A Preferential Growing Evolution-model of Terrorist Networks Based on Multi-local Network
-
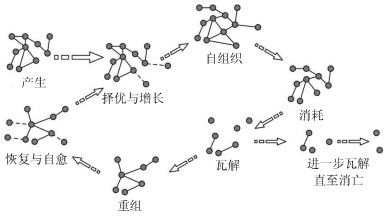
摘要: 恐怖组织网络是一种特殊的复杂网络,其时空演化规律反映出恐怖组织活动的特征.为更准确地理解恐怖组织网络的动态演化规律,提出一种基于多局域的恐怖组织网络择优增长演化模型,并对此模型进行了仿真与模拟.该模型能准确地描述在局部信息条件下,新节点的择优和网络的增长过程及其规律;并且利用网络信息中心度来衡量恐怖组织网络节点的信念水平,动态地刻画了恐怖组织网络的增长过程.实验结果表明:恐怖组织网络的局域度分布仍服从幂律分布,网络信息中心度具有集中与分散性的特征;最后,对多个恐怖组织网络按该模型进行仿真演化,验证了该模型的准确性与科学性.Abstract: The network of terrorist organizations is a special complex network, and its spatiotemporal evolution process reflects the characteristics of terrorist organization activities. To more accurately depict the dynamic evolution process of terrorist network, this paper puts forward a preferential-growing evolution model of terrorist networks based on the multi-local network, and the model is simulated. The model can accurately describe the growth of new nodes and the growth process of network under the condition of local information. We use the node network information center degree to measure the level of terrorist beliefs, dynamic characterization of a terrorist network growth process. The experimental results show:in the terrorist networks, the degree distribution of local network follows the power-law distribution, the network information center degree of the nodes of local network has the characteristics of centralized and decentralized. Finally, the model is verified with the data of terrorist networks. The verification results show that the model is accurate.
-
Key words:
- Terrorist networks /
- preferential-growth /
- multi-local network /
- information center degree /
- power law distribution
1) 本文责任编委 赵铁军 -
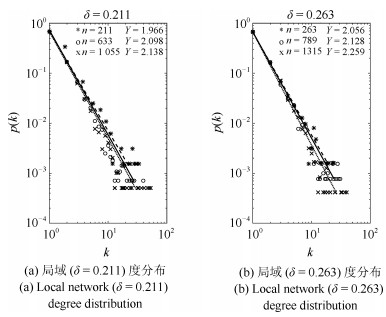
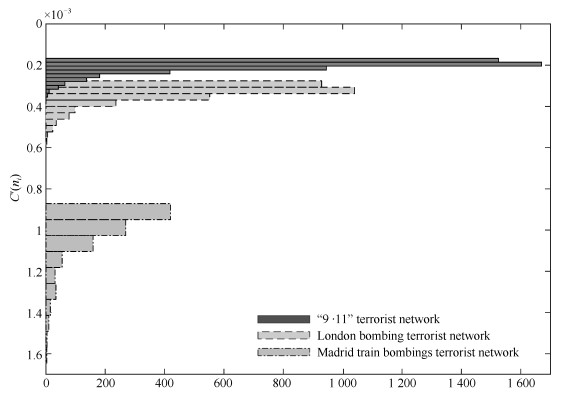
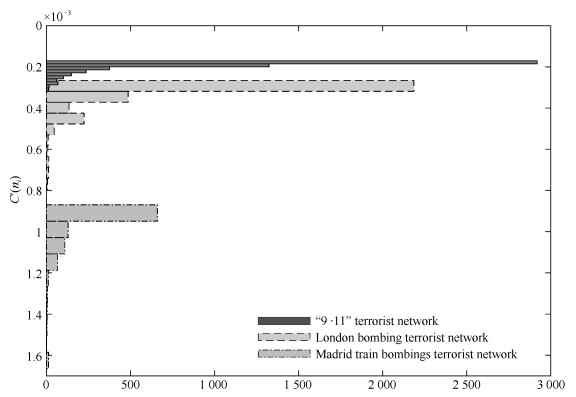
表 1 "9$\cdot$11"恐怖组织网络局域划分
Table 1 The di"ision on local network of "9$\cdot$11" Terrorist Network
$L_j (t)$ $\delta$ 5 0.263 4 0.211 5 0.263 5 0.263 表 2 伦敦爆炸案恐怖组织网络局域划分
Table 2 The division on local network of London bombing terrorist network
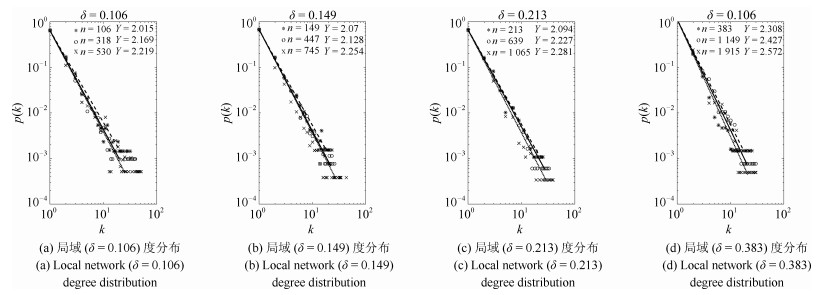
$L_j (t)$ $\delta$ 5 0.106 7 0.149 7 0.149 10 0.213 18 0.383 表 3 马德里火车站爆炸案恐怖组织网络局域划分
Table 3 The division on local network of Madrid train bombings terrorist network
$L_j (t)$ $\delta$ 4 0.06 4 0.06 6 0.09 10 0.149 11 0.164 13 0.193 19 0.284 -
[1] 程聪慧, 郭俊华.网络恐怖主义的挑战及其防范.情报杂志, 2015, 34(3):10-15, 20 doi: 10.3969/j.issn.1002-1965.2015.03.003Cheng Cong-Hui, Guo Jun-Hua. Challenges and prevention of cyberterrorism. Journal of Intelligence, 2015, 34(3):10-15, 20 doi: 10.3969/j.issn.1002-1965.2015.03.003 [2] Stripling M. Embodying terror networks: How directioncreates structure[Online], available: http://www.crisisville.com/files/Terrorism-DirectedNetworks.pdf, January 8, 2013. [3] Moon I C, Carley K M. Modeling and simulating terrorist networks in social and geospatial dimensions. IEEE Intelligent Systems, 2007, 22(5):40-49 doi: 10.1109/MIS.2007.4338493 [4] Krebs V E. Mapping networks of terrorist cells. Connections, 2002, 24(3):43-52 [5] Krebs V E. Uncloaking terrorist networks. First Monday, 2002, 7(4):1-4 http://www.wanfangdata.com.cn/details/detail.do?_type=perio&id=Open J-Gate000002557116 [6] Memon N, Hicks D L, Harkiolakis N, Rajput A Q K. Retracted: Small world terrorist networks: a preliminary investigation. Applications and Innovations in Intelligent Systems XV. London: Springer, 2008. 339-344 [7] Memon N, Larsen H L, Hicks D L, Harkiolakis N. Retracted: detecting hidden hierarchy in terrorist networks: some case studies. In: Proceedings of the 2008 International Conference on Intelligence and Security Informatics. Taipei, China: Springer-Verlag, 2008. 477-489 [8] Memon N, Larsen H L. Practical Approaches for analysis, visualization and destabilizing terrorist networks. In: Proceedings of the First International Conference on Availability, Reliability and Security. Vienna, Austria: IEEE, 2006. 435-448 [9] Will U K, Memon N, Karampelas P. Detecting new trends in terrorist networks. In: Proceedings of the 2010 International Conference on Social Networks Analysis and Mining. Odense, Denmark: IEEE, 2010. 435-440 [10] Enders W, Su X J. Rational terrorists and optimal network structure. Journal of Conflict Resolution, 2007, 52(1):33-57 http://www.wanfangdata.com.cn/details/detail.do?_type=perio&id=10.1177/0022002706296155 [11] Carly K M. Dynamic network analysis for counter-terrorism[Online], available: https://www.researchgate.net/publication/228770516_Dynamic_network_analysis_for_counter-terrorism, January 7, 2017. [12] Carly K M. Destabilization of covert networks. Computational and Mathematical Organization Theory, 2006, 12(1):51-56 doi: 10.1007/s10588-006-7083-y [13] 毕震坤, 张伟, 余浩淼, 陈云芳.恐怖网络中基于节点割集分层的组织结构发现方法.南京邮电大学学报(自然科学版), 2014, 34(5):111-118 doi: 10.3969/j.issn.1673-5439.2014.05.018Bi Zhen-Kun, Zhang Wei, Yu Hao-Miao, Chen Yun-Fang. Organizational structure discovery in terrorist networks based on cut Set and hierarchical method. Journal of Nanjing University of Posts and Telecommunications (Nature Science), 2014, 34(5):111-118 doi: 10.3969/j.issn.1673-5439.2014.05.018 [14] 张海, 孙多勇.基于社会网络理论的恐怖组织隐蔽网络分析方法.安全与环境学报, 2011, 11(3):259-264 doi: 10.3969/j.issn.1009-6094.2011.03.063Zhang Hai, Sun Duo-Yong. Study on the terrorist covert networks from the perspective of social network analysis. Journal of Safety and Environment, 2011, 11(3):259-264 doi: 10.3969/j.issn.1009-6094.2011.03.063 [15] 李本先, 凌云翔, 方锦清, 梅建明.恐怖组织如何编制网络.复杂系统与复杂性科学, 2016, 13(1):68-73 http://d.old.wanfangdata.com.cn/Periodical/fzxtyfzxkx201601006Li Ben-Xian, Ling Yun-Xiang, Fang Jin-Qing, Mei Jian-Ming. How to map the network of terrorism group. Complex Systems and Complexity Science, 2016, 13(1):68-73 http://d.old.wanfangdata.com.cn/Periodical/fzxtyfzxkx201601006 [16] 李本先, 李孟军, 方锦清, 仰琎歆.恐怖组织网络的时空演化规律.自动化学报, 2013, 39(6):772-779 http://www.aas.net.cn/CN/abstract/abstract18102.shtmlLi Ben-Xian, Li Meng-Jun, Fang Jin-Qing, Yang Jin-Xin. Empirical study on spatiotemporal evolution of terrorism organization network. Acta Automatica Sinica, 2013, 39(6):772-779 http://www.aas.net.cn/CN/abstract/abstract18102.shtml [17] 李本先, 江成俊, 方锦清.网络科学在反恐研究中面临的挑战和机遇.复杂系统与复杂性科学, 2014, 11(1):60-66 http://d.old.wanfangdata.com.cn/Periodical/fzxtyfzxkx201401008Li Ben-Xian, Jiang Cheng-Jun, Fang Jin-Qing. Network science's challenges and opportunities in counter-terrorism research. Complex Systems and Complexity Science, 2014, 11(1):60-66 http://d.old.wanfangdata.com.cn/Periodical/fzxtyfzxkx201401008 [18] 李本先, 方锦清, 江成俊, 梅建明, 迟妍.恐怖组织网络的心理学与动力学分析:从个体到群体.复杂系统与复杂性科学, 2014, 11(2):87-94 http://d.old.wanfangdata.com.cn/Periodical/fzxtyfzxkx201402011Li Ben-Xian, Fang Jin-Qing, Jiang Cheng-Jun, Mei Jian-Ming, Chi Yan. Psychology and dynamical analysis of terrorism organization:from individual to group. Complex Systems and Complexity Science, 2014, 11(2):87-94 http://d.old.wanfangdata.com.cn/Periodical/fzxtyfzxkx201402011 [19] 许晴, 祖正虎, 郑涛.恐怖组织网络的实证研究.合肥工业大学学报(自然科学版), 2010, 33(2):242-244, 292 doi: 10.3969/j.issn.1003-5060.2010.02.020Xu Qing, Zu Zheng-Hu, Zheng Tao. Empirical study of terrorist organizations network. Journal of Hefei University of Technology (Natural Science), 2010, 33(2):242-244, 292 doi: 10.3969/j.issn.1003-5060.2010.02.020 [20] 孙多勇, 李文举, 付举磊, 李博.基于Agent建模的恐怖袭击影响因素仿真分析.安全与环境学报, 2013, 13(5):259-264 http://d.old.wanfangdata.com.cn/Periodical/aqyhjxb201305055Sun Duo-Yong, Li Wen-Ju, Fu Ju-Lei, Li Bo. On the factors leading to terror attacks based on the agent simulation analysis approach. Journal of Safety and Environment, 2013, 13(5):259-264 http://d.old.wanfangdata.com.cn/Periodical/aqyhjxb201305055 [21] Lange S, Donges J F, Volkholz J, Kurths J. Local difference measures between complex networks for dynamical system model evaluation. PLoS One, 2015, 10(4):Article No. e0129413 http://www.wanfangdata.com.cn/details/detail.do?_type=perio&id=Doaj000004522087 [22] Li B, Sun D Y, Zhu R Q, Li Z. Agent based modeling on organizational dynamics of terrorist network. Discrete Dynamics in Nature and Society, 2015, 2015: Article No. 237809 [23] Gaharwar R D, Shah D B. Application of centrality principles for terrorist network role analysis. International Journal of Scientific Research in Science and Technology, 2018, 4(2):1216-1221 [24] Barabási A L, Albert R. Emergence of scaling in random networks. Science, 1999, 286(5439):509-512 doi: 10.1126/science.286.5439.509 [25] Barabasi A L. Linked:The New Science of Networks. Cambridge, MA:Perseus, 2002. [26] Michalak T P, Rahwan T, Skibski O, Wooldridge M. Defeating terrorist networks with game theory. IEEE Intelligent Systems, 2015, 30(1):53-61 doi: 10.1109/MIS.2015.11 [27] Husslage B, Borm P, Burg T, Hamers H, Lindelauf R. Ranking terrorists in networks:a sensitivity analysis of Al Qaedaś 9/11 attack. Social Networks, 2015, 42:1-7 doi: 10.1016/j.socnet.2015.02.003 [28] Aitkin M, Vu D, Francis B. Statistical modelling of a terrorist network. Journal of the Royal Statistical Society, 2017, 180(3):751-768 doi: 10.1111/rssa.12233 [29] Penzar D, Srbljinovic A. About modeling of complex networks with applications to terrorist group modeling. Interdisciplinary Description of Complex Systems, 2005, 3(1):27-43 [30] Li X, Chen G R. A local-world evolving network model. Physica A:Statistical Mechanics and its Applications, 2003, 328(1-2):274-286 doi: 10.1016/S0378-4371(03)00604-6 [31] Qin S, Dai G Z. A new local-world evolving network model. Chinese Physics B, 2009, 18(2):383-390 doi: 10.1088/1674-1056/18/2/001 [32] Arquilla J, Ronfeldt D F. Networks and Netwars:the Future of Terror, Crime, and Militancy. California:Santa Monica, 2001. 20-24 [33] Bohannon J. Counter terrorism's new tool:"metanetwork" analysis. Science, 2009, 325(5939):409-411 doi: 10.1126/science.325_409 [34] Wasserman S, Faust K. Social Network Analysis:Methods and Applications. London:Cambridge University Press, 1994. 125-245 [35] Stephenson K, Zelen M. Rethinking centrality:methods and examples. Social Networks, 1989, 11(1):1-37 doi: 10.1016/0378-8733(89)90016-6 [36] Morris M. Networks and Diffusion: An Application of Loglinear Models to the Population Dynamics of Disease. Chicago: Dissertation Department of Sociology, 1989. 110-126 [37] Gill P, Corner E, Conway M, Thornton A, Bloom M, Horgan J. Terrorist use of the internet by the numbers. Criminology & Public Policy, 2017, 16(1):99-117 doi: 10.1111/1745-9133.12249 [38] Gaharwar R D, Shah D B, Gaharwar G K S. Terrorist network mining:issues and challenges. International Journal of Advance Research in Science and Engineering, 2015, 4(1):33-37 http://d.old.wanfangdata.com.cn/NSTLQK/NSTL_QKJJ0211627901/ [39] 张将星. 1970-2013年全球恐怖主义活动的特征分析-兼论"9·11"事件前后时段比较.同济大学学报(社会科学版), 2016, 27(2):48-57 doi: 10.3969/j.issn.1009-3060.2016.02.008Zhang Jiang-Xing. An analysis of the features of global terrorist activities from 1970 to 2013-a comparison of those before and after Sept. 11. Journal of Tongji University (Social Science Section), 2016, 27(2):48-57 doi: 10.3969/j.issn.1009-3060.2016.02.008 -




 下载:
下载: