Location Detection of False Data Injection Attacks in Cyber-Physical Power Systems Based on Sample Filtering-Label Powerset Extreme Trees Ensemble Boost
-
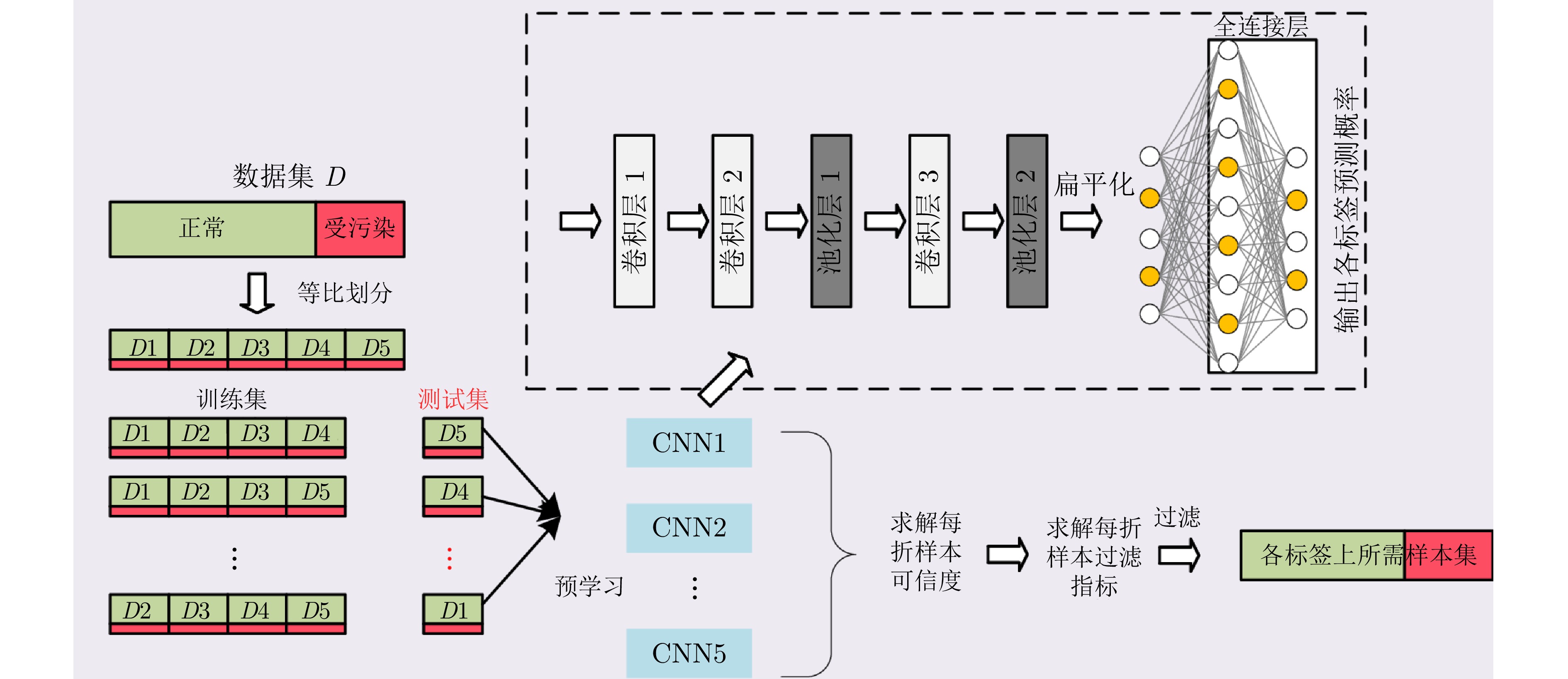
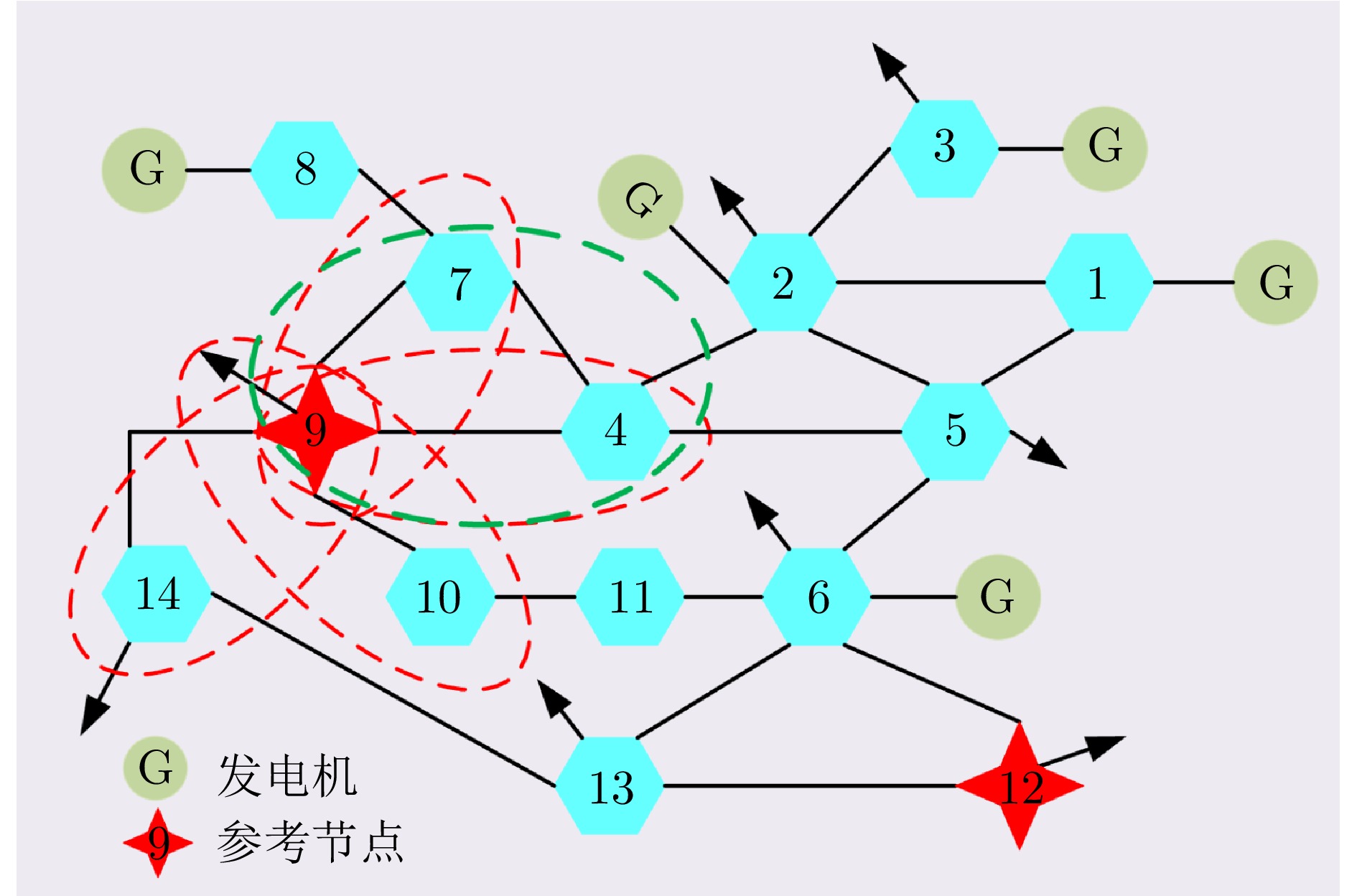
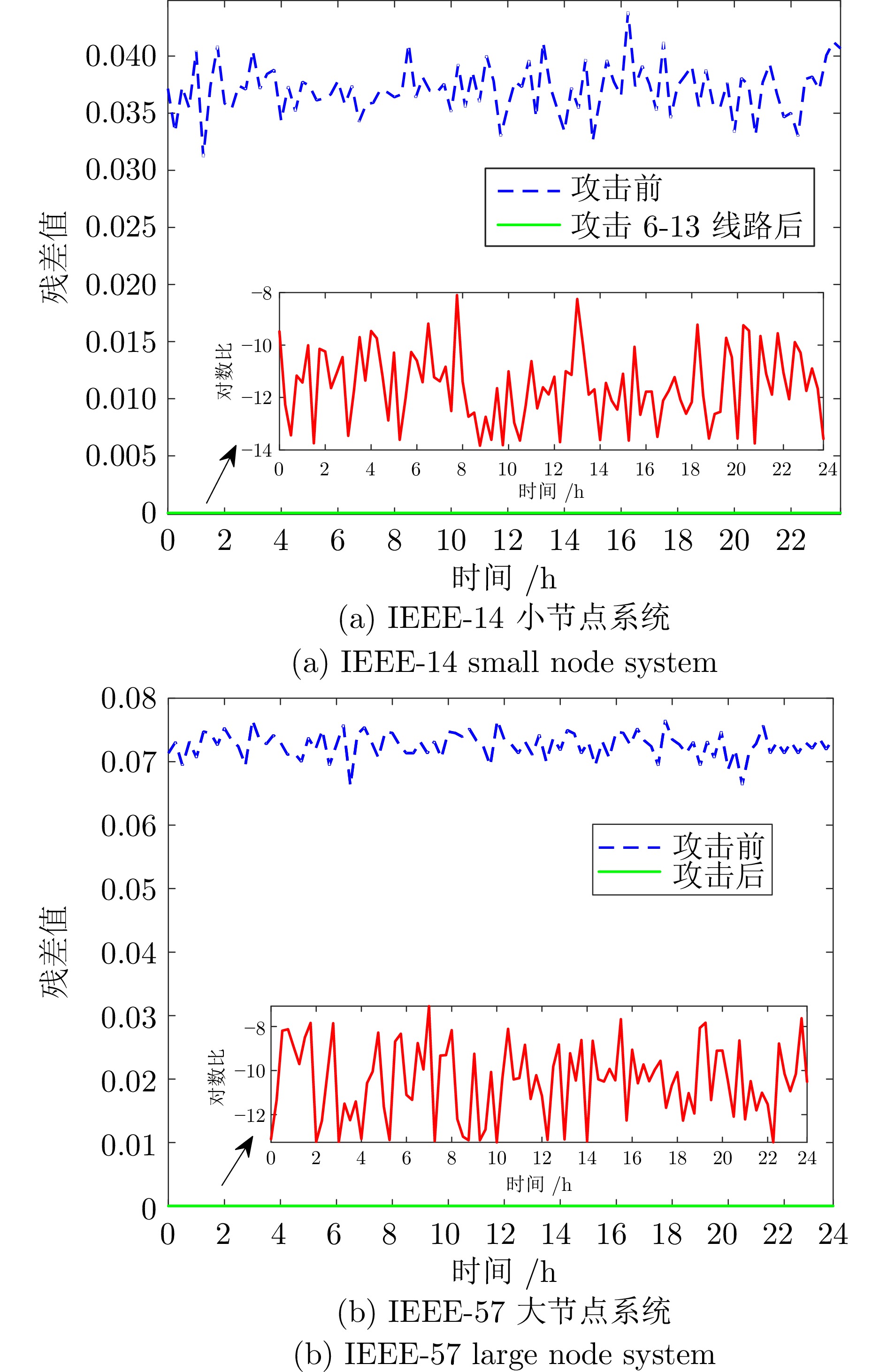
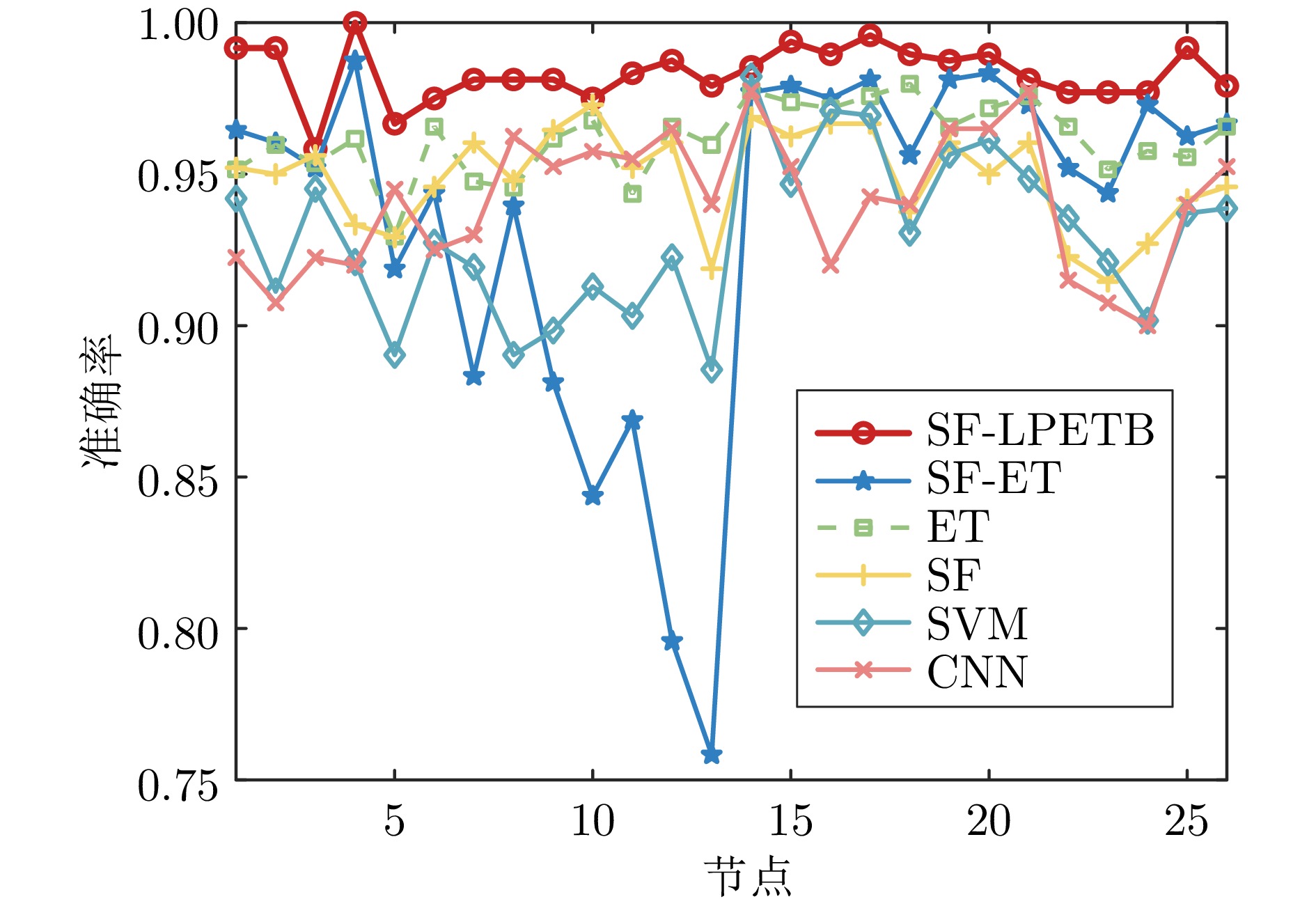
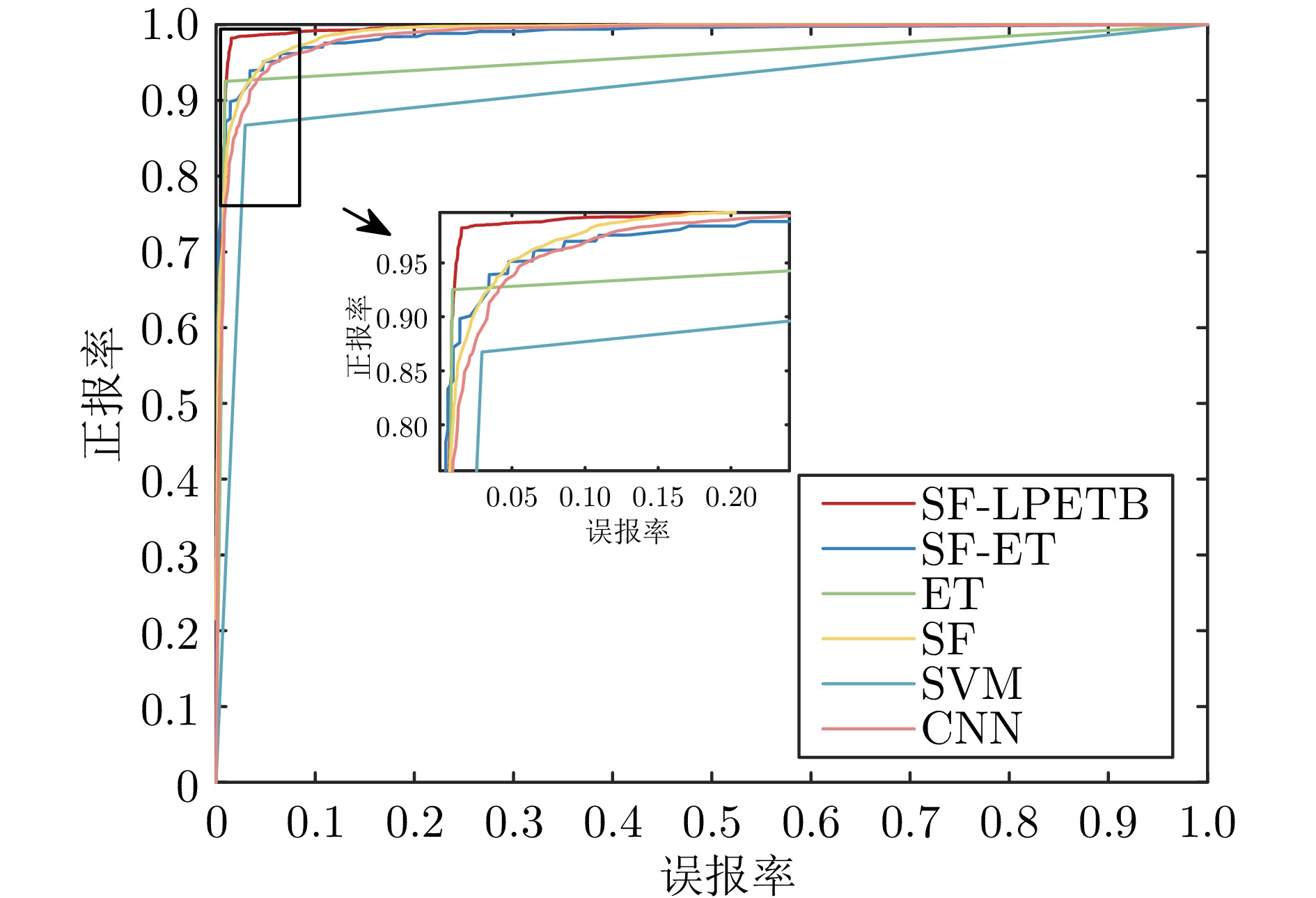
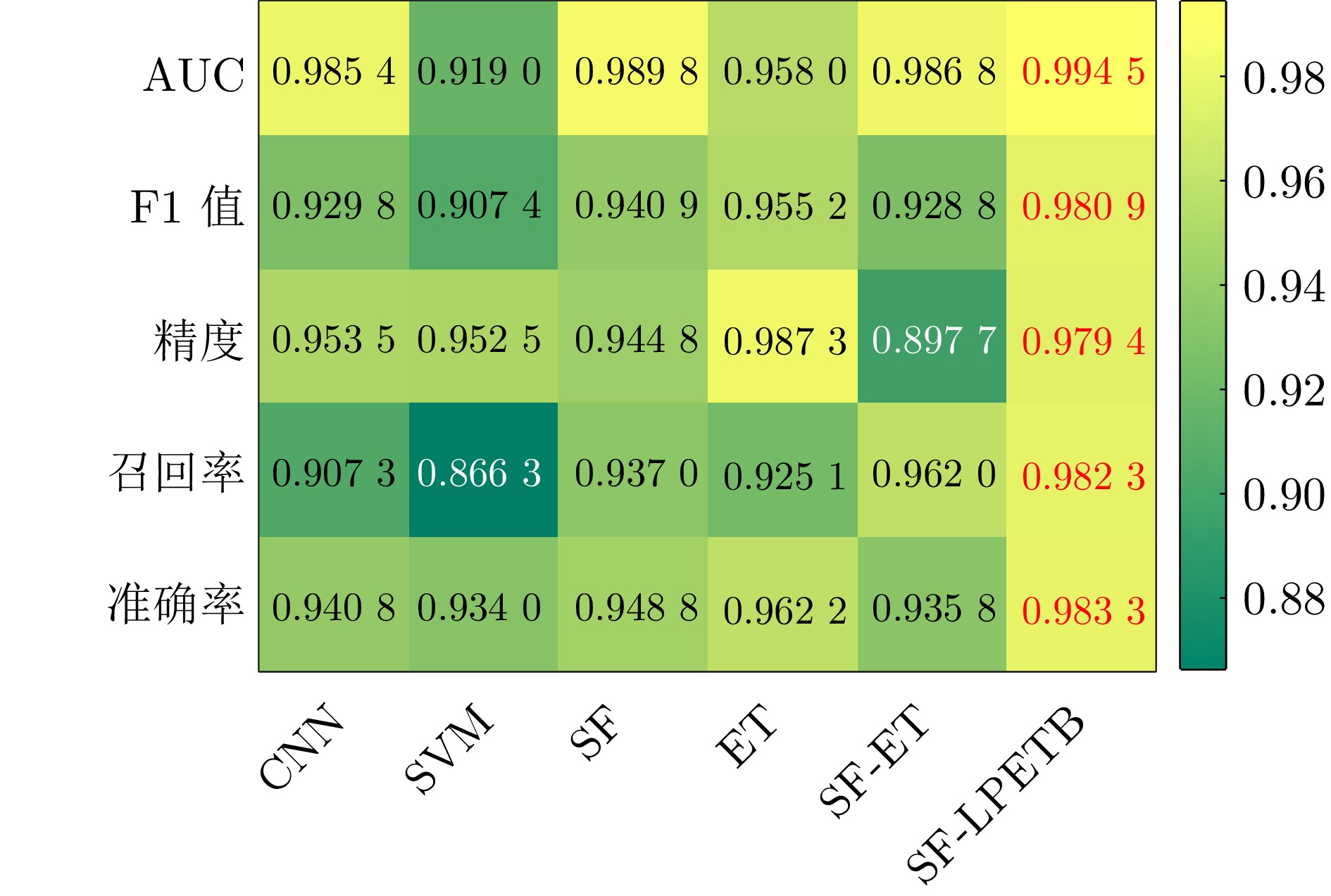
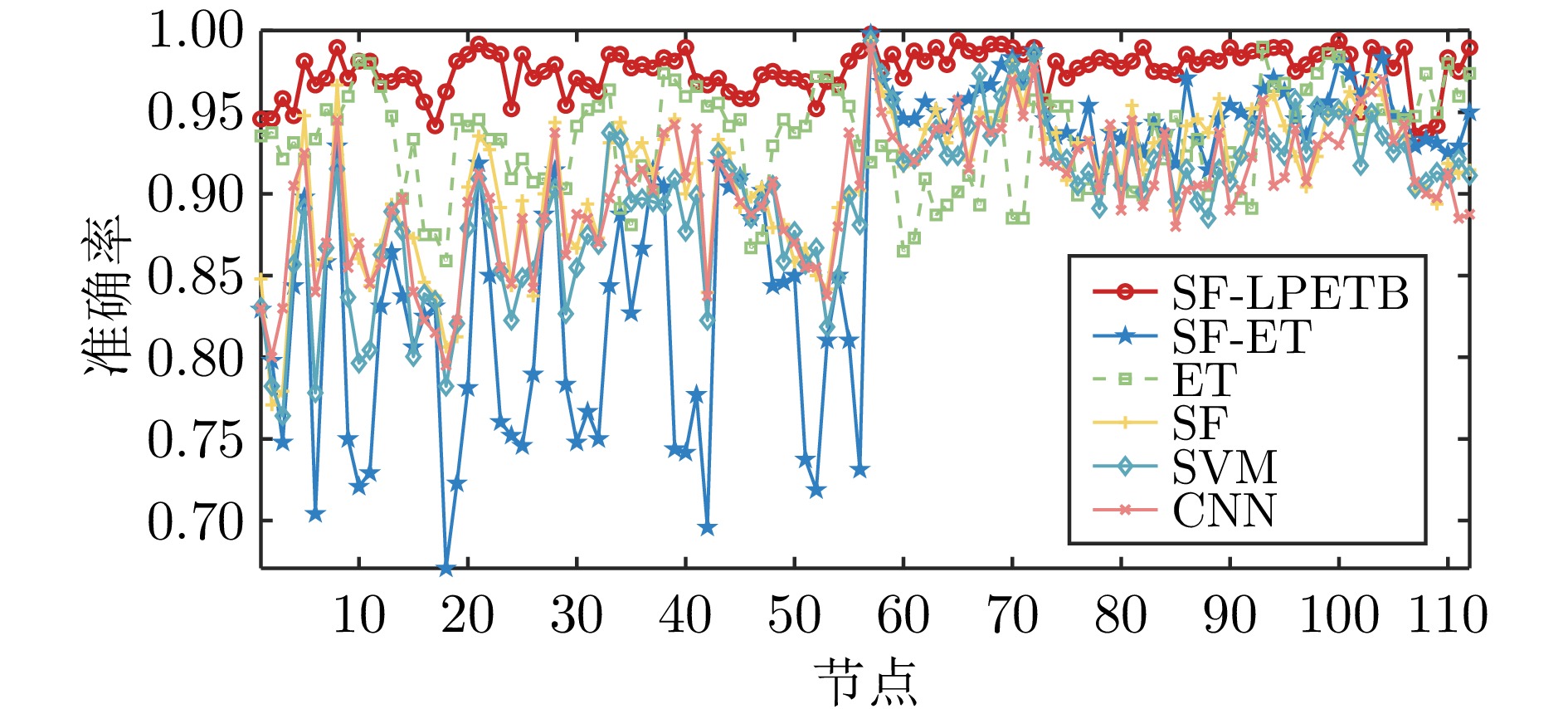
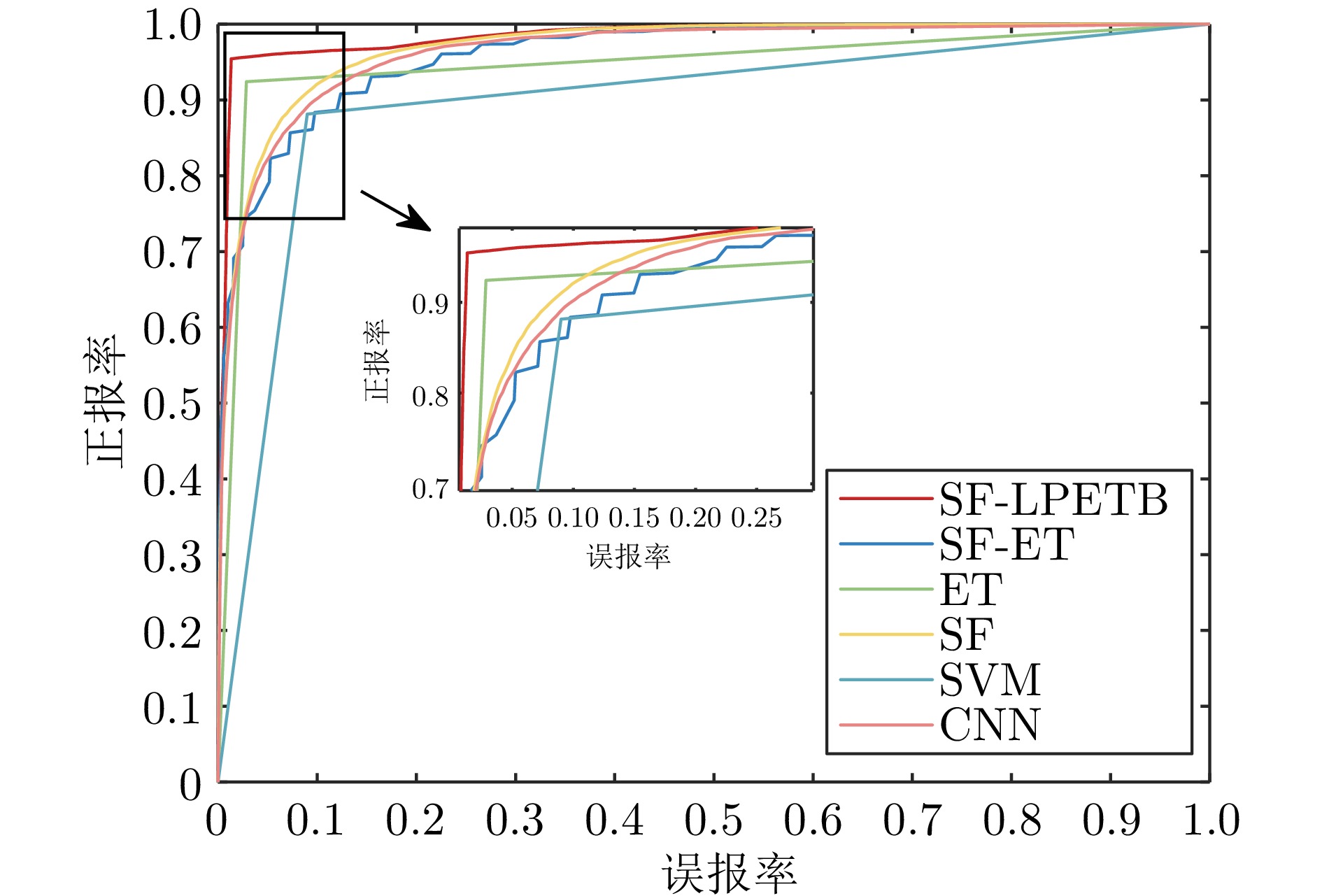
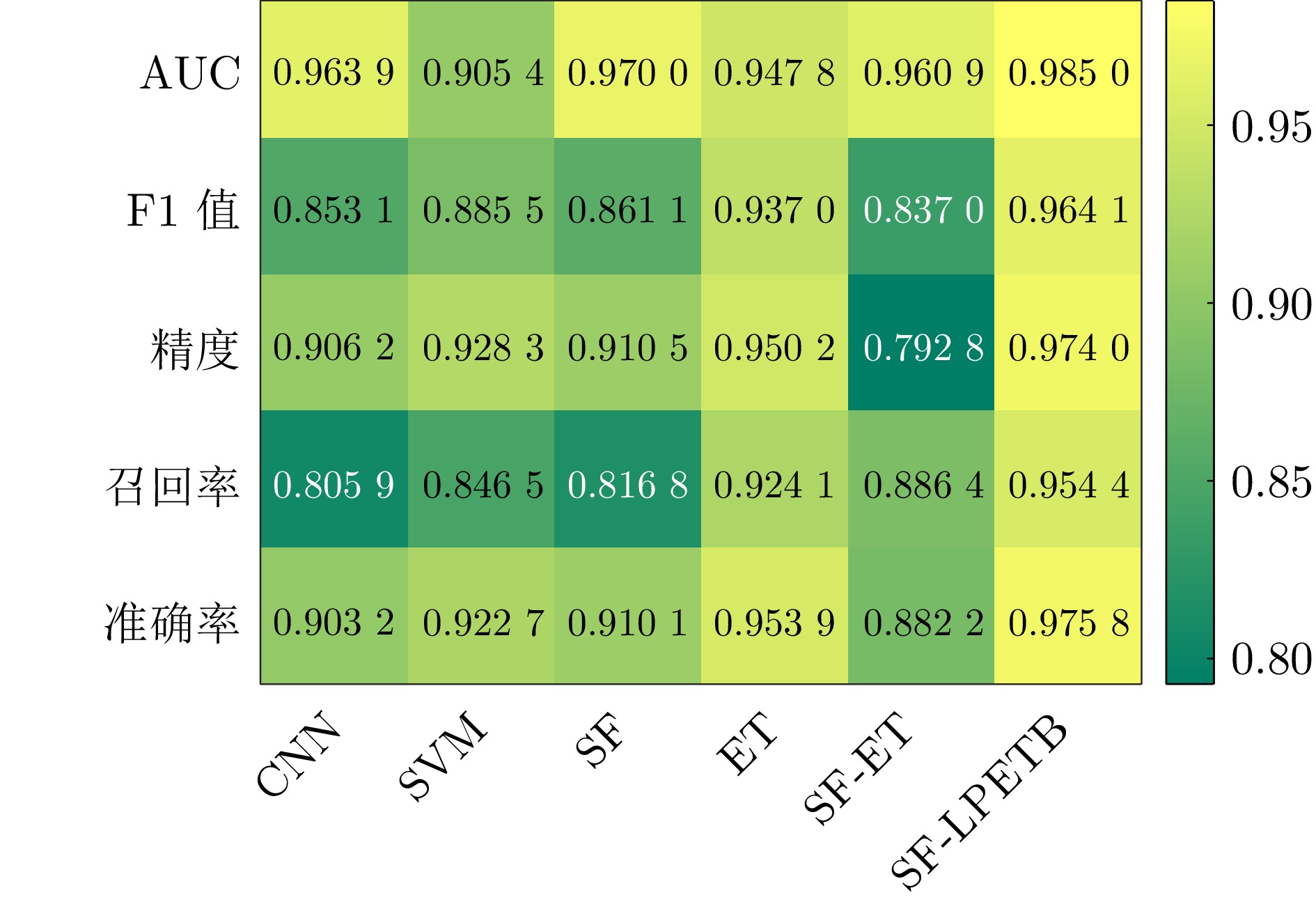
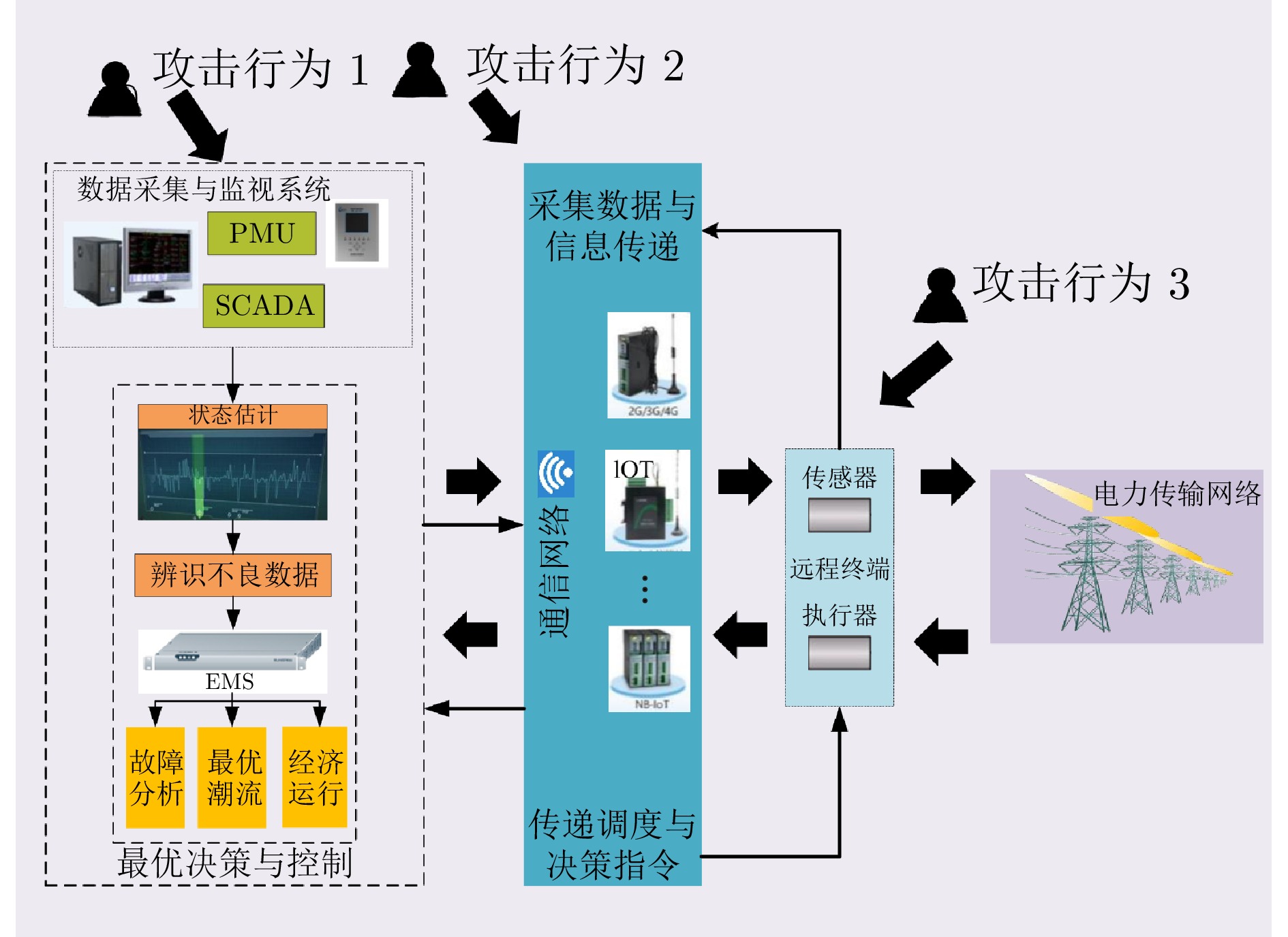
摘要: 虚假数据注入攻击行为严重威胁电力信息物理系统的安稳运行. 然而, 针对虚假数据注入攻击的现有检测未充分考虑海量量测数据的不平衡性和网络拓扑的关联性, 导致检测方法广泛存在定位性能差的问题, 因此提出一种基于样本过滤−标签聚合极端树集成的电力信息物理系统虚假数据注入攻击定位检测方法. 所提方法在基于深度学习的卷积神经网络中引入交叉验证思想, 用于过滤海量量测数据中代表性弱、重复率高的不平衡样本; 通过利用标签聚合将关联的网络拓扑融入极端树中, 并在与各节点状态对应的所有极端树上进行集成, 继而加权输出得到各节点状态的最终检测概率, 以实现对受攻击位置的精确定位. 在IEEE-14、IEEE-57节点系统上进行的仿真, 验证了所提方法的有效性, 且与多种已有定位检测方法进行充分对比, 验证了其在准确率、精度、召回率、F1值和AUC值上更优.Abstract: False data injection attacks seriously threaten the safe and stable operation of the cyber-physical power systems. However, the existing detection for false data injection attacks does not fully consider the imbalance of massive quantitative measurement data and the correlation of network topology, resulting in a wide range of detection methods that suffer from poor localization performance. In this paper, a sample filtering-label powerset extreme trees ensemble boost-based localization and detection method is proposed for false data injection attacks in cyber-physical power systems. The proposed method combines five-fold cross-validation with deep learning-based convolutional neural network for filtering unbalanced samples with weak representativeness and high repetition rate in massive quantitative measurement data; integrates the associated network topology into the extreme tree by utilizing label aggregation and integrates it over all the extreme trees corresponding to the states of each node, and then weights the outputs to obtain the final detection probability of each node's state, in order to achieve accurate localization of the attacked precise localization of the location. A large number of simulations on IEEE-14 and IEEE-57 node systems are conducted to verify the effectiveness of the proposed method, and a full comparison with multiple existing localization detection methods verifies its superiority in terms of accuracy, precision, recall, F1 value and AUC value.
-
表 1 量测单元信息部署表
Table 1 Deployment information of measurement units
节点系统设置 IEEE-14 IEEE-57 SCADA
配置节点编号1 ~ 14 1 ~ 57 PMU
配置节点编号4, 6 4, 10, 15, 20, 24, 29,
32, 37, 41, 48, 54SCADA量测量 节点有功/无功功率注入 节点有功/无功功率流 PMU量测量 节点电压幅值、相角 电流相量实部、虚部 表 2 标签编码对照表
Table 2 Tag code comparison table
编码规则 1 2 3 4 5 6 7 8 [9-4] [9-7] [0 0] [0 1] [1 0] [1 1] [9-10] [9-14] [9-4-7] [0 0 0] [0 0 1] [0 1 0] [0 1 1] [1 0 0] [1 0 1] [1 1 0] [1 1 1] -
[1] 龚立, 王先培, 田猛, 李晓旭, 朱紫阳. 电力信息物理系统韧性的概念与提升策略研究进展. 电力系统保护与控制, 2023, 51(14): 169−187Gong Li, Wang Xian-Pei, Tian Meng, Li Xiao-Xu, Zhu Zi-Yang. Concepts and research progress on enhancement strategies for cyber physical power system resilience. Power System Protection and Control, 2023, 51(14): 169−187 [2] 汤奕, 李梦雅, 王琦, 倪明. 电力信息物理系统网络攻击与防御研究综述(二)检测与保护. 电力系统自动化, 2019, 43(10): 1−9Tang Yi, Li Meng-Ya, Wang Qi, Ni Ming. A review on research of cyber-attacks and defense in cyber physical power systems part two detection and protection. Automation of Electric Power Systems, 2019, 43(10): 1−9 [3] Chen B Y, Li H B, Zhou B. Real-time identification of false data injection attacks: A novel dynamic-static parallel state estimation based mechanism. IEEE Access, 2019, 7: 95812−95824 doi: 10.1109/ACCESS.2019.2929785 [4] 刘增稷, 王琦, 薛彤, 汤奕. 电力系统中数据驱动算法安全威胁分析及应对方法研究. 中国电机工程学报, 2023, 43(12): 4538−4553Liu Zeng-Ji, Wang Qi, Xue Tong, Tang Yi. Research on security risks and defense methods of data-driven algorithms in power systems. Proceedings of the CSEE, 2023, 43(12): 4538−4553 [5] 李卓, 谢耀滨, 吴茜琼, 张有为. 基于深度学习的电力系统虚假数据注入攻击检测综述. 电力系统保护与控制, 2024, 52(19): 175−187Li Zhuo, Xie Yao-Bin, Wu Qian-Qiong, Zhang You-Wei. Review of deep learning-based false data injection attack detection in power systems. Power System Protection and Control, 2024, 52(19): 175−187 [6] 席磊, 董璐, 程琛, 田习龙, 李宗泽. 基于混合黑猩猩优化极限学习机的电力信息物理系统虚假数据注入攻击定位检测. 电力系统保护与控制, 2024, 52(14): 46−58Xi Lei, Dong Lu, Cheng Chen, Tian Xi-Long, Li Zong-Ze. Location detection of a false data injection attack in a cyber-physical power system based on a hybrid chimp optimized extreme learning machine. Power System Protection and Control, 2024, 52(14): 46−58 [7] 席磊, 王艺晓, 何苗, 程琛, 田习龙. 基于反向鲸鱼−多隐层极限学习机的电网FDIA检测. 中国电力, 2024, 57(9): 20−31Xi Lei, Wang Yi-Xiao, He Miao, Cheng Chen, Tian Xi-Long. FDIA detection in power grid based on opposition-based whale optimization algorithm and multi-layer extreme learning machine. Electric Power, 2024, 57(9): 20−31 [8] 席磊, 何苗, 周博奇, 李彦营. 基于改进多隐层极限学习机的电网虚假数据注入攻击检测. 自动化学报, 2023, 49(4): 881−890Xi Lei, He Miao, Zhou Bo-Qi, Li Yan-Ying. Research on false data injection attack detection in power system based on improved multi layer extreme learning machine. Acta Automatica Sinica, 2023, 49(4): 881−890 [9] 陶磊, 罗萍萍, 林济铿. 基于深度学习的直流微电网虚假数据注入攻击二阶段检测方法. 中国电力, 2024, 57(9): 11−19Tao Lei, Luo Ping-Ping, Lin Ji-Keng. Two-stage detection method for DC microgrid false data injection attack based on deep learning. Electric Power, 2024, 57(9): 11−19 [10] 席磊, 程琛, 田习龙. 基于改进卷积神经网络的电网虚假数据注入攻击定位方法. 南方电网技术, 2025, 19(1): 74−84Xi Lei, Cheng Chen, Tian Xi-Long. Improved convolutional neural network-based localization method for false data injection attacks on power grids. Southern Power System Technology, 2025, 19(1): 74−84 [11] 陈柏任, 夏候凯顺, 李梦诗. 基于数据驱动的电力系统虚假数据注入攻击防御框架的研究. 电测与仪表, 2024, 61(12): 10−16Chen Bai-Ren, Xiahou Kai-Shun, Li Meng-Shi. Research on defense framework for false data injection attacks in power system based on data-driven algorithm. Electrical Measurement & Instrumentation, 2024, 61(12): 10−16 [12] 苏向敬, 邓超, 栗风永, 符杨, 萧士渠. 基于MGAT-TCN模型的可解释电网虚假数据注入攻击检测方法. 电力系统自动化, 2024, 48(2): 118−127Su Xiang-Jing, Deng Chao, Li Feng-Yong, Fu Yang, Xiao Shi-Qu. Interpretable detection method for false data injection attack on power grid based on multi-head graph attention network and time convolution network model. Automation of Electric Power Systems, 2024, 48(2): 118−127 [13] Xue W L, Wu T. Active learning-based XGBoost for cyber physical system against generic AC false data injection attacks. IEEE Access, 2020, 8: 144575−144584 doi: 10.1109/ACCESS.2020.3014644 [14] 席磊, 田习龙, 余涛, 程琛. 基于相关特征−多标签级联提升森林的电网虚假数据注入攻击定位检测. 南方电网技术, 2024, 18(5): 39−50Xi Lei, Tian Xi-Long, Yu Tao, Cheng Chen. Locational detection of false data injection attack in power grid based on relevant features multi-label cascade boosting forest. Southern Power System Technology, 2024, 18(5): 39−50 [15] 席磊, 王文卓, 白芳岩, 陈洪军, 彭典名, 李宗泽. 基于最大信息系数−双层置信极端梯度提升树的电网虚假数据注入攻击定位检测. 电网技术, 2025, 49(2): 824−833Xi Lei, Wang Wen-Zhuo, Bai Fang-Yan, Chen Hong-Jun, Peng Dian-Ming, Li Zong-Ze. Grid false data injection attack localization detection based on MIC-double-deck confidence XGBoost tree. Power System Technology, 2025, 49(2): 824−833 [16] 王琦, 邰伟, 汤奕, 倪明. 面向电力信息物理系统的虚假数据注入攻击研究综述. 自动化学报, 2019, 45(1): 72−83Wang Qi, Tai Wei, Tang Yi, Ni Ming. A review on false data injection attack toward cyber physical power system. Acta Automatica Sinica, 2019, 45(1): 72−83 [17] Wu T, Xue W L, Wang H Z, Chung C Y, Wang G B, Peng J C, et al. Extreme learning machine-based state reconstruction for automatic attack filtering in cyber physical power system. IEEE Transactions on Industrial Informatics, 2021, 17(3): 1892−1904 doi: 10.1109/TII.2020.2984315 [18] 王彩强, 张青, 李晨, 黄志勇, 梁财源, 何思名. 含有限PMU的配电网故障区域在线辨识算法. 南方电网技术, 2024, 18(12): 42−50Wang Cai-Qiang, Zhang Qing, Li Chen, Huang Zhi-Yong, Liang Cai-Yuan, He Si-Ming. Fault section on-line identification algorithm with limited PMU for distribution network. Southern Power System Technology, 2024, 18(12): 42−50 [19] Wang H Z, Wen X C, Xu Y L, Zhou B, Peng J C, Liu W X. Operating state reconstruction in cyber physical smart grid for automatic attack filtering. IEEE Transactions on Industrial Informatics, 2022, 18(5): 2909−2922 doi: 10.1109/TII.2020.3000172 [20] Yadav S, Shukla S. Analysis of k-fold cross-validation over hold-out validation on colossal datasets for quality classification. In: Proceedings of the IEEE 6th International Conference on Advanced Computing (IACC). Bhimavaram, India: IEEE, 2016. 78−83 [21] 申超波, 王志海, 孙艳歌. 基于标签聚类的多标签分类算法. 软件, 2014, 35(8): 16−21Shen Chao-Bo, Wang Zhi-Hai, Sun Yan-Ge. A multi-label classification algorithm based on label clustering. Software, 2014, 35(8): 16−21 [22] 罗小元, 何俊楠, 王新宇, 李宏波, 关新平. 智能电网虚假数据注入攻击弹性防御策略的拓扑优化. 自动化学报, 2023, 49(6): 1326−1338Luo Xiao-Yuan, He Jun-Nan, Wang Xin-Yu, Li Hong-Bo, Guan Xin-Ping. Research on topology optimization of resilient defense strategy against false data injection attack in smart grid. Acta Automatica Sinica, 2023, 49(6): 1326−1338 [23] 徐先峰, 李芷菡, 刘状壮, 王轲, 马志雄, 姚景杰, 等. 基于半监督学习标签传播−极端随机树算法的光伏阵列故障诊断及定位. 电网技术, 2023, 47(3): 1038−1046Xu Xian-Feng, Li Zhi-Han, Liu Zhuang-Zhuang, Wang Ke, Ma Zhi-Xiong, Yao Jing-Jie, et al. Fault diagnosis and localization of photovoltaic arrays based on semi-supervised learning label propagation-extra tree algorithm. Power System Technology, 2023, 47(3): 1038−1046 [24] 李刚, 李天琦, 程晓荣, 王红玉. 大数据可信性度量方法. 计算机工程与设计, 2017, 38(3): 652−658Li Gang, Li Tian-Qi, Cheng Xiao-Rong, Wang Hong-Yu. Credibility measurement method of big data. Computer Engineering and Design, 2017, 38(3): 652−658 [25] 林峰, 梅勇, 朱益华, 常东旭, 刘韧, 郭恒道. 网络攻击对电力系统典型场景全过程影响综述. 南方电网技术, 2023, 17(11): 61−75Lin Feng, Mei Yong, Zhu Yi-Hua, Chang Dong-Xu, Liu Ren, Guo Heng-Dao. Overview of the entire process influence of cyber attack on typical scenarios of power systems. Southern Power System Technology, 2023, 17(11): 61−75 [26] Qu Z W, Yang J C, Wang Y J, Georgievitch P M. Detection of false data injection attack in power system based on Hellinger distance. IEEE Transactions on Industrial Informatics, 2024, 20(2): 2119−2128 doi: 10.1109/TII.2023.3286895 -




 下载:
下载: