1 工艺指标2 T2异常检测时间 SPE异常检测时间 x1 x11 x12 x13 x14 x2 x21 x22 x23 x24 ┇ ┇ ┇ ┇ ┇ xm xm1 xm2 xm3 xm4 表 2 过程操作限制
Table 2 Process operating constraints
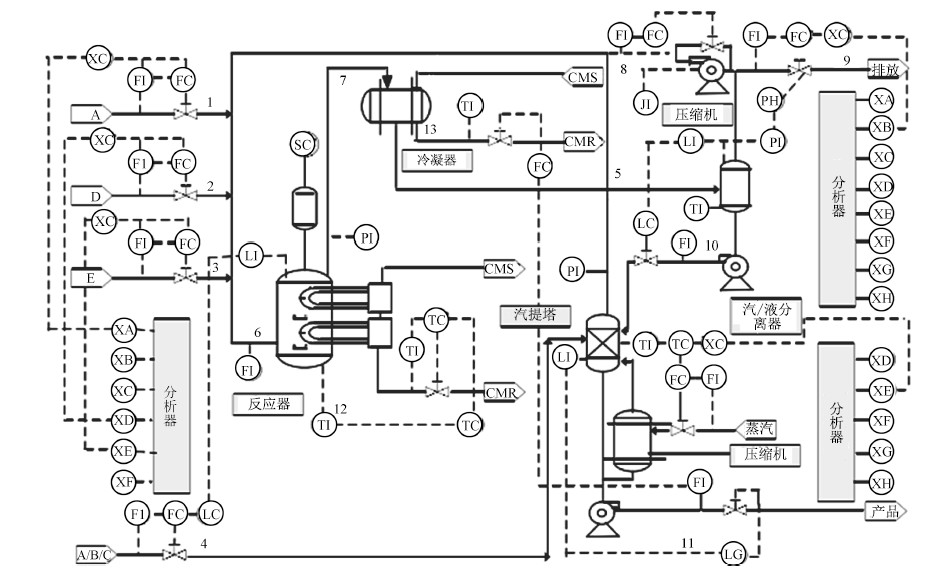
过程变量 正常操作限制 停机操作限制 下限 上限 下限 上限 反应炉压力(kPa) 无 2 895 无 3 000 反应炉液位(m3) 50% (11.8) 100% (21.3) 2.0 (24.0) 反应炉温度(℃) 无 150 无 175 分离器液位(m3) 30% (3.3) 100% (9.0) 11.8 12.0 汽提塔基准液位(m3) 30% (3.5) 100% (6.6) 1.0 8.0 表 3 实验结果
Table 3 Experiment results
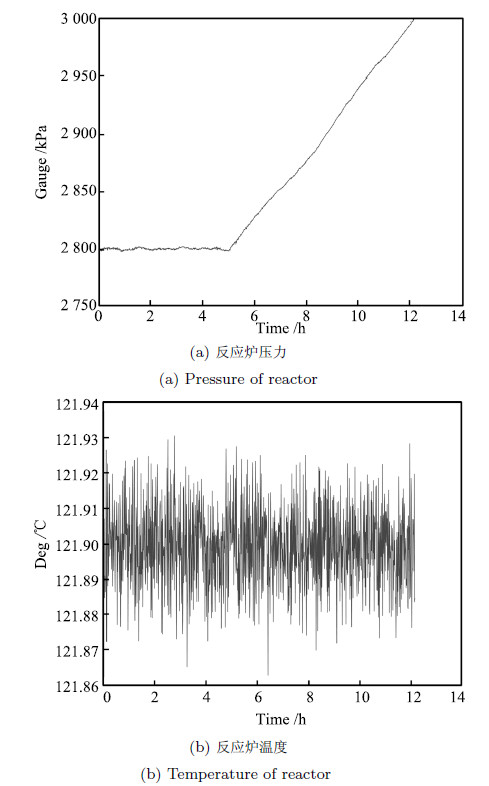
设备 反应炉 反应炉 检测时间 检测时间 压力(kPa) 温度(℃) T2异常 SPE异常 A1 3 000 122 1 400 1 400 A2 3 000 122 - 1 200 a3 3 000 122 - 1 000 a4 3 000 122 1 450 1 380 A5 3 050 140 720 760 a6 2 800 139 850 870 -
[1] Illiashenko O, Kharchenko V, Ahtyamov M. Security assessment and green issues of FPGA-based information and control systems. In: Proceedings of the 2013 International Conference on Digital Technologies (DT). Zilina, Slovakia: IEEE, 2013. 185-190 [2] Papakonstantinou N, Sierla S, Charitoudi K, O'Halloran B, Karhela T, Vyatkin V, Turner I. Security impact assessment of industrial automation systems using genetic algorithm and simulation. In: Proceedings of the 2014 IEEE Emerging Technology and Factory Automation (ETFA). Barcelona, Spain: IEEE, 2014. 1-8 [3] Lu Hui-Kang, Chen Dong-Qing, Peng Yong, Wang Hua-Zhong. Quantitative research on risk assessment for information security of industrial control system. Process Automation Instrumentation, 2014,35(10): 21-25 [4] Wang L J, Wang B, Peng Y J. Research the information security risk assessment technique based on Bayesian network. In: Proceedings of the 3rd International Conference on Advanced Computer Theory and Engineering (ICACTE). Chengdu, China: IEEE, 2010. V3-600-V3-604 [5] Bian N Y, Wang X Y, Mao L. Network security situational assessment model based on improved AHP_FCE. In: Proceedings of the 6th International Conference on Advanced Computational Intelligence (ICACI). Hangzhou, China: IEEE, 2013. 200-205 [6] 卢慧康, 陈冬青, 彭勇, 王华忠. 工业控制系统信息安全风险评估量化研究. 自动化仪表, 2014, 35(10): 21-25Lu Hui-Kang, Chen Dong-Qing, Peng Yong, Wang Hua-Zhong. Quantitative research on risk assessment for information security of industrial control system. Process Automation Instrumentation, 2014,35(10): 21-25 [7] Sasirekha V, Ilanzkumaran M. Heterogeneous wireless network selection using FAHP integrated with TOPSIS and VIKOR. In: Proceedings of the 2013 International Conference on Pattern Recognition, Informatics and Mobile Engineering (PRIME). Salem, India: IEEE, 2013. 399-407 [8] Mohyeddin M A, Gharaee H. FAHP-TOPSIS risks ranking models in ISMS. In: Proceedings of the 7th International Symposium on Telecommunications (IST). Tehran, Iran: IEEE, 2014. 879-882 [9] Cárdenas A A, Amin S, Lin Z S, Huang Y L, Huang C Y, Sastry S. Attacks against process control systems: risk, assessment, detection, and response. In: Proceedings of the 6th ACM Symposium on Information. Computer and Communication Security. New York, USA: ACM Press, 2011. 355 -366 [10] Nziga J P, Cannady J. Minimal dataset for network intrusion detection systems via MID-PCA: a hybrid approach. In: Proceedings of the 6th International Conference Intelligent Systems (IS). Sofia, Bulgaria: IEEE, 2012. 453-460 [11] Livani M A, Abadi M. A PCA-based distributed approach for intrusion detection in wireless sensor networks. In: Proceedings of the 2011 International Symposium on Computer Networks and Distributed Systems (CNDS). Tehran, Iran: IEEE, 2011. 55-60 [12] Downs J J, Vogel E F. A plant-wide industrial process control problem. Computers and Chemical Engineering, 1993,17(3): 245-255 [13] Lyman P R, Georgakis C. Plant-wide control of the Tennessee Eastman problem. Computers and Chemical Engineering, 1995,19(3): 321-331 [14] McAvoy T J. A methodology for screening level control structures in plantwide control systems. Computers and Chemical Engineering, 1998,22(11): 1543-1552 -




 下载:
下载: